 ICACT20210126 Slide.18
[Big slide for presentation]
ICACT20210126 Slide.18
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
This paper proposes a new approach for detecting and preventing ARP spoofing attacks in the LAN environment. In the proposed system, MITM attack over SSL has been implemented, detected using Wireshark and C programming, and finally prevented using DHCP snooping and dynamic ARP inspection. This approach helps to ensure that enterprises run effectively and efficiently by creating reliability and security for network solidity.
|
 ICACT20210126 Slide.17
[Big slide for presentation]
ICACT20210126 Slide.17
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
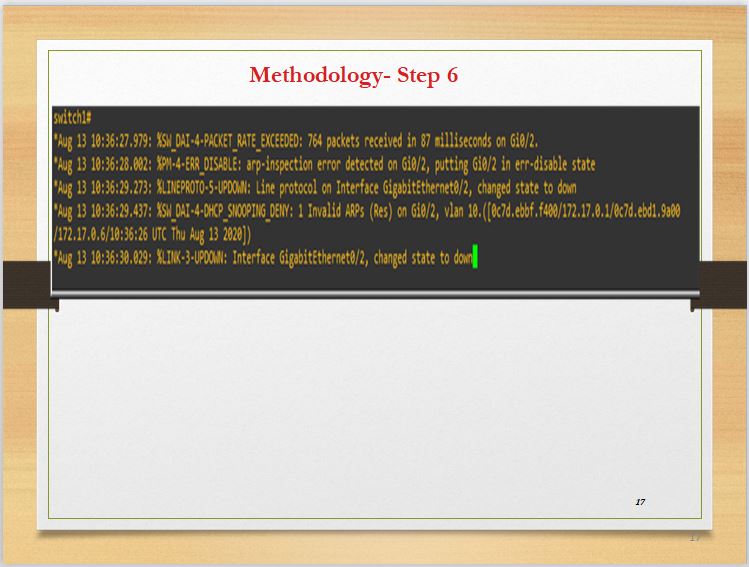 |
In slide 17, ARP inspection error is detected on interface Gi0/2, this is because any of the conditions in algorithm 6 has been met and as a result, the interface has been shut down and can no longer send packets in the network.
|
 ICACT20210126 Slide.16
[Big slide for presentation]
ICACT20210126 Slide.16
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
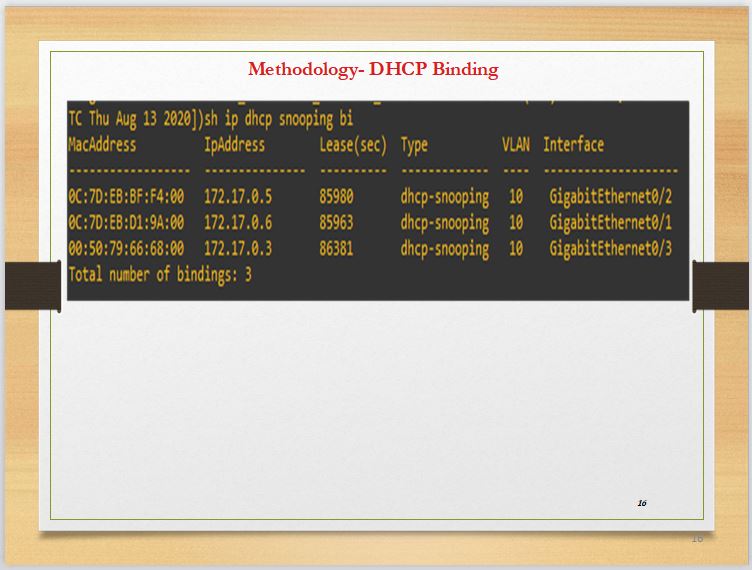 |
Slide 16 shows a table for the DHCP binding. This binding is needed to prevent packet dropping from all hosts whose details are in the table except when they exceed the transfer rate that is 10 rates per second.
|
 ICACT20210126 Slide.15
[Big slide for presentation]
ICACT20210126 Slide.15
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
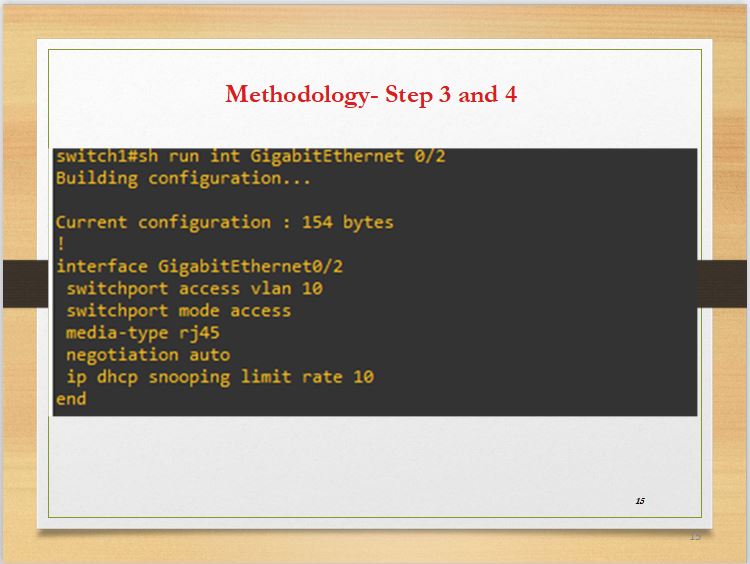 |
In slide 15, the transfer rate from the interface that isn¡¯t trusted is set to 10 frames per second. That means, once the rate exceeds 10, it will shut down. This is because only when suspicious activity is going on can there be a transfer of more than 10 rates in a second. At this point, ARP inspection is enabled.
|
 ICACT20210126 Slide.14
[Big slide for presentation]
ICACT20210126 Slide.14
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
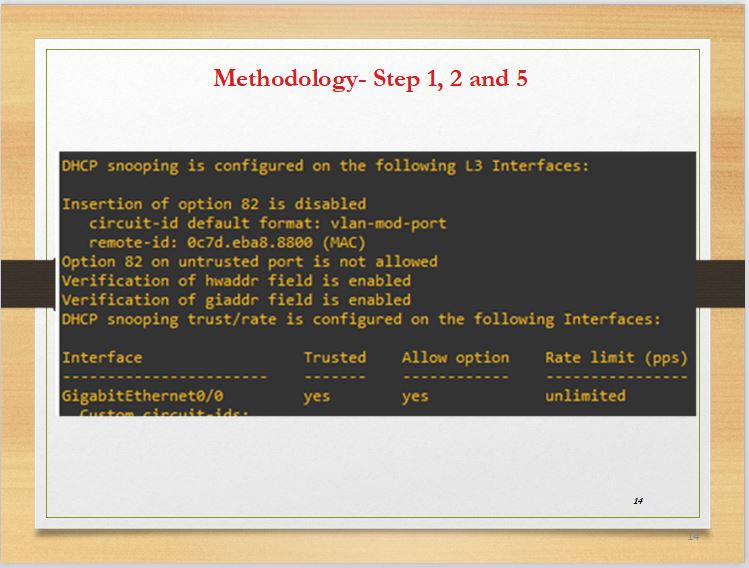 |
Slide 14 shows the result of enabling DHCP snooping in step 1 and all trusted port configuration in step 2 and 5.DHCP snooping is a layer two feature that implements better security in an Ethernet switch environment by allowing its users to create both trusted and untrusted ports.The port for the gateway Gigabit Ethernet (Gi0/0) has been configured to be trusted by DHCP snooping. Trusted ports receive DHCP responses and are not monitored whereas untrusted ports are monitored for any suspicious activities.This prevents rogues DHCP servers from creating fake DHCP offers to clients.
|
 ICACT20210126 Slide.13
[Big slide for presentation]
ICACT20210126 Slide.13
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
In slide 13, the algorithms for the prevention of the attack are concisely explained.
|
 ICACT20210126 Slide.12
[Big slide for presentation]
ICACT20210126 Slide.12
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
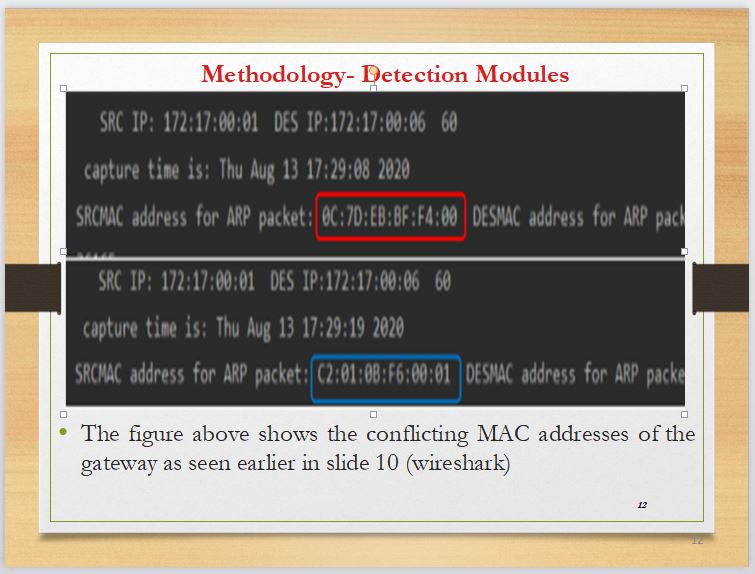 |
In Slide 12, Gateway MAC that is conflicting due to the ARP spoofing ongoing in the network has been filtered.
|
 ICACT20210126 Slide.11
[Big slide for presentation]
ICACT20210126 Slide.11
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
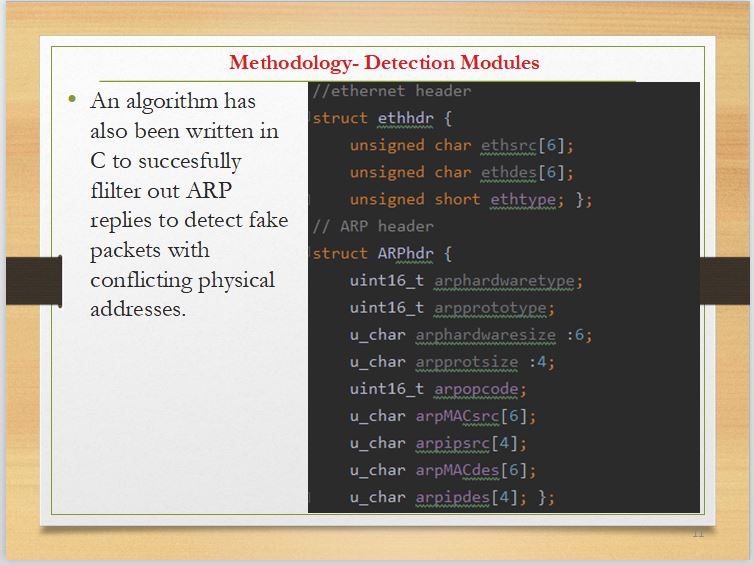 |
Slide 11 shows the header of the Algorithm used in C to detect the attack. It consists of the ethernet and the ARP header.
|
 ICACT20210126 Slide.10
[Big slide for presentation]
ICACT20210126 Slide.10
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
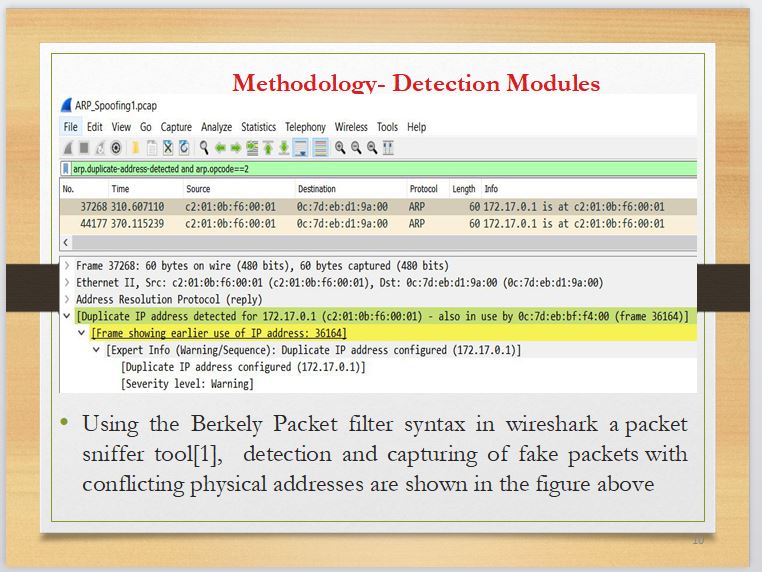 |
Wireshark is a packet sniffer tool developed by Gerald Combs in 1988 to analyze and troubleshoot computer networks. In the expert information area of wireshark, we filter only ARP reply protocols with duplicate addresses with the Berkeley Packet Filter (BPF) syntax ¡°arp.duplicate-address-detected and arp.opcode==2¡± which only filters ARP replies that have duplicate addresses.
|
 ICACT20210126 Slide.09
[Big slide for presentation]
ICACT20210126 Slide.09
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
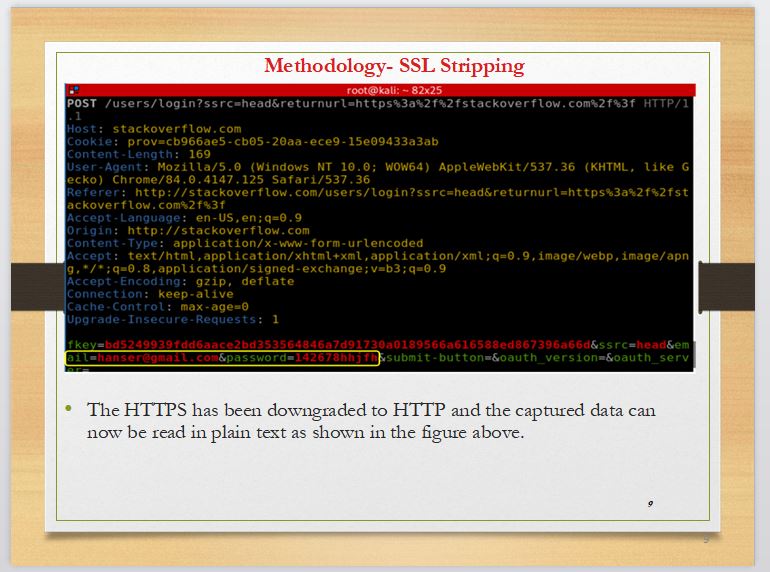 |
It can be seen in slide 9 that the data entered on stack overflow is not encrypted as it is supposed to. Because of the downgrade, the mail address and the password entered here is in readable text.
|
 ICACT20210126 Slide.08
[Big slide for presentation]
ICACT20210126 Slide.08
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
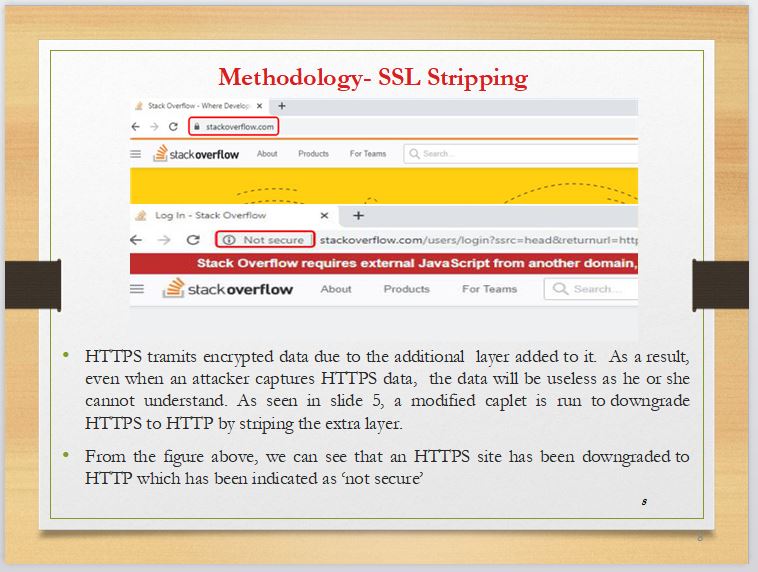 |
HTTP with an extra secured layer added to it becomes HTTPS. The function of this extra layer is to encrypt the plain data that HTTP sends so that, even if an attacker becomes a man-in-the-middle, the data over HTTPS becomes gibberish. This HTTPS that transmits encrypted data due to the additional security layer added has been downgraded to HTTP. Stack overflow that uses HTTPS has been used for demonstration. After the downgrade, one can see that the padlock sign is no longer there, and instead ¡°not secure¡± is shown. This indicates that the site is no longer encrypted.
|
 ICACT20210126 Slide.07
[Big slide for presentation]
ICACT20210126 Slide.07
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
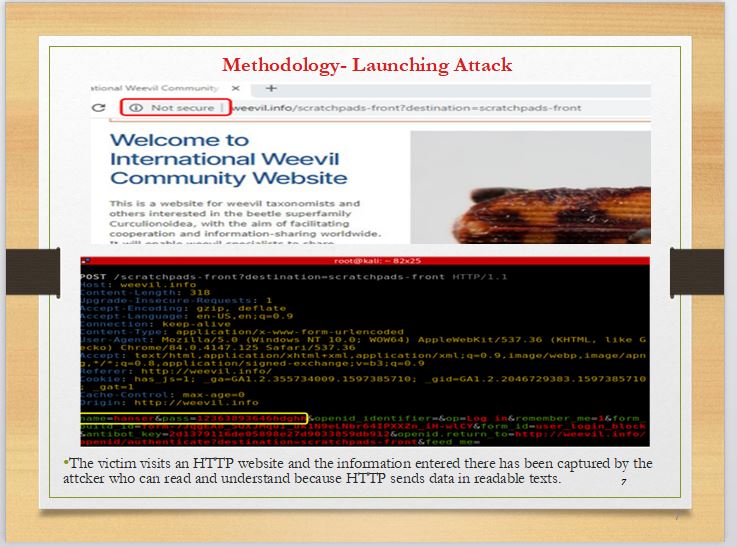 |
The victim visits an HTTP site (Hypertext Transfer Protocol). Hypertext transfer protocol commonly known as HTTP is a communication protocol in the upper layer of the open system interconnection (OSI) model used for communication between a web-server and a browser. Because HTTP sends data in readable texts, the username and password entered on the site by the victim machine has been captured by the attacker.
|
 ICACT20210126 Slide.06
[Big slide for presentation]
ICACT20210126 Slide.06
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
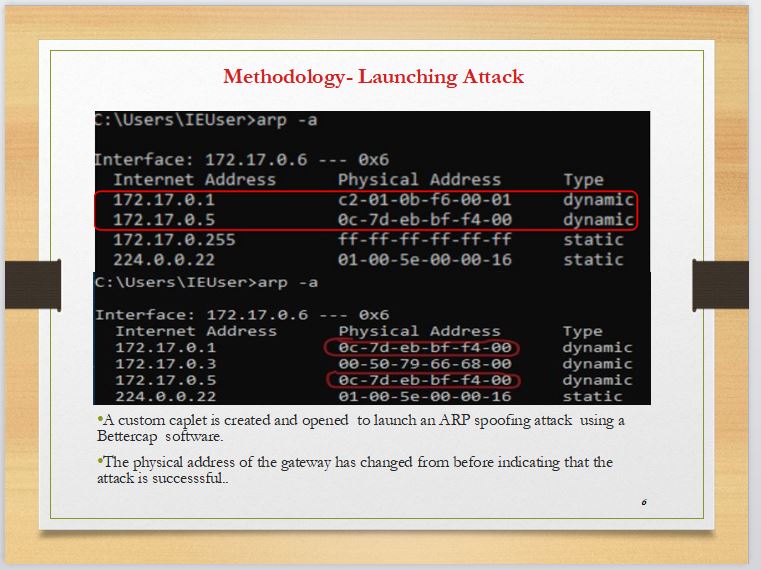 |
In slide 6, An attack is launched from the kali machine using bettercap on interface eth0. The MAC address of the gateway and the kali were different before the attack. After performing the ARP spoofing, the kali machine that is the attacker has successfully become the man in the middle and is now having the same MAC address as the gateway. This happens so that the victim machine sends data to the attacker thinking that the attacker is the gateway.
|
 ICACT20210126 Slide.05
[Big slide for presentation]
ICACT20210126 Slide.05
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
The detailed list of components for the experimental network is shown
here.
|
 ICACT20210126 Slide.04
[Big slide for presentation]
ICACT20210126 Slide.04
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
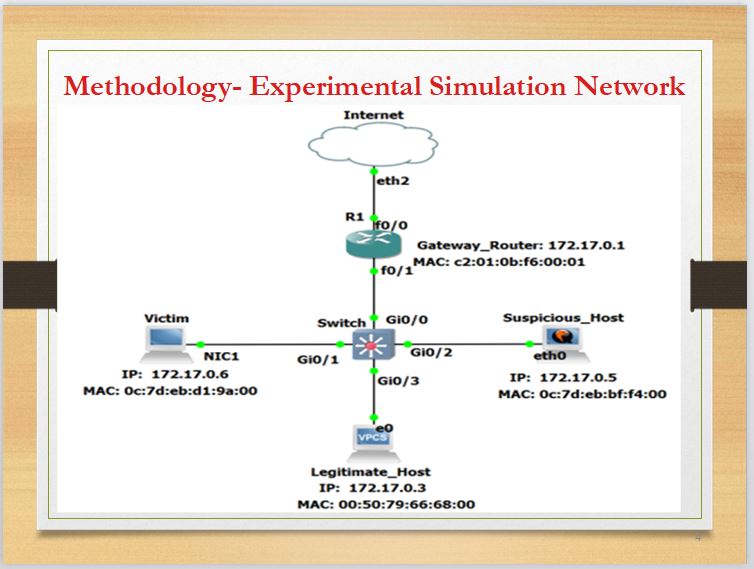 |
Side 4 shows the virtual LAN network that has been set up using GNS3 Graphical User Interface, VMware workstation, cisco ethernet two-layer switch, ethernet three router, Kali Linux as the attacker, and windows as the victim.
|
 ICACT20210126 Slide.03
[Big slide for presentation]
ICACT20210126 Slide.03
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
The objective of this research work is to present a comprehensive experimental approach that explains in detail how to launch, detect, and prevent an ARP attack in a Local Area Network (LAN)
|
 ICACT20210126 Slide.02
[Big slide for presentation]
ICACT20210126 Slide.02
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
The outline of the work consists of the objectives, methodology that includes the experimental simulation where the attack has been launched, detected and prevented, and finally the conclusion of the work.
|
 ICACT20210126 Slide.01
[Big slide for presentation]
ICACT20210126 Slide.01
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
Hi everyone, Hannah Adjei is my name . For ICACT 2021 i am presenting on a solution for address resolution protocol spoofing (ARP) in a local area network(LAN) with corresponding authors: Associate Professor Tan Shunhua, Yangyang Li, George Agordzo, Peprah Gregory and Gyarteng Emmanuel.
|






