 ICACT20230046 Slide.00
[Big Slide] ICACT20230046 Slide.00
[Big Slide]
|
Chrome  Click!! Click!! |
 |
Please skip this slide. |
 ICACT20230046 Slide.01
[Big Slide]
[YouTube] ICACT20230046 Slide.01
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Good Morning. I am going to present about Blockchain-based Security Information and Event Monitoring Framework. |
 ICACT20230046 Slide.02
[Big Slide]
[YouTube] ICACT20230046 Slide.02
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Security Information and Event Monitoring (SIEM)
tools collect log data which helps organizations to plan appropriate security assessment and reconciliation strategies. Root cause analysis of security risks needs data provenance capabilities. Blockchain Technology augments SIEM tools with data
provenance capability so that an effective security framework can
be built for organizations. In this paper, we describe a unified and comprehensive security assurance framework that supports a
tamper-proof, time-stamped, and distributed storage repository to
ensure data provenance and is useful in security assessment in
compliance with the cloud control matrix of CSA. This framework can be used in a Cloud environment also by adding additional security log data collection points. |
 ICACT20230046 Slide.03
[Big Slide]
[YouTube] ICACT20230046 Slide.03
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Continuous monitoring of critical resources of an organization is essential in today's digital world where cyber-attacks are possible from anywhere anytime irrespective of geographical location. It would be prudent to have the critical resources well protected with system-hardening techniques instead of leaving them with default settings during installation or commissioning time. In order to ensure this, a continuous auditing process must be in place that is robust and well-maintained without leaving room for any data integrity loss. One such technology that can support this is Blockchain Technology which when coupled with data analytics can be proven to be more effective solution. In the case of system information event monitoring this technology would be beneficial as it supports data provenance that is maintained in a tamper-proof manner across different geographical locations making it harder to break such a system. The technology provides a unique state replication of data that is harder to break because of its inherent architectural design and consensus mechanism. |
 ICACT20230046 Slide.04
[Big Slide]
[YouTube] ICACT20230046 Slide.04
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
SIEM tools produce reports instantaneously when they run in a
machine. For a detailed analysis of security assessment history
of events and related data need to be captured in a manner
such that the data integrity is maintained forever. Hence, we
need a technology that maintains data provenance in a tamperproof and time-stamped manner so that the security framework is assured of data integrity at any time. Moreover, such a provision will help SIEM tools to produce more effective reports when data analytics components are integrated for fine-grained analysis. Apart from the above, there should be a mechanism using which one can see to what extent the underlying security policy is conformant and its current severity level to indicate a perceived threat.
If unique state replication of data provenance is ensured at
the premises of the service provider and other stakeholders
then compliance with the organization¡¯s security policy framework can be provided as a Software Service with continuous monitoring capabilities in a decentralized manner.
Blockchain is a technology that provides, Consensus-based unique state replication across multiple nodes, a tamper-proof storage of data for ensuring data integrity and data provenance along with secured and authentic transaction capability when deployed as a permissioned network.
Integrating Blockchain capabilities and SIEM features into a solution makes the security assurance systems a robust and effective mechanism to safeguard the organization¡¯s interest. |
 ICACT20230046 Slide.05
[Big Slide]
[YouTube] ICACT20230046 Slide.05
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Blockchain Technology is a distributed ledger technology
that ensures unique state replication across the participating
nodes in a tamper-proof and time-stamped manner. The data
once stored cannot be modified or deleted. This is because
data will be stored in the form of a block whose header
contains a hash of the previous block and so on. The same
process of appending a new block to the existing chain of
blocks in each of the participating nodes will be ensured by
the consensus algorithms in the Blockchain network. Hence,
to modify data in the Blockchain network, an attacker not only has
to recompute the hash of the corresponding block but also
the hash of the next blocks up to the end block. And this entire
effort has to be replicated in each and every participating node
of the Blockchain network. Considering the effort required to
modify the data in the Blockchain network we can be assured
of the security and integrity of the data that is stored in the
Blockchain network.
To the best of our knowledge, a unified approach where evidence collection in a tamper-proof and time-stamped manner and maintenance of the same based on consensus among its stakeholders in a distributed storage system on one side and presenting the standards conformance along with perceived severity level in the whole system on another side is not present. We addressed this problem in our paper. |
 ICACT20230046 Slide.06
[Big Slide]
[YouTube] ICACT20230046 Slide.06
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
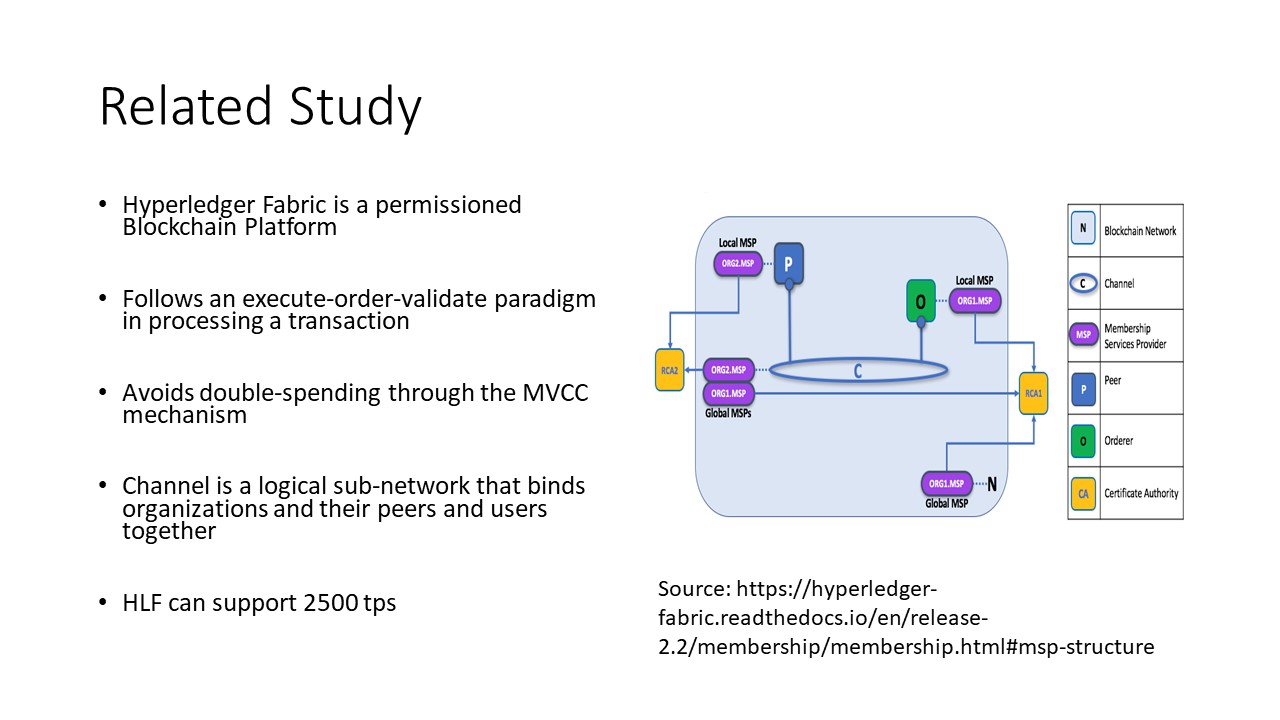 |
We have examined different Blockchain platforms and felt that Hyperledger Fabric is one platform that suits the requirement of not only maintaining data in a tamper-proof manner but also assist stakeholders in accessing the information from different geographical locations because of its decentralized architectural design pattern. Researchers are claiming HLF has the capability of processing up to 2500 transactions per second with certain optimizations this can be improved even further. The HLF separates out a consortium of participating members into a logical group by binding them through a logical subnetwork called 'channel'. This design consideration makes it apt for offering the security monitoring service as a service. |
 ICACT20230046 Slide.07
[Big Slide]
[YouTube] ICACT20230046 Slide.07
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Cloud security alliance has released cloud control matrix which is a cyber-security control framework for cloud computing, composed of 133 control objectives that are structured in 16 domains. It can be used as a guide to determine which security controls should be implemented by which actor for the systematic assessment of a cloud implementation. The controls in the CCM are mapped against industry-accepted security standards, regulations, and control frameworks including but not limited to: ISO 27001/27002/27017/27018, NIST SP 800-53, AICPA TSC, ENISA Information Assurance Framework, German BSI C5, PCI DSS, ISACA COBIT, NERC CIP, and many others. The control matrix defines various protective/defensive metrics that can be used for safeguarding various threats that are discussed in the Top 10 Cloud Threats that are frequently observed in the digital world. There are various tools such as Cloud Watch from Amazon, Lynis, CIS-CAT etc., that can be used to monitor the critical resources of an organization. However, in such initiatives, it is observed that the focus was mainly on providing the ability to audit or privacy protection of cloud data objects or related operations of a cloud platform whereas in our approach the emphasis was more on using the data provenance capability of the underlying blockchain network for security analysis. |
 ICACT20230046 Slide.08
[Big Slide]
[YouTube] ICACT20230046 Slide.08
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
From the background study, we can observe that several
efforts have been made in Cloud security by different
organizations or standard bodies, primarily CSA, ISO, and
individual cloud platform vendors. However, it is confusing
which standard to follow from a plethora of standards by
different organizations or else which platform to choose from
the available platforms in the market as each one has its own
metrics resulting in vendor lock-in. Each effort is in its own
direction with a common goal of ensuring cloud security
assurance. We need a holistic view of the security assurance
framework.
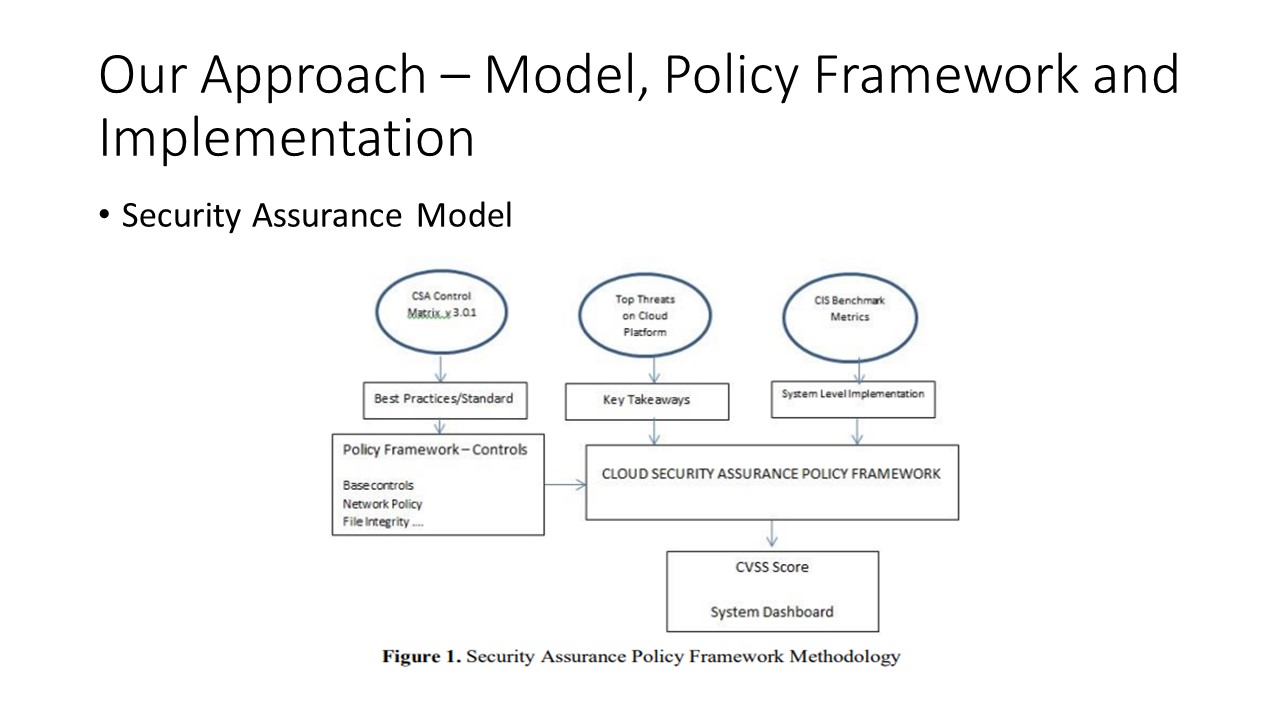
To fill this gap, we developed a security assurance policy
framework based on the model defined in Fig 1 here in this slide, and implemented monitoring of 14 controls as given in Table I in the next slide.
The list is not limited to these controls itself and can be
extended in the future. The controls are all relevant to the key
takeaways that were studied based on CSA Top Cloud Threats
and corresponding preventive mechanisms. These controls
have been implemented for continuous monitoring using
Centre for Internet Security benchmark metrics. These
controls have been mapped to different control domains of
CSA Control Matrix v 3.0.1 in order to present the compliance
w.r.t Cloud Control Matrix best practices. |
 ICACT20230046 Slide.09
[Big Slide]
[YouTube] ICACT20230046 Slide.09
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
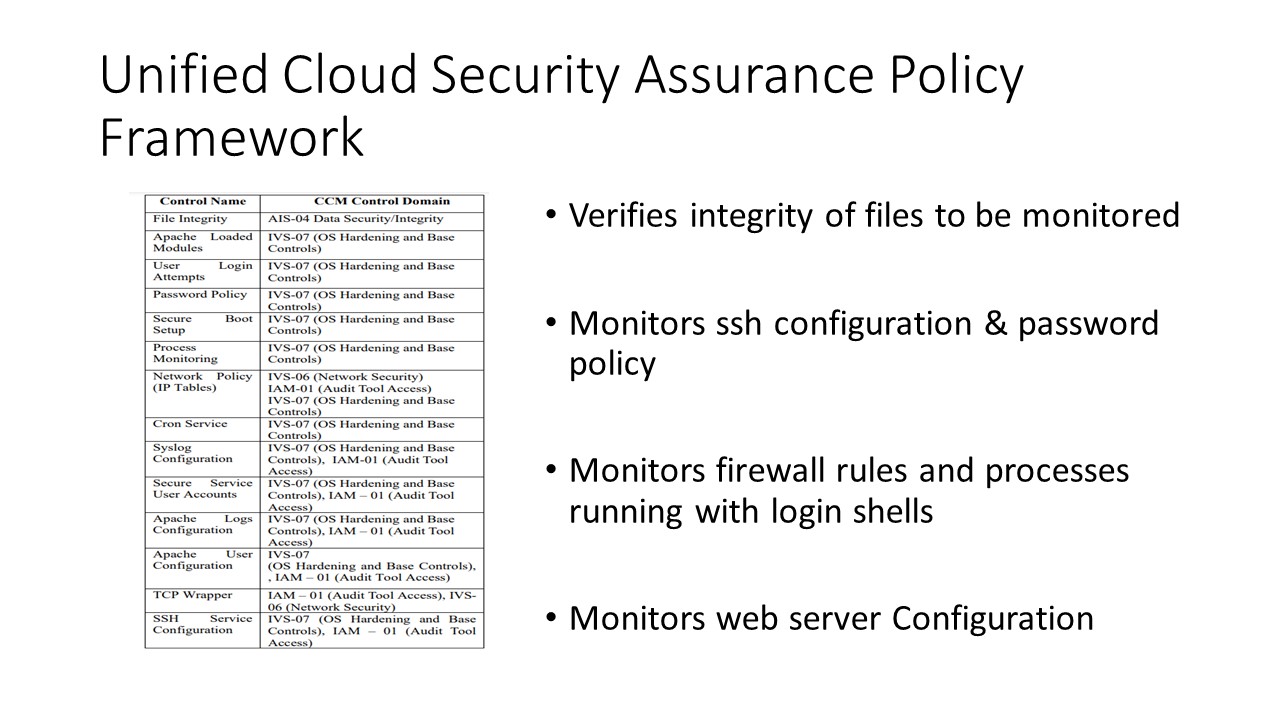 |
In table 1, column 1 represents the description of the control being monitored, and column 2 represents the Cloud Control Matrix
control domain to which the control name is mapped. When
monitoring of a control name is implemented based on CIS
benchmark metrics, its security threat perception can be
graded in accordance with the Common Vulnerability Scoring
System (CVSS) score. The combination of the control name, its
mapping to the control domain, and its CVSS score thus form
the security assessment policy framework from which the
overall compliance with all critical resources of the business entity can be ascertained. The CVSS score could be one of
None, Low, Medium, High or Critical.
The controls mentioned here are related to assessing resources capability w.r.t monitoring file system integrity, password policy verification, firewall rules, network processes that are running with login shell, improper ssh configuration etc. |
 ICACT20230046 Slide.10
[Big Slide]
[YouTube] ICACT20230046 Slide.10
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
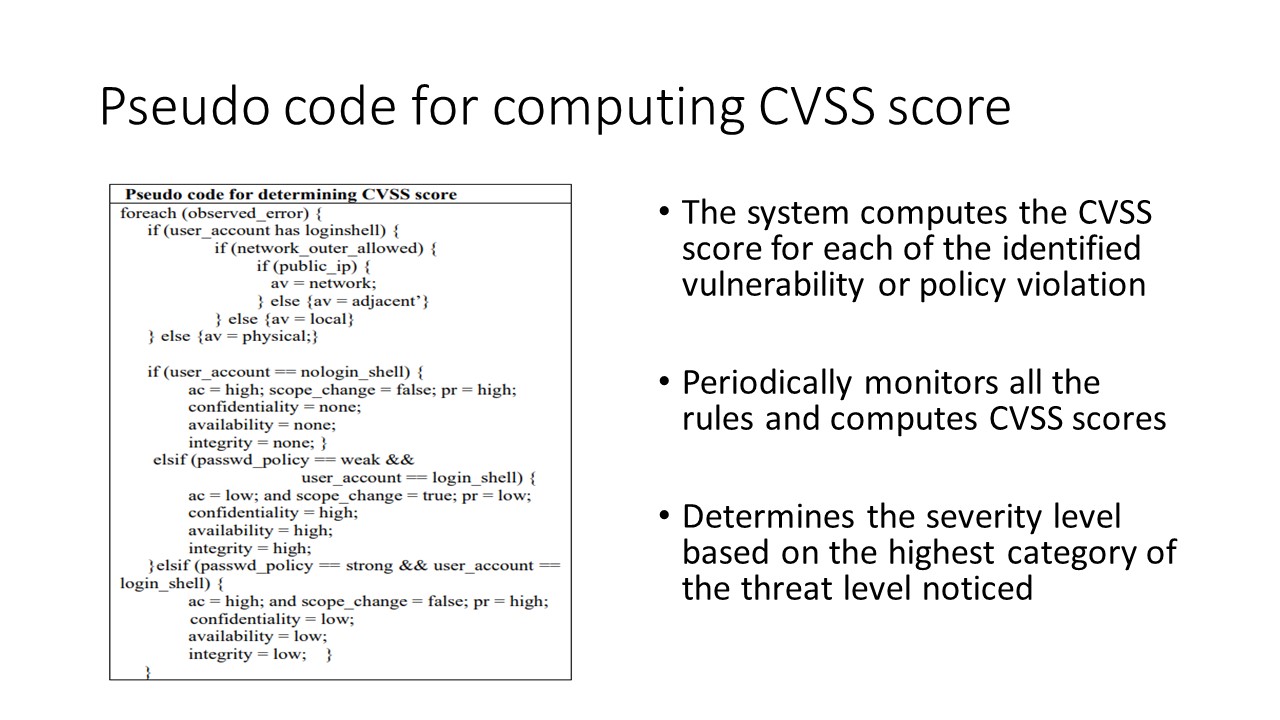 |
The CVSS score for each policy rule can be obtained based on the pseudo-code shown in this slide. Implementation of each control name may have a dependence on the occurrence of more than one event associated with it. For example, Process monitoring control
compliance would be verified based on various events such as
(a) Whether a process is system-oriented or network-oriented,
(b) if it is network oriented whether access restrictions are
present in the network policy or not (c) whether the log
information corresponding to the process has appropriate
access permissions or not (d) if it is network oriented whether
the process owner has ¡°nologin¡± shell or not. For each event,
the CVSS score would be computed and the highest severity
level among all the events that correspond to a control name
would become that control¡¯s severity level.
This model gives three important dimensions from which
the security assessment of the business entity can be ascertained.
Security Threat Perception of a critical resource being
monitored. (2) Strength/Weakness of the critical resource in a
particular domain in a particular control domain in accordance
with the CCM. (3) Overall compliance with the security
assessment policy framework of the business entity
considering all the critical resources.
|
 ICACT20230046 Slide.11
[Big Slide]
[YouTube] ICACT20230046 Slide.11
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
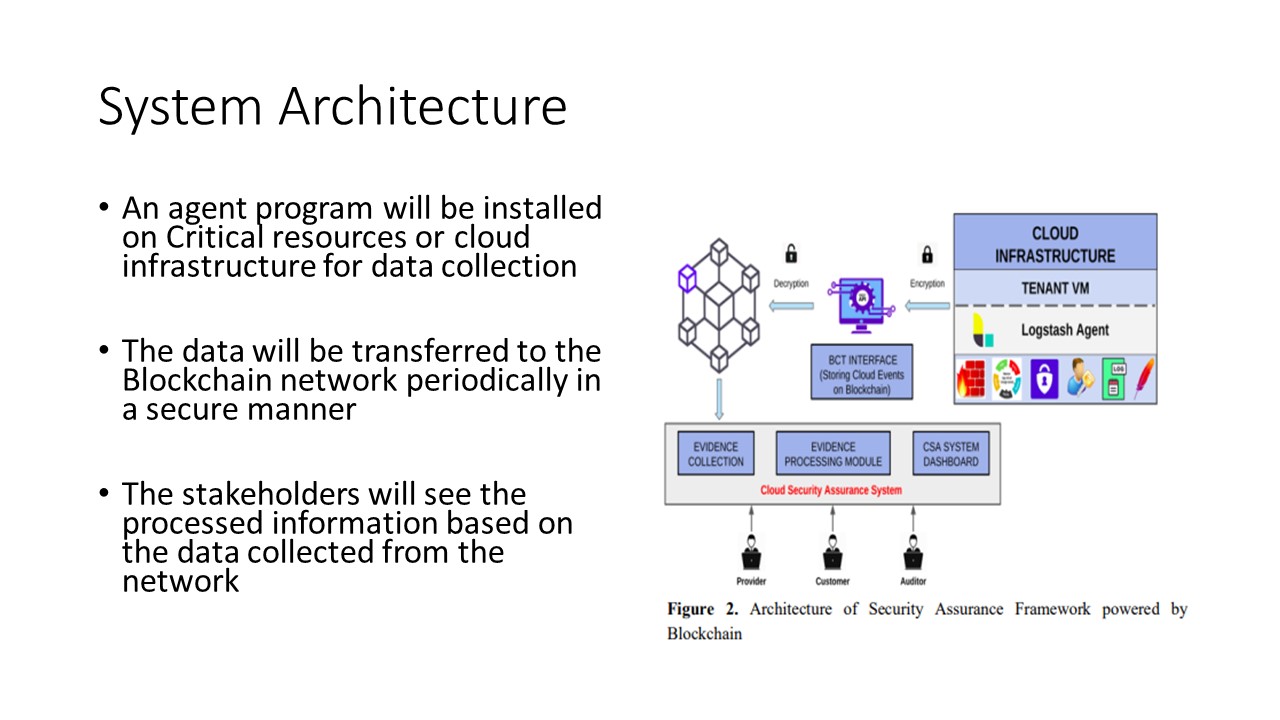 |
In order to realize the effectiveness of the policy
framework the policy has to be implemented as a software
module. Fig 2 here depicts the system architecture which
implements the proposed security policy framework using
Blockchain Technology.
We used Hyperledger Fabric (HLF) as a blockchain
platform. In each resource that is being monitored, there will
be an agent program running hereinafter called ¡®Agent¡¯. The
agent program reads the log contents from the respective resource
corresponding to each observable control as defined in table 1,
encapsulates the same in a JSON object format, and transfers
the same to the Blockchain platform.
During this process each resource that is being monitored encrypts the JSON object using its private key and the same will be sent to the HLF Blockchain node. The array containing error ids represents
events where policy violations have been detected. |
 ICACT20230046 Slide.12
[Big Slide]
[YouTube] ICACT20230046 Slide.12
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
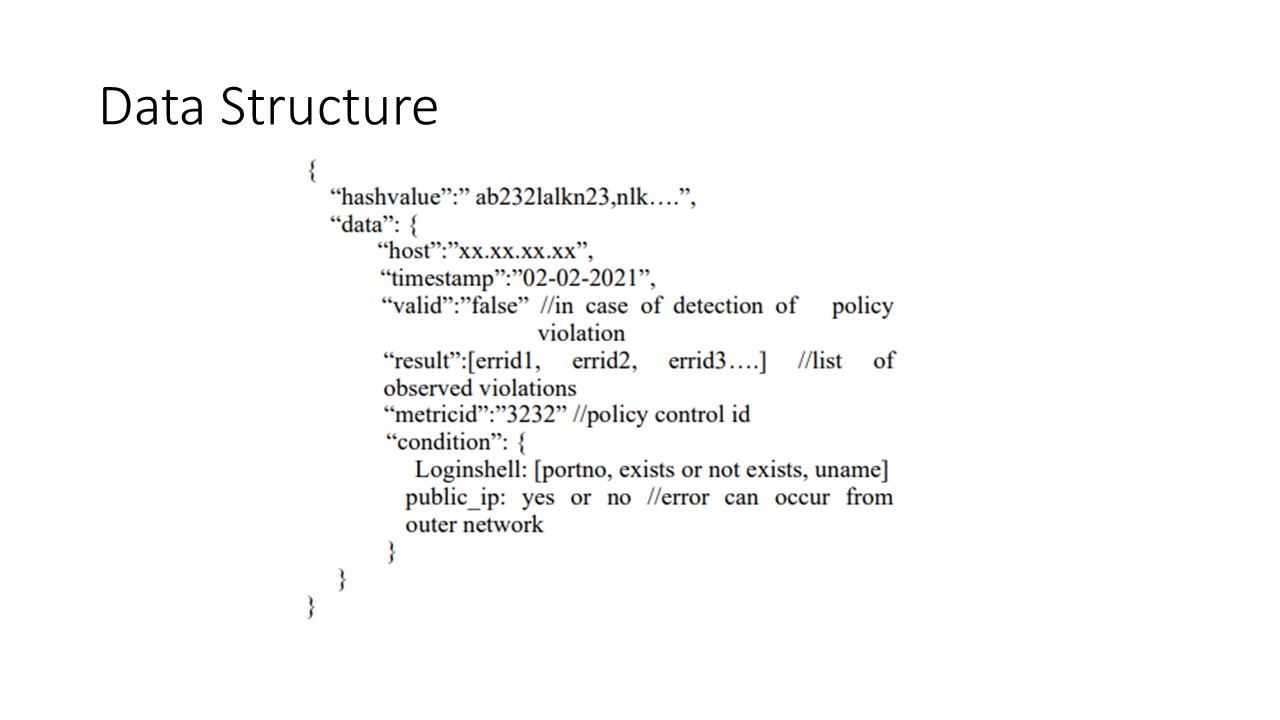 |
The JSON object format to be stored in the Blockchain is shown here. The array containing error ids represents events where policy violations have been detected. A hash value of all the fields in the JSON object is computed and is also made part of the JSON object. This is useful for data validation upon receipt by the Blockchain node. The condition field is useful during the computation of the CVSS score. Blockchain node upon receiving the JSON object would decrypt the received JSON object using the resource public key and recalculates the hash of all the fields in the JSON object and verify its integrity. Modified JSON objects would be rejected and will not be stored in the Blockchain node.
Since all blockchain nodes apply the same validation process it is ensured that all nodes will eventually maintain the same state only. The consensus algorithms of the Blockchain network ensure that the state is replicated across all the nodes uniformly.
|
 ICACT20230046 Slide.13
[Big Slide]
[YouTube] ICACT20230046 Slide.13
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
The advantages of using Blockchain in this architecture are
(a) The security policy-relevant information collected from
each resource gets replicated in all the Blockchain nodes in a
tamper-proof and time-stamped manner based on the
underlying consensus mechanism (b) Reduces log processing
load on the resource being monitored by delegating the data
processing to the Blockchain platform. (c) Due to consensus
based unique state representation of data across all Blockchain
nodes, all stakeholders viz. service providers, consumers and
auditors of a business entity would see the same data
provenance or its analysis report at any given time without
loss of generality.
ess/retrieve data from the Blockchain nodes.
In this system architecture, we defined three logical
organizations namely Customer, Service Provider, and
Information Security Auditor. Each logical organization can
be assumed as a representation of real time entities of
respective stakeholders.
Since logical organizations have been defined based on the
functionalities of respective stakeholders who are concerned
about the security aspects of the business entity, and all
stakeholders are ensured of unique state replication with
tamper-proof capability the security assessment of the
business entity can be regarded as a fool-proof, robust and
trustworthy system. |
 ICACT20230046 Slide.14
[Big Slide]
[YouTube] ICACT20230046 Slide.14
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
With the above architecture, the system reports its findings by computing the average compliance rate over a period of time as well as the overall compliance rate at any given time frame as follows.
Compliance Rate (CR) = (Xt-1 – Xt ) / Xt-1 where Xt is no of
errors observed w.r.t security assurance policy at time t and Xt1 is at time t-1. CR represents the observed rate of change w.r.t
identified non-compliance factors of security policy. The CR
represents the compliance rate against the security policy
pertaining to the most recent time window. The time window
represents the gap between two successive vulnerability
analysis attempts. The time window is a configurable parameter
that defines how frequently the security log and other critical
information have to be collected from the critical resources to
be monitored.
Average Compliance Rate = 1/𝑛 ¢²𝐶𝑅𝑖 where ¡®CRi¡¯ is the
value of the compliance rate at a given instant of a time
window and ¡®n¡¯ is the no of such time windows chosen in a
given period (e.g., in the last 24 hours, in the last 30 days etc).
Severity Level is one of ¡®Critical¡¯, ¡®High¡¯, ¡®Medium¡¯, ¡®Low¡¯,
¡®None¡¯ labels which is decided based on Base Score. Base score computation is shown in next slide.
|
 ICACT20230046 Slide.15
[Big Slide]
[YouTube] ICACT20230046 Slide.15
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
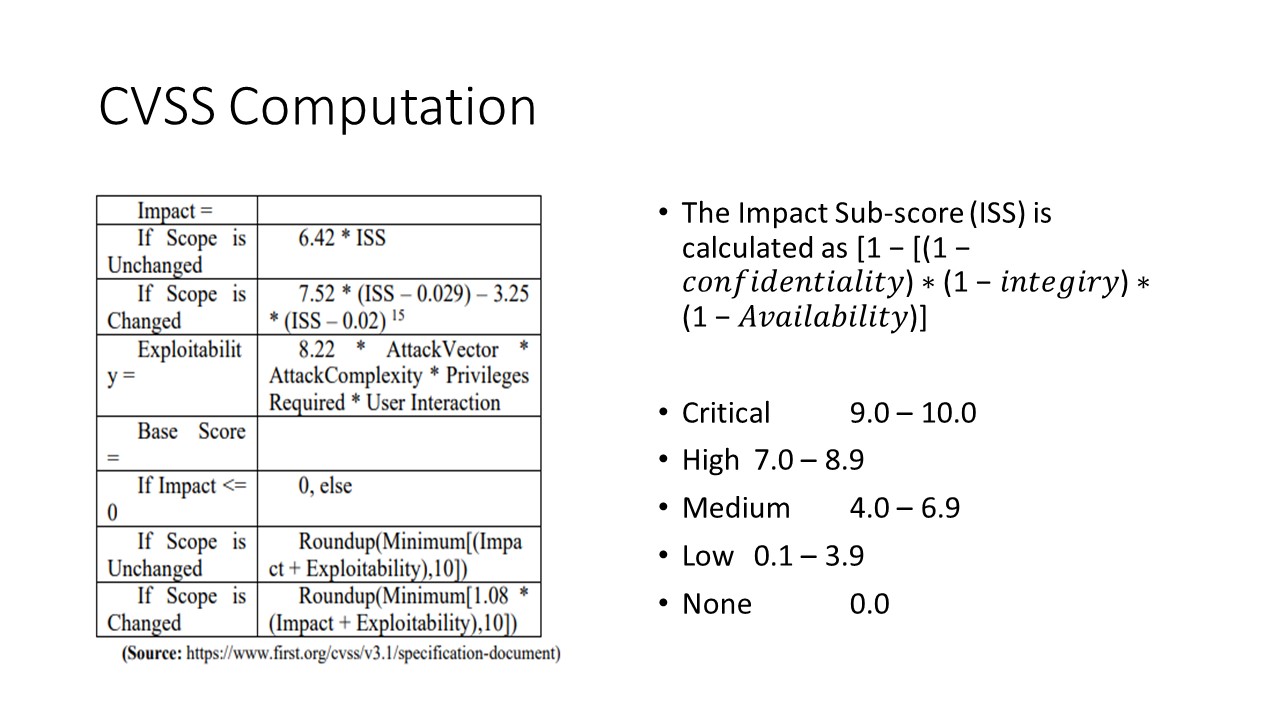 |
The base score is computed as shown in this slide. The base score and other formulae computation are done in accordance with section 7.1 of CVSS specification.
The severity level is decided based on base score value ranges. For example, if CVSS score is with in the range of 9-10 then the severity is decided as Critical, for 7-8.9 the severity is High, for 4.0 - 6.9 the severity is Medium etc.
|
 ICACT20230046 Slide.16
[Big Slide]
[YouTube] ICACT20230046 Slide.16
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
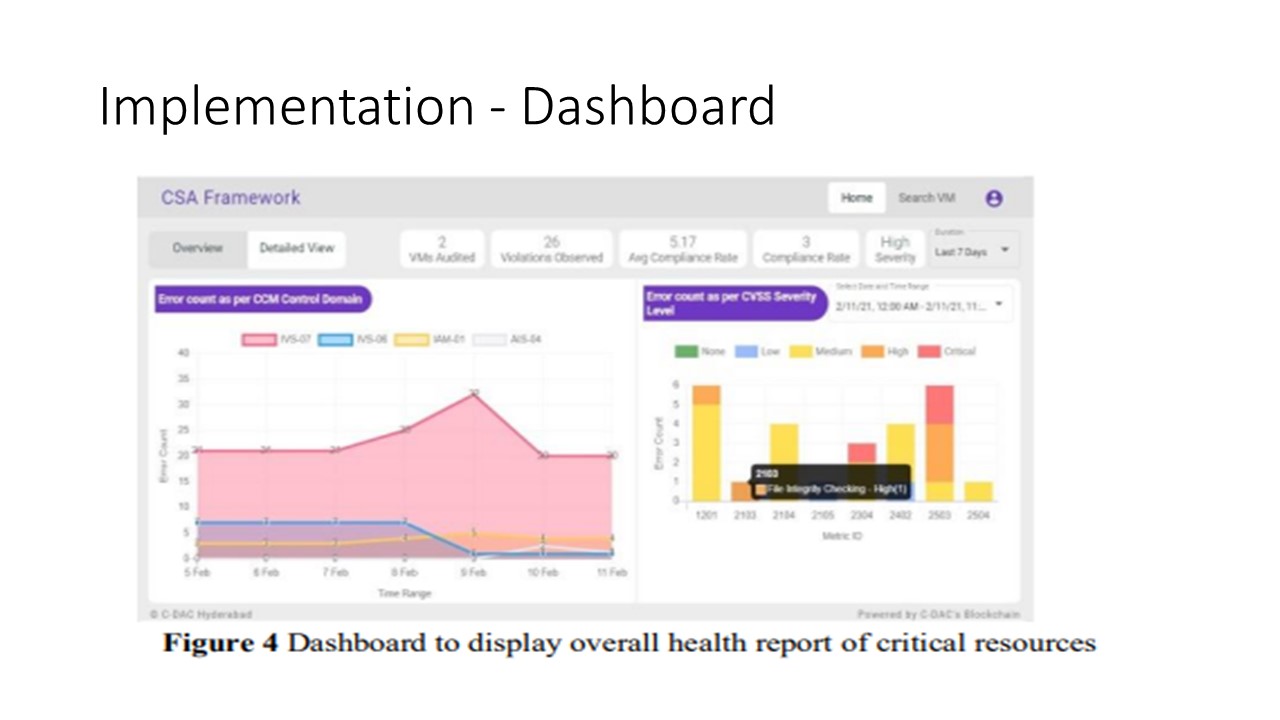 |
We have implemented an ¡®Agent¡¯ code using ¡°logstash¡±
for each control that is described in the security policy
framework depicted in table 1. The log information
from each resource is routed through an intermediate gateway
developed using Node.JS server side program which acts as a
client to the HLF Blockchain network. The Node server upon
receiving the encrypted JSON object sends the same unaltered
to the Blockchain network. The smart contract later decrypts
the JSON Object and stores the same in the Blockchain
network. A Dashboard component also has
been developed using the Angular programming framework
which can be accessed from the web by end-users who are
members of service providers, customer, and auditor
organizations. The dashboard component displays the no of
violations against the security policy framework as described
in Table I in a graphical format. It also displays various
metrics such as no of resources audited in the platform, the
average compliance rate over a period of time (e.g., last 24hrs,
7 days, 30 days). The application also displays the detailed report of each vulnerability and its mitigation plan.
The CVSS computation of all the resources gives us a clue about the current health scenario of the resources being monitored. Hence, it can be regarded as a way for monitoring whether the policy compliance has any effect or not. |
 ICACT20230046 Slide.17
[Big Slide]
[YouTube] ICACT20230046 Slide.17
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
The software module i.e., the intermediate gateway in our overall architecture, used for retrieval of data from the Blockchain network and to verify security policy conformance, should be designed in such a manner that it can withstand the vast amount of data that is required to be processed and improve the system response time. It is observed that if logs are collected at 10min intervals in a day, a total of 144 iterations will be required to store the log information in the Blockchain platform. We observed that with 14 control data that are collected 144 times a day and each JSON object size of 594bytes on average, approximately a
total of 1.14MB of data would be stored from each resource
that is being monitored. For 30 days 34.27MB of data will
have to be processed corresponding to a particular resource.
After observing this, we designed the below data structure to
cope up with data generated by multiple resources. In our
experiment, we used nearly 8VMs for monitoring purposes and
improved the system response time. The end-user, upon
selecting the duration for which the analysis has to be
performed in the dashboard, data pertaining to that period will
be retrieved from the Blockchain network and maintained in
accordance with the below data structure.
{
metric_id: val # id of the control name
result: [error1, error2, error3, error4 ¡¦.] #stores id of
every error that is observed
timestamp: [ts1, ts2, ts3 ¡¦.] #stores timestamps at
which the errors have been observed
machine_id: xxxx #id of the resource
hostname: val #name of the host
}
By default, the data collection interval is set to 10min in
our approach. In this format instead of processing individual
JSON objects representing each log entry, we rearranged
similar entries based on the time of their occurrence while
responding to the request from the dashboard component. This
has enhanced the system response time considerably.
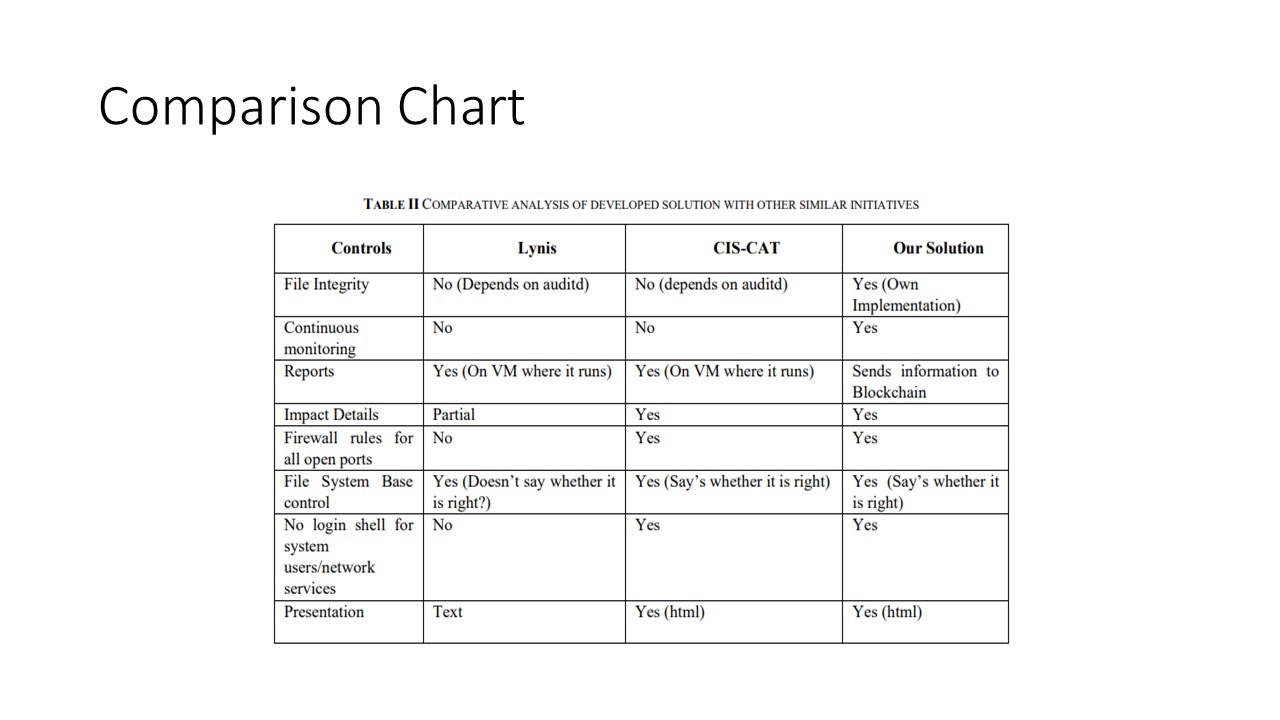
Table II in this slide depicts the comparative analysis of
developed solutions with different security analysis tools.
Other tools given in Table II have certain shortcomings when
compared to our solution as both of them generate a report in
the system in which those tools are deployed. We used
freeware versions. Whereas our solution provides a web
interface to view the health report of all resources being
monitored in one place. Moreover, we also have the CVSS
score that displays the severity level to alert the concerned
stakeholders. Another important feature of the developed
solution is that it automatically collects data at regular
intervals and sends them to the Blockchain platform for
permanent storage in a tamper-evident manner. This way, we
have designed and implemented a unified security policy
framework with 24x7 monitoring and alert system. |
 ICACT20230046 Slide.18
[Big Slide]
[YouTube] ICACT20230046 Slide.18
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
In this paper, we presented our security assessment model.
The model provides a unified security policy framework based
on inputs drawn from key takeaways from top threats in the
cloud platform, existing cloud best practices/standards such as
Cloud Security Alliance, and implementation techniques to
provide an early detection mechanism using CIS Benchmarks
etc. By using Blockchain technology we demonstrated how
the data provenance related to security aspects is maintained
uniquely in the decentralized network and in a time-stamped
and tamper-evident manner based on consensus among the
relevant stakeholders. We also have shown measurements of
security policy compliance rate and Common Vulnerability
Scoring System severity level. By looking at the security
policy compliance rate and the CVSS severity level one can
deduce the effectiveness of the overall system. This
architecture can be used for cloud environments also. |
 ICACT20230046 Slide.19
[Big Slide]
[YouTube] ICACT20230046 Slide.19
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Thank You |






