 |
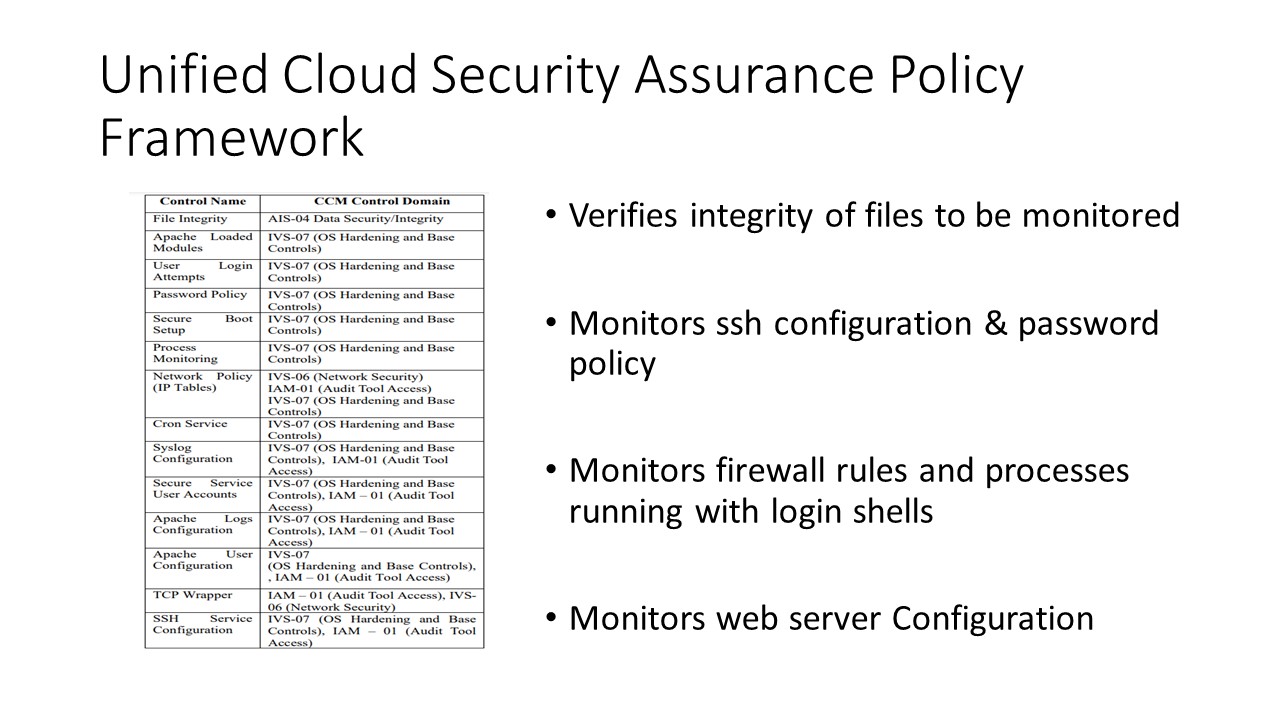
In table 1, column 1 represents the description of the control being monitored, and column 2 represents the Cloud Control Matrix
control domain to which the control name is mapped. When
monitoring of a control name is implemented based on CIS
benchmark metrics, its security threat perception can be
graded in accordance with the Common Vulnerability Scoring
System (CVSS) score. The combination of the control name, its
mapping to the control domain, and its CVSS score thus form
the security assessment policy framework from which the
overall compliance with all critical resources of the business entity can be ascertained. The CVSS score could be one of
None, Low, Medium, High or Critical.
The controls mentioned here are related to assessing resources capability w.r.t monitoring file system integrity, password policy verification, firewall rules, network processes that are running with login shell, improper ssh configuration etc. |
 IEEE/ICACT20230046 Slide.09
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.09
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20230046 Slide.09
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.09
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 