 IEEE/ICACT20220353 Slide.05
[Big Slide]
[YouTube]
IEEE/ICACT20220353 Slide.05
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 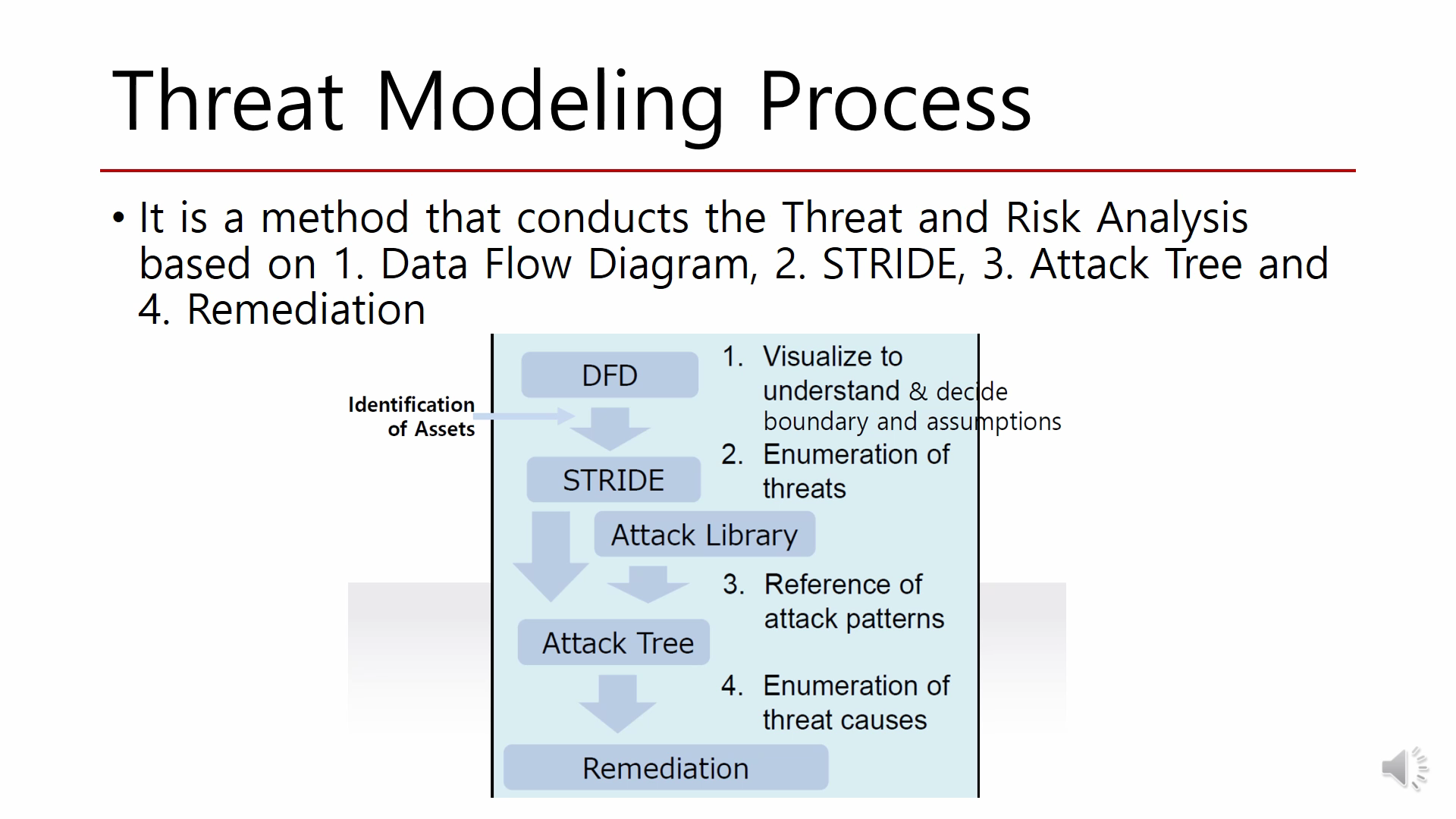
| Virual Oral Presentation Slide by Slide |
 IEEE/ICACT20220353 Slide.05
[Big Slide]
[YouTube]
IEEE/ICACT20220353 Slide.05
[Big Slide]
[YouTube] |
 Oral Presentation Oral Presentation |
|
 |
Threat Modeling Initiated usually with 5 processes. However, depending on the target system and the clientĄ¯s demand, it can modify the process step. The usual Treat Modeling steps are as follows, First, draw Data Flow Diagram is known as DFD Second, initiate STRIDE analysis. Third, Built the Attack Library, Fourth, Drawing an attack tree Fifth, come up with the Remediation plan. | |
| [Go to Next Slide] |