 IEEE/ICACT20230129 Slide.14
[Big Slide]
[YouTube]
IEEE/ICACT20230129 Slide.14
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 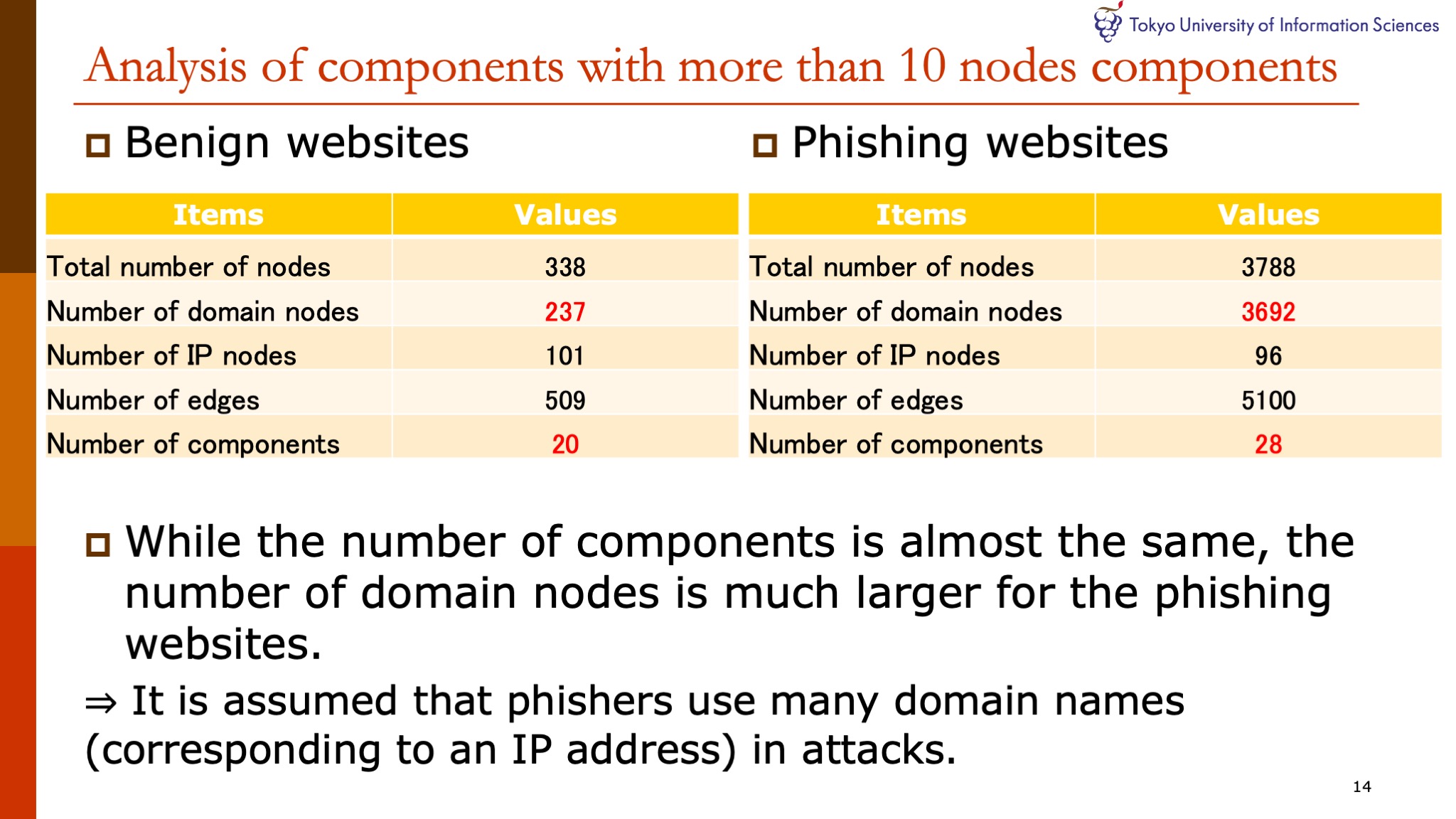
| Virual Oral Presentation Slide by Slide |
 IEEE/ICACT20230129 Slide.14
[Big Slide]
[YouTube]
IEEE/ICACT20230129 Slide.14
[Big Slide]
[YouTube] |
 Oral Presentation Oral Presentation |
|
 |
Next, we focus on components with 10 or more nodes of the DNS graphs of the benign and phishing websites and analyze them. These two tables are the results of extracting components with more than 10 nodes from DNS graphs of the benign and phishing websites. While the number of components is almost the same, the number of domain nodes is much larger for the phishing websites. These results, it is assumed phishers use many domain names that correspond to an IP address in attacks. | |
| [Go to Next Slide] |