 |
In order to realize the effectiveness of the policy
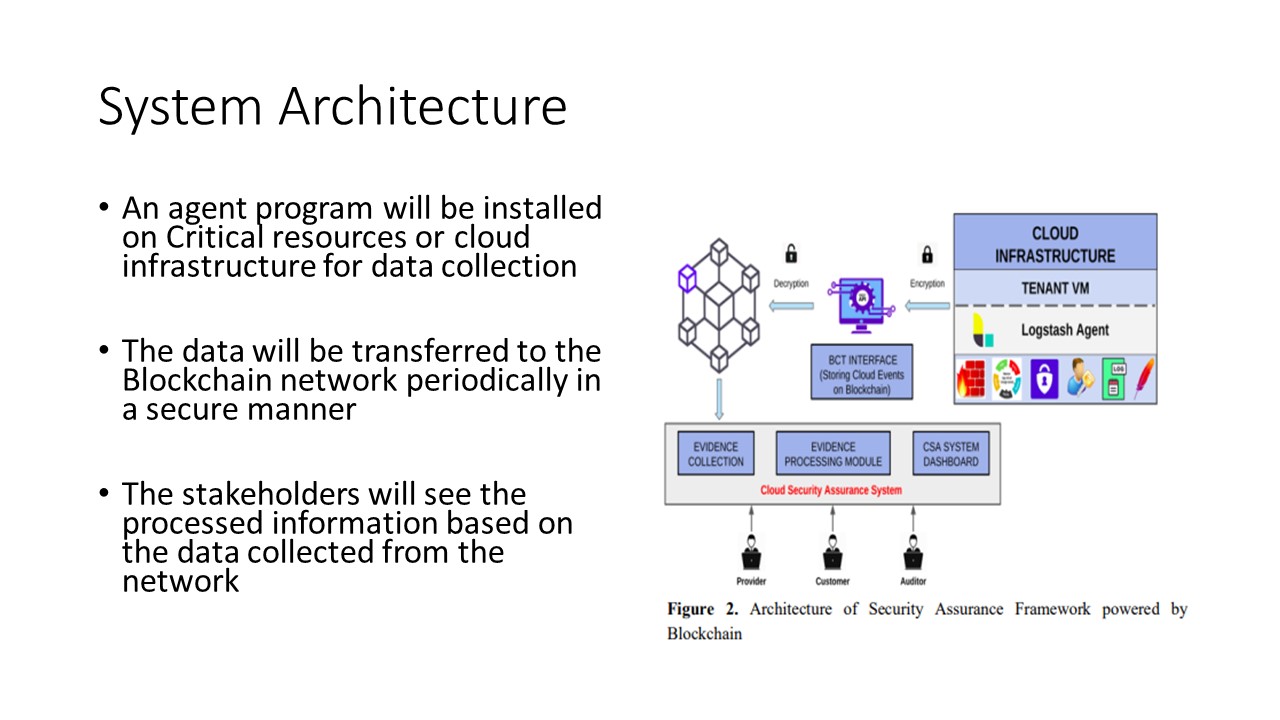
framework the policy has to be implemented as a software
module. Fig 2 here depicts the system architecture which
implements the proposed security policy framework using
Blockchain Technology.
We used Hyperledger Fabric (HLF) as a blockchain
platform. In each resource that is being monitored, there will
be an agent program running hereinafter called ¡®Agent¡¯. The
agent program reads the log contents from the respective resource
corresponding to each observable control as defined in table 1,
encapsulates the same in a JSON object format, and transfers
the same to the Blockchain platform.
During this process each resource that is being monitored encrypts the JSON object using its private key and the same will be sent to the HLF Blockchain node. The array containing error ids represents
events where policy violations have been detected. |
 IEEE/ICACT20230046 Slide.11
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.11
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20230046 Slide.11
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.11
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 