 |
From the background study, we can observe that several
efforts have been made in Cloud security by different
organizations or standard bodies, primarily CSA, ISO, and
individual cloud platform vendors. However, it is confusing
which standard to follow from a plethora of standards by
different organizations or else which platform to choose from
the available platforms in the market as each one has its own
metrics resulting in vendor lock-in. Each effort is in its own
direction with a common goal of ensuring cloud security
assurance. We need a holistic view of the security assurance
framework.
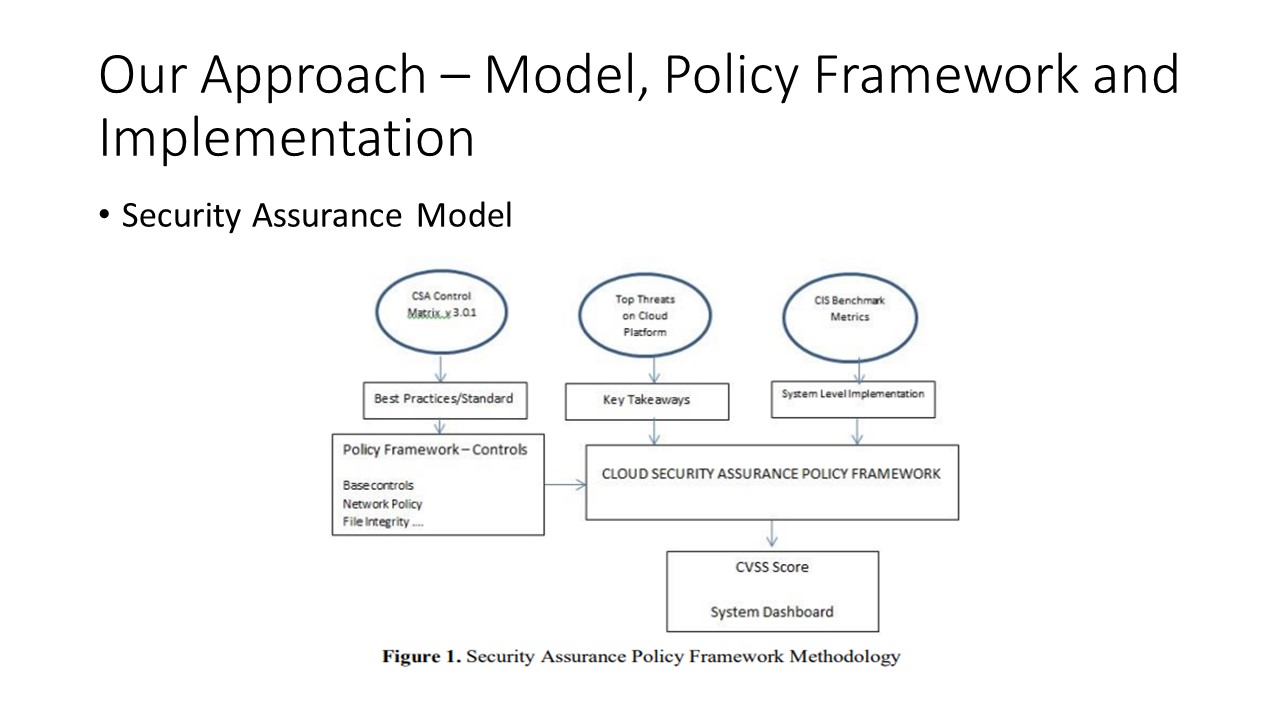
To fill this gap, we developed a security assurance policy
framework based on the model defined in Fig 1 here in this slide, and implemented monitoring of 14 controls as given in Table I in the next slide.
The list is not limited to these controls itself and can be
extended in the future. The controls are all relevant to the key
takeaways that were studied based on CSA Top Cloud Threats
and corresponding preventive mechanisms. These controls
have been implemented for continuous monitoring using
Centre for Internet Security benchmark metrics. These
controls have been mapped to different control domains of
CSA Control Matrix v 3.0.1 in order to present the compliance
w.r.t Cloud Control Matrix best practices. |
 IEEE/ICACT20230046 Slide.08
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.08
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20230046 Slide.08
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.08
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 