 |
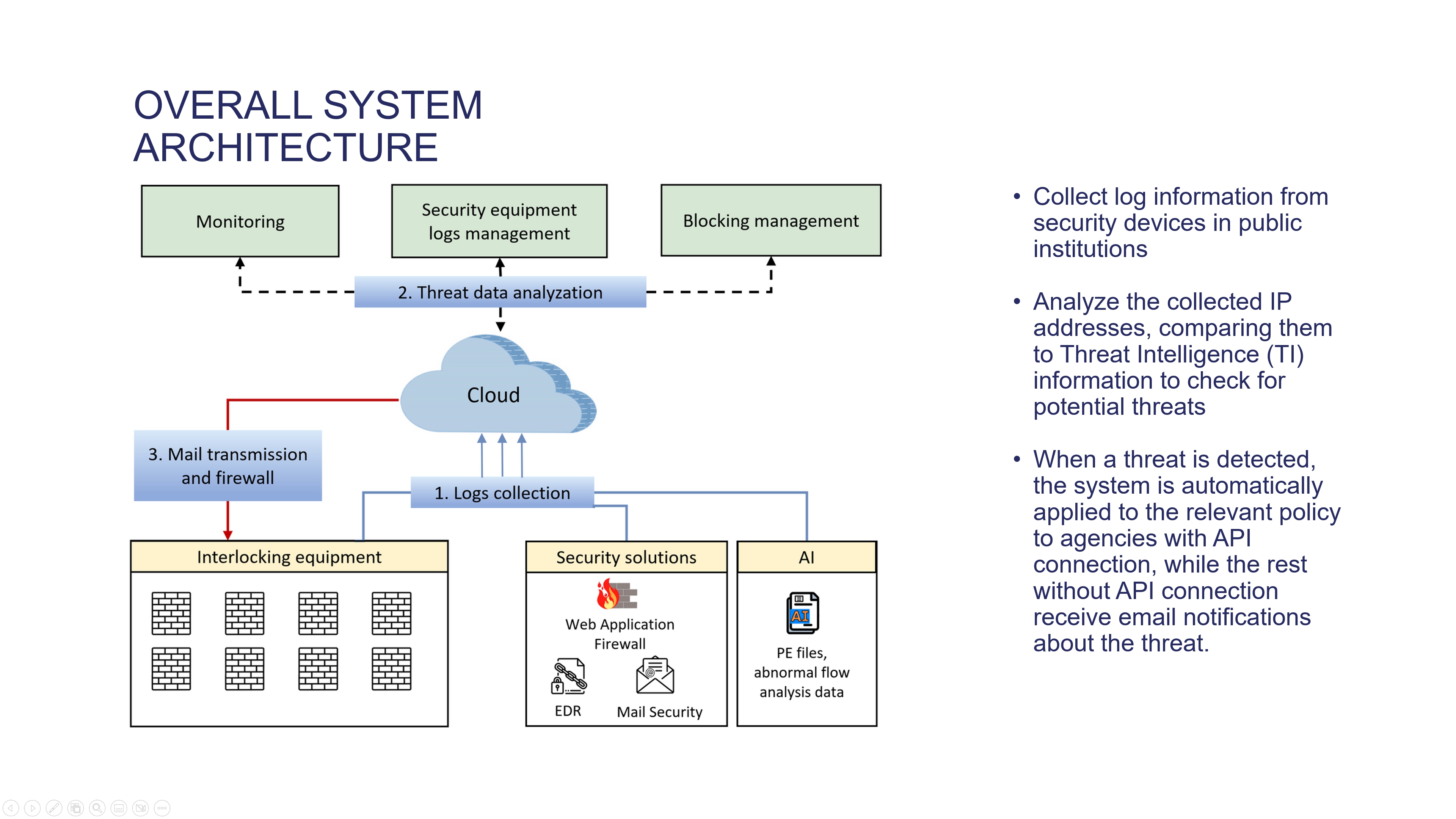
The core of our system revolves around a three-step process described in this figure. First, we collected log information from security devices in public institutions. Then, we analyzed the collected IP addresses, comparing them to Threat Intelligence (TI) information to check for potential threats. When a threat is detected, the system is automatically applied to the relevant policy to agencies with API connection, while the rest without API connection receive email notifications about the threat.
|
 IEEE/ICACT20240309 Slide.14
[Big Slide]
IEEE/ICACT20240309 Slide.14
[Big Slide]
 Oral Presentation
Oral Presentation 
 IEEE/ICACT20240309 Slide.14
[Big Slide]
IEEE/ICACT20240309 Slide.14
[Big Slide]
 Oral Presentation
Oral Presentation 