 |
We have implemented an ¡®Agent¡¯ code using ¡°logstash¡±
for each control that is described in the security policy
framework depicted in table 1. The log information
from each resource is routed through an intermediate gateway
developed using Node.JS server side program which acts as a
client to the HLF Blockchain network. The Node server upon
receiving the encrypted JSON object sends the same unaltered
to the Blockchain network. The smart contract later decrypts
the JSON Object and stores the same in the Blockchain
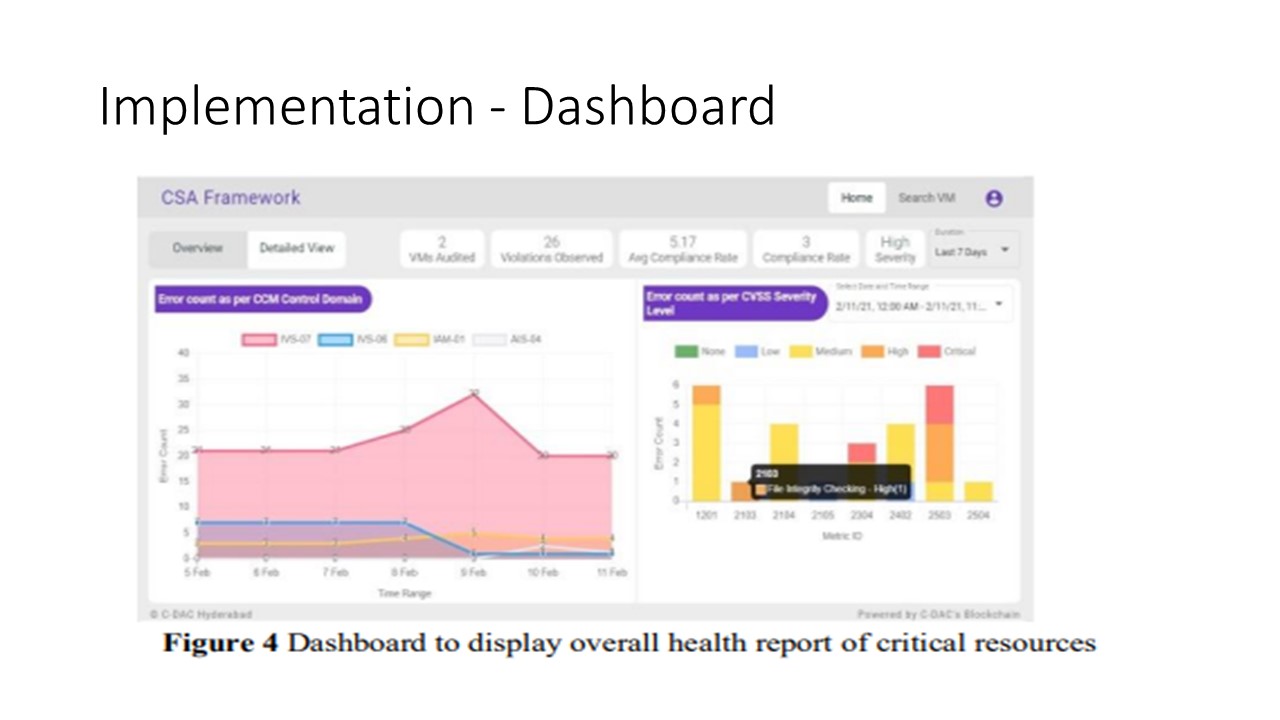
network. A Dashboard component also has
been developed using the Angular programming framework
which can be accessed from the web by end-users who are
members of service providers, customer, and auditor
organizations. The dashboard component displays the no of
violations against the security policy framework as described
in Table I in a graphical format. It also displays various
metrics such as no of resources audited in the platform, the
average compliance rate over a period of time (e.g., last 24hrs,
7 days, 30 days). The application also displays the detailed report of each vulnerability and its mitigation plan.
The CVSS computation of all the resources gives us a clue about the current health scenario of the resources being monitored. Hence, it can be regarded as a way for monitoring whether the policy compliance has any effect or not. |
 IEEE/ICACT20230046 Slide.16
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.16
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20230046 Slide.16
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.16
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 