 |
The software module i.e., the intermediate gateway in our overall architecture, used for retrieval of data from the Blockchain network and to verify security policy conformance, should be designed in such a manner that it can withstand the vast amount of data that is required to be processed and improve the system response time. It is observed that if logs are collected at 10min intervals in a day, a total of 144 iterations will be required to store the log information in the Blockchain platform. We observed that with 14 control data that are collected 144 times a day and each JSON object size of 594bytes on average, approximately a
total of 1.14MB of data would be stored from each resource
that is being monitored. For 30 days 34.27MB of data will
have to be processed corresponding to a particular resource.
After observing this, we designed the below data structure to
cope up with data generated by multiple resources. In our
experiment, we used nearly 8VMs for monitoring purposes and
improved the system response time. The end-user, upon
selecting the duration for which the analysis has to be
performed in the dashboard, data pertaining to that period will
be retrieved from the Blockchain network and maintained in
accordance with the below data structure.
{
metric_id: val # id of the control name
result: [error1, error2, error3, error4 íŽ.] #stores id of
every error that is observed
timestamp: [ts1, ts2, ts3 íŽ.] #stores timestamps at
which the errors have been observed
machine_id: xxxx #id of the resource
hostname: val #name of the host
}
By default, the data collection interval is set to 10min in
our approach. In this format instead of processing individual
JSON objects representing each log entry, we rearranged
similar entries based on the time of their occurrence while
responding to the request from the dashboard component. This
has enhanced the system response time considerably.
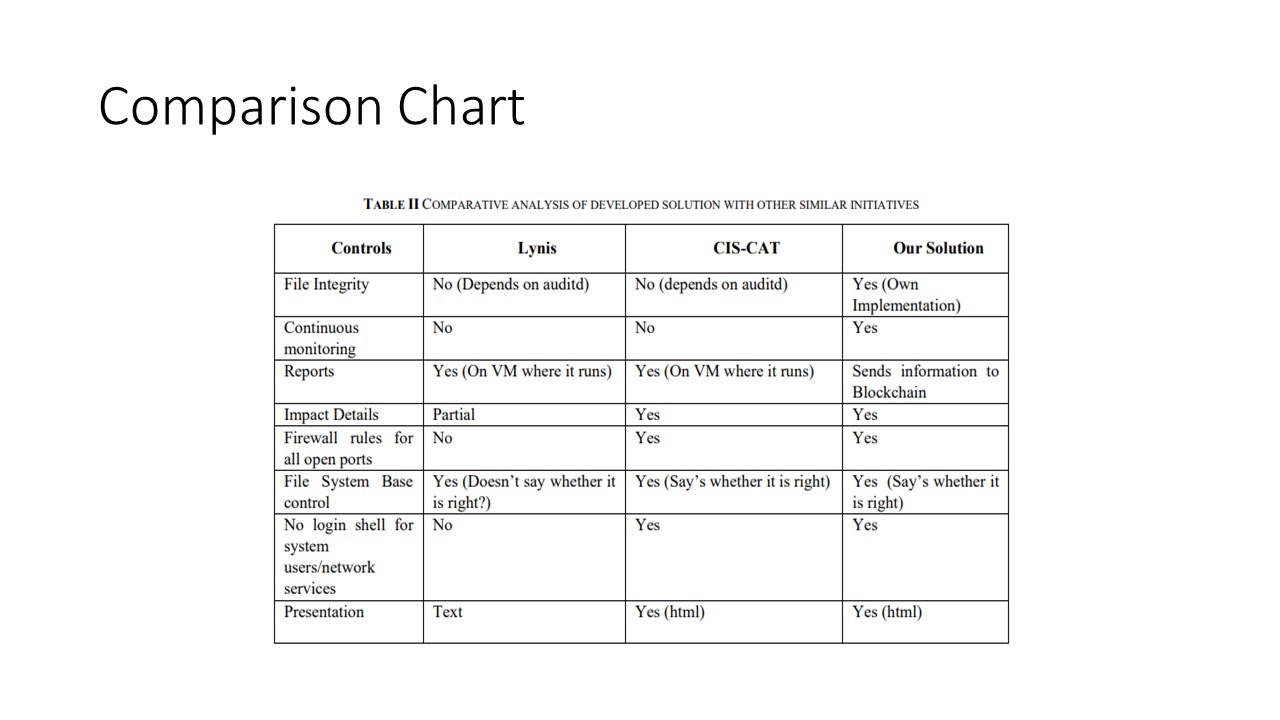
Table II in this slide depicts the comparative analysis of
developed solutions with different security analysis tools.
Other tools given in Table II have certain shortcomings when
compared to our solution as both of them generate a report in
the system in which those tools are deployed. We used
freeware versions. Whereas our solution provides a web
interface to view the health report of all resources being
monitored in one place. Moreover, we also have the CVSS
score that displays the severity level to alert the concerned
stakeholders. Another important feature of the developed
solution is that it automatically collects data at regular
intervals and sends them to the Blockchain platform for
permanent storage in a tamper-evident manner. This way, we
have designed and implemented a unified security policy
framework with 24x7 monitoring and alert system. |
 IEEE/ICACT20230046 Slide.17
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.17
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20230046 Slide.17
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.17
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 