 ICACT20230129 Slide.00
[Big Slide]
[YouTube] ICACT20230129 Slide.00
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Hi everyone, my name is Yuki Ishida from Tokyo University of Information Sciences. Today, I will be talking about Analysis of DNS Graph of Phishing Websites Using Digital Certificates. |
 ICACT20230129 Slide.01
[Big Slide]
[YouTube] ICACT20230129 Slide.01
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Hi everyone, my name is Yuki Ishida from Tokyo University of Information Sciences.
Today, I will be talking about Analysis of DNS Graph of Phishing Websites Using Digital Certificates.
|
 ICACT20230129 Slide.02
[Big Slide]
[YouTube] ICACT20230129 Slide.02
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Here is the table of contents.
In this presentation, first I will talk about background of this study.
Then, I will introduce related works and research objectives.
After that, I will explain Certificate Transparency (CT) and DNS graphs using the CT logs.
After that, I will show you our analysis results.
Finally, I will make a summary and talk about future works.
|
 ICACT20230129 Slide.03
[Big Slide]
[YouTube] ICACT20230129 Slide.03
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
I will be talking about our research background.
Phishing attacks are currently on the rise, with the Anti-Phishing Work Group recently announcing that over 1 million such attacks were observed in the second quarter of 2022.
This is the highest number since the APWG began observations.
And the amount of damage caused by phishing is also increasing, with the FBI announcing that the total loss in 2021 was over $44 million.
Phishing sites should be taken down as soon as possible.
In addition, phishing websites have a short lifetime.
In fact, the mean lifetime of phishing websites was about three days.
From these backgrounds, phishing websites must be detected quickly to prevent damage from phishing attacks.
|
 ICACT20230129 Slide.04
[Big Slide]
[YouTube] ICACT20230129 Slide.04
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
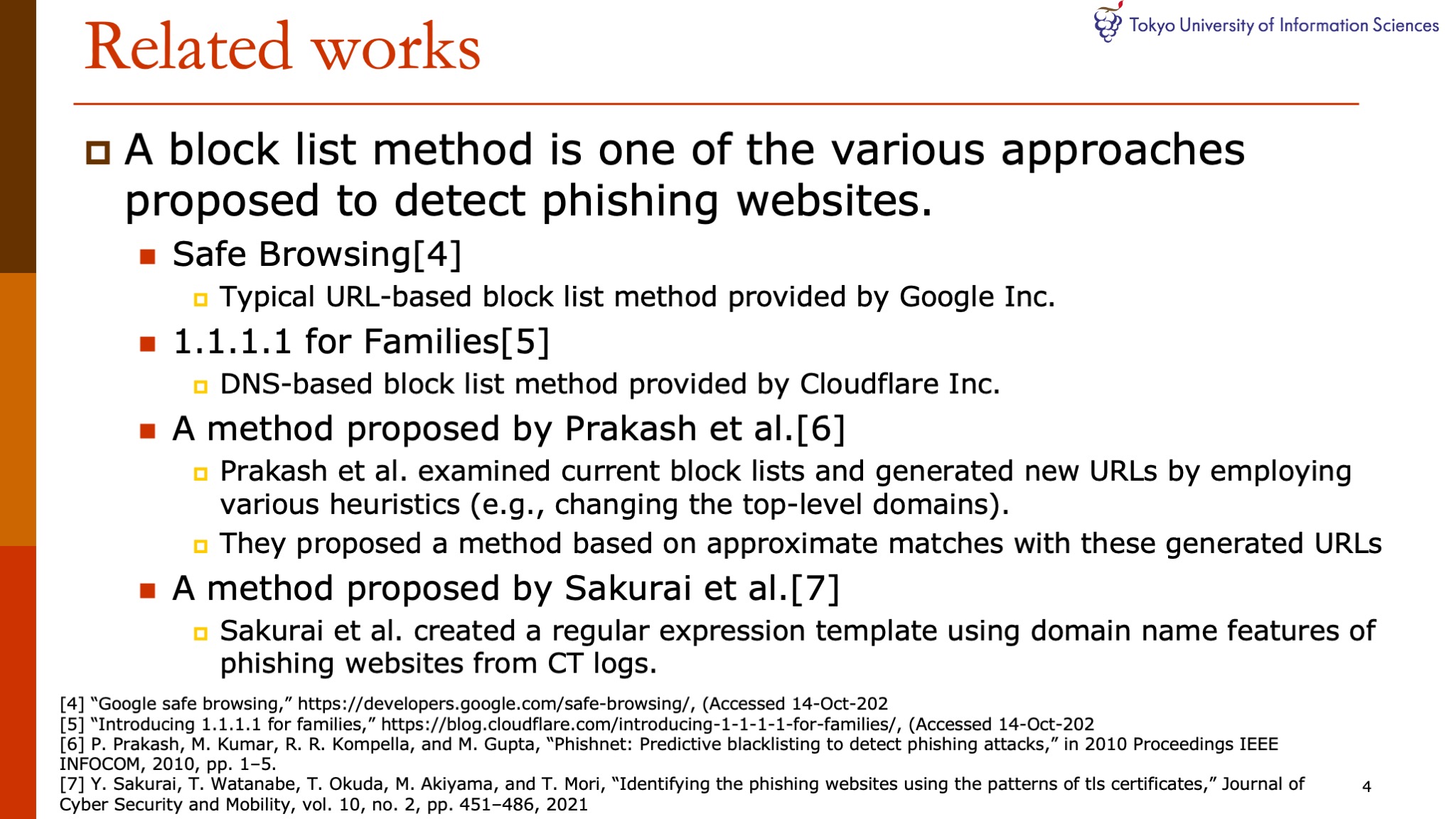 |
The block list method has been proposed as one of the various approaches proposed to detect phishing websites.
Safe Browsing and 1.1.1.1 for Families are two of the most popular and practiced blocklist approach that is already available to the public.
In addition, Prakash and Sakurai have also been respectively proposed signature-based block list method using current block lists of phishing websites and logs of HTTPS-enabled phishing websites.
|
 ICACT20230129 Slide.05
[Big Slide]
[YouTube] ICACT20230129 Slide.05
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Here is our research objective.
Phishers frequently change domain names and IP addresses of websites to avoid detection.
However, the traditional block list methods remain insufficient with regard to dealing with rapidly changing domain names and IP addresses of phishing websites.
In addition, phishing websites often employ certificates and HTTPS encryption to appear more trustworthy.
Therefore, in this study, we constructed and analyzed DNS graphs of domain names and IP addresses of HTTPS-enabled phishing websites to be useful for phishing website detection.
|
 ICACT20230129 Slide.06
[Big Slide]
[YouTube] ICACT20230129 Slide.06
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
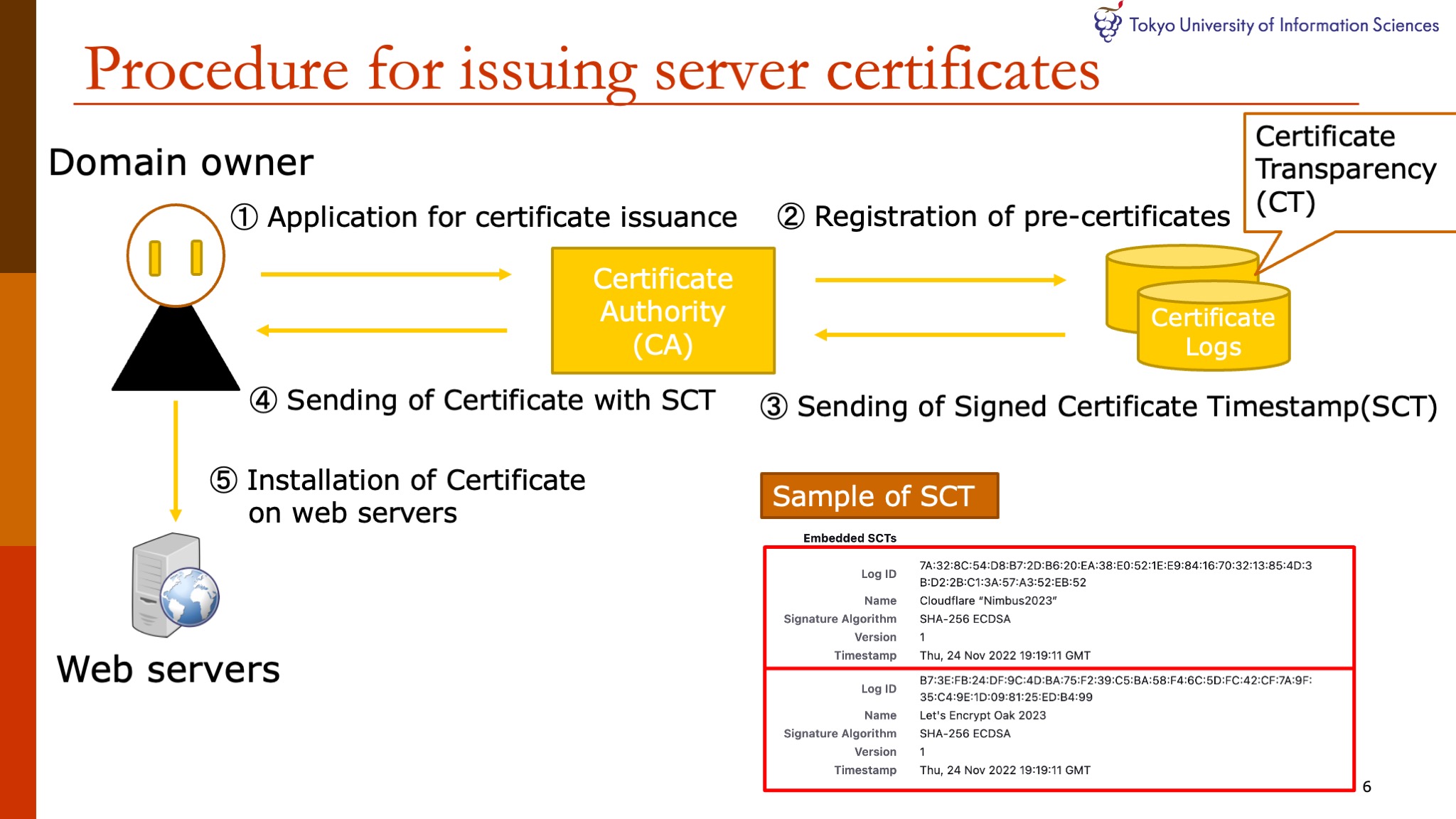 |
Here is an overview of the process of obtaining a server certificate.
First, a domain owner submits a request for certificate issuance to a Certificate Authority (CA).
The CAs register a pre-certificate to Certificate Transparency (CT) servers.
The CT servers return registration time, that is SCT, to the CA.
The CA return the signed certificate with SCT to the domain owner.
Finally, the domain owner installs the certificate on the web servers.
Here, it should be noted that the certificate information is recorded on the CT log servers at the same time that the certificate is registered.
|
 ICACT20230129 Slide.07
[Big Slide]
[YouTube] ICACT20230129 Slide.07
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Certificate Transparency is a security framework for monitoring and auditing all public digital certificates issued by CAs, and CT is published in RFC6962.
Whenever CAs issue a digital certificate, a corresponding log entry is made in the CT logs.
Therefore, if we can identify the phishing domain names from the CT logs, we believe that phishing websites can be detected before they become active.
|
 ICACT20230129 Slide.08
[Big Slide]
[YouTube] ICACT20230129 Slide.08
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
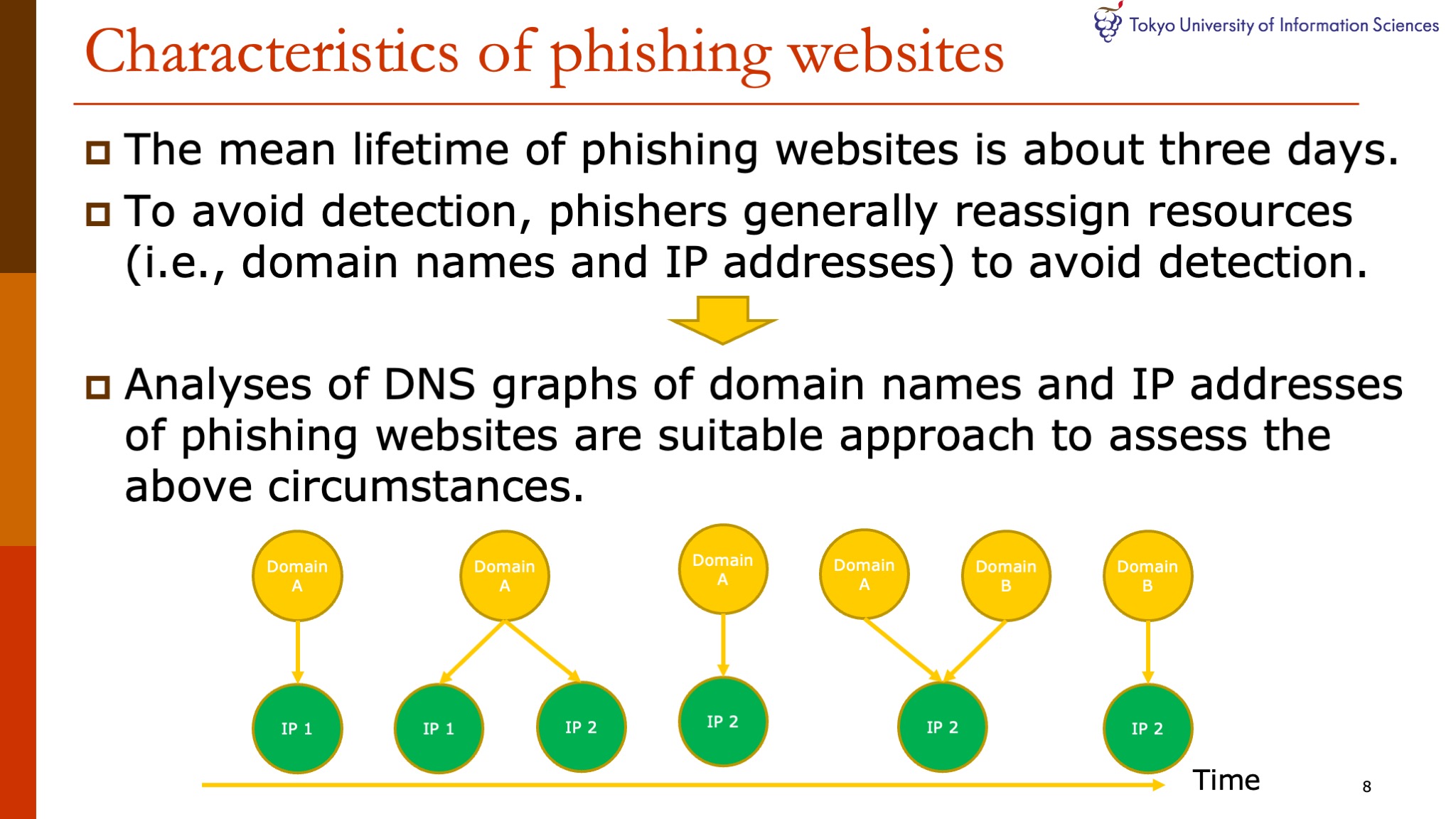 |
It was reported that the average lifetime of phishing sites was about three days in previous work.
In general, phishers reassign resources, such as domain names and IP addresses, to avoid detection.
Therefore, to assess the above circumstances, we consider that analyses of DNS graphs of domain names and IP addresses of phishing websites are suitable approach.
|
 ICACT20230129 Slide.09
[Big Slide]
[YouTube] ICACT20230129 Slide.09
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
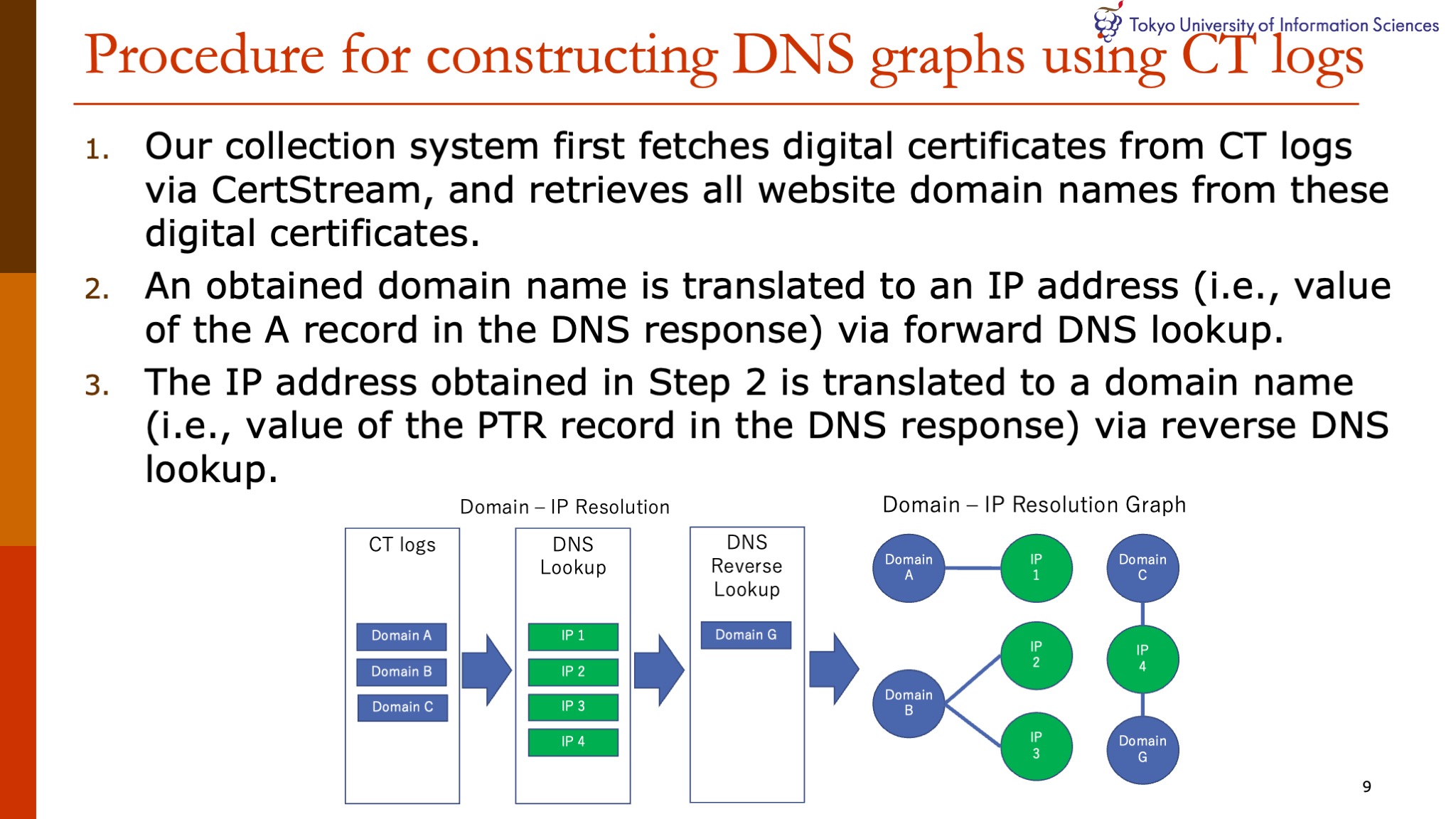 |
The following procedure was employed in the collection of CT logs and construction of DNS graphs.
In step 1, our collection system first fetches digital certificates from CT logs via CertStream, and retrieves all website domain names from these digital certificates.
In step 2, the obtained domain name is translated via forward DNS lookup to an IP address that is the value of the A record in the DNS response.
In step 3, the IP address obtained in step 2 is translated via reverse DNS lookup to a domain name that is the value of the PTR record in the DNS response.
|
 ICACT20230129 Slide.10
[Big Slide]
[YouTube] ICACT20230129 Slide.10
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
In our experiment analysis, we collected domain names and IP addresses observed over a 7-day period from September 20, 2022 to September 27, 2022.
After a list of domain names or IP addresses is created, an item on the list is labeled as a phishing website using information from several sites such as PhishTank and so on, that list reported phishing URLs.
|
 ICACT20230129 Slide.11
[Big Slide]
[YouTube] ICACT20230129 Slide.11
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
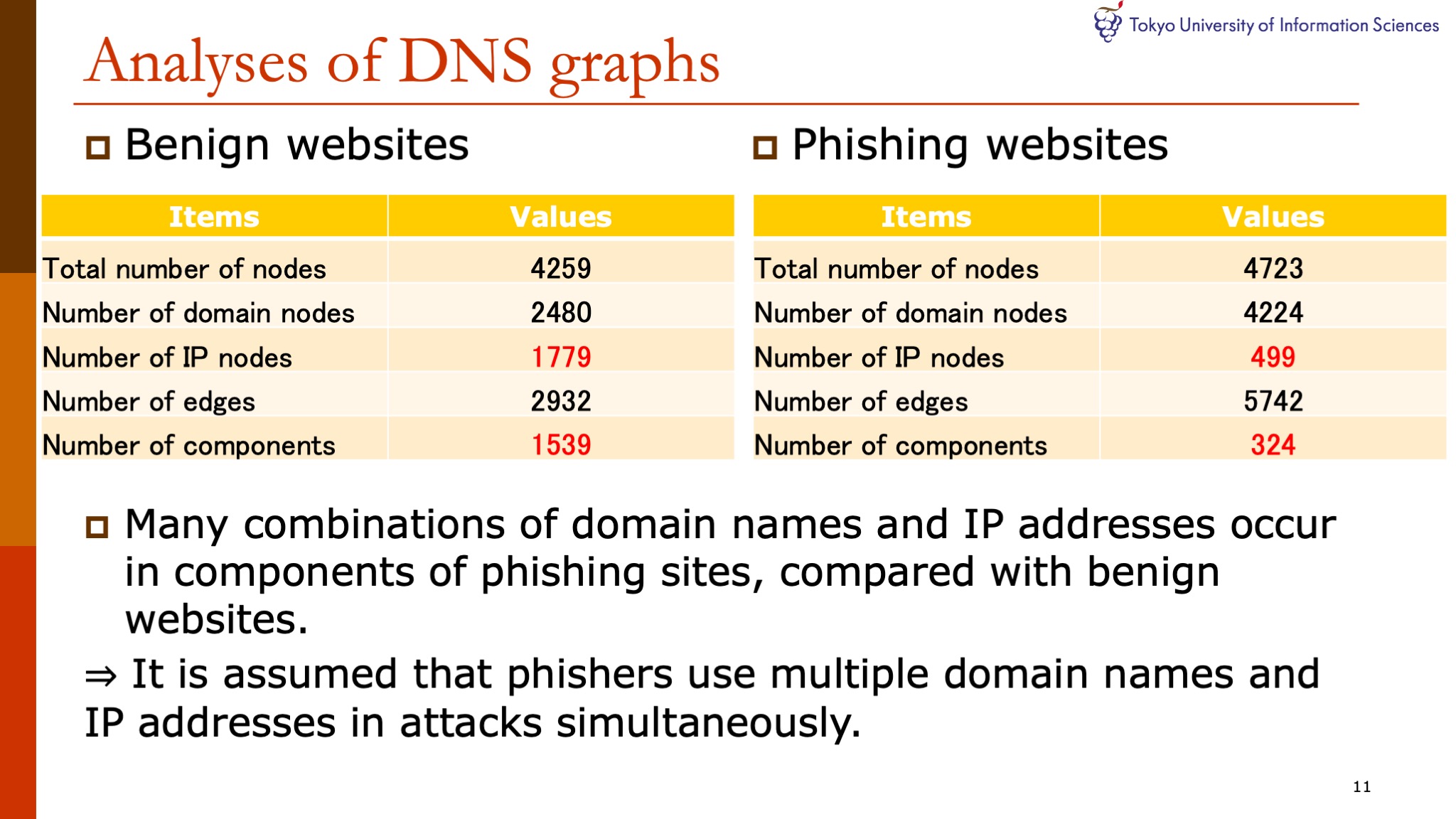 |
We present the analysis results for the DNS graphs of phishing and benign websites.
As the tables show, any combinations of domain names and IP addresses occur in components of phishing websites, compared with benign websites.
We notice that the number of IP address nodes and components are different.
These results suggest that phishers use multiple domain names and IP addresses in their attacks.
|
 ICACT20230129 Slide.12
[Big Slide]
[YouTube] ICACT20230129 Slide.12
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
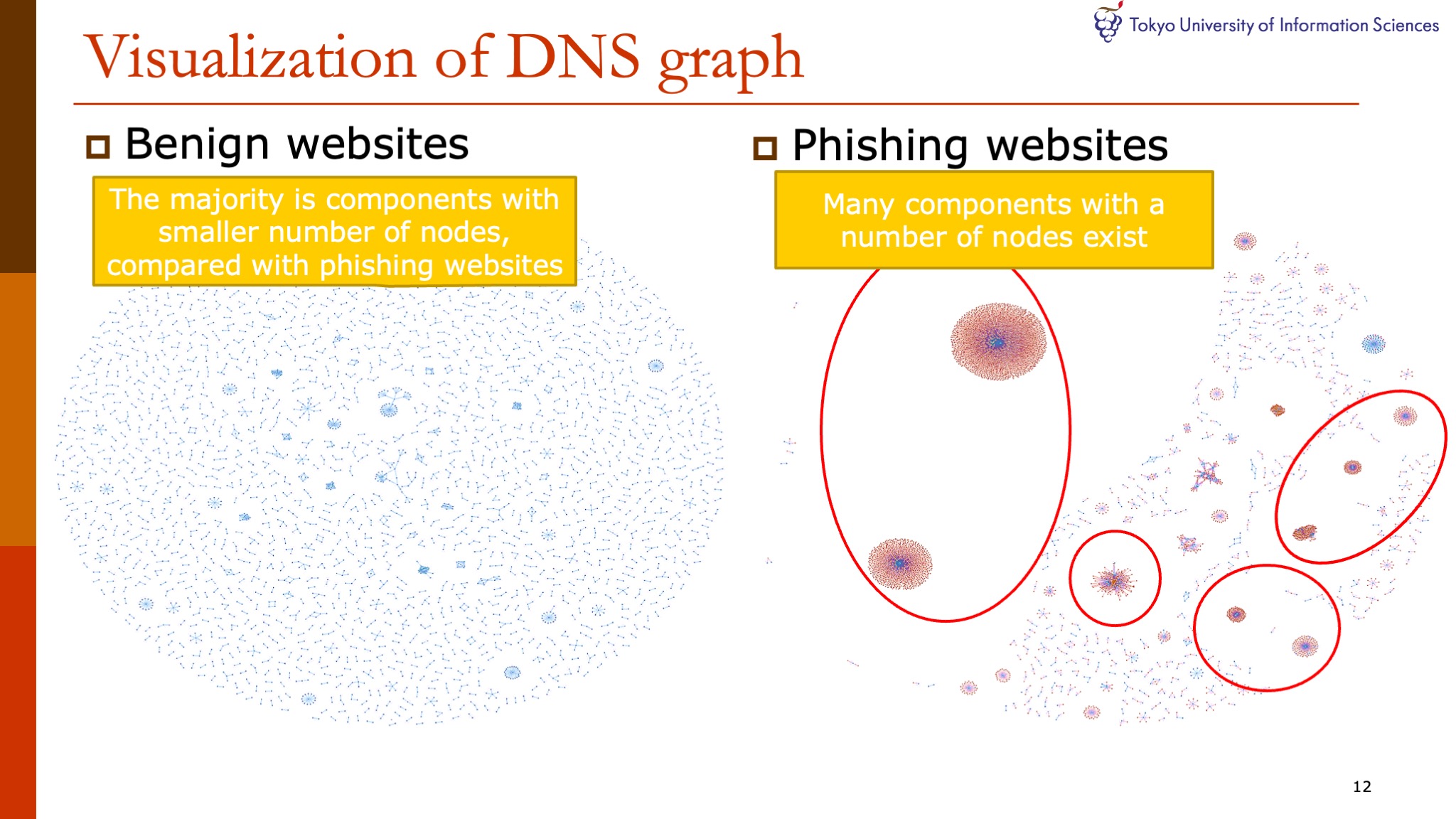 |
This is a visualization of the DNS graph.
Phishing sites have many components with a number of nodes.
On the other hand, in benign websites, the majority is components with smaller number of nodes, compared with phishing websites.
|
 ICACT20230129 Slide.13
[Big Slide]
[YouTube] ICACT20230129 Slide.13
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
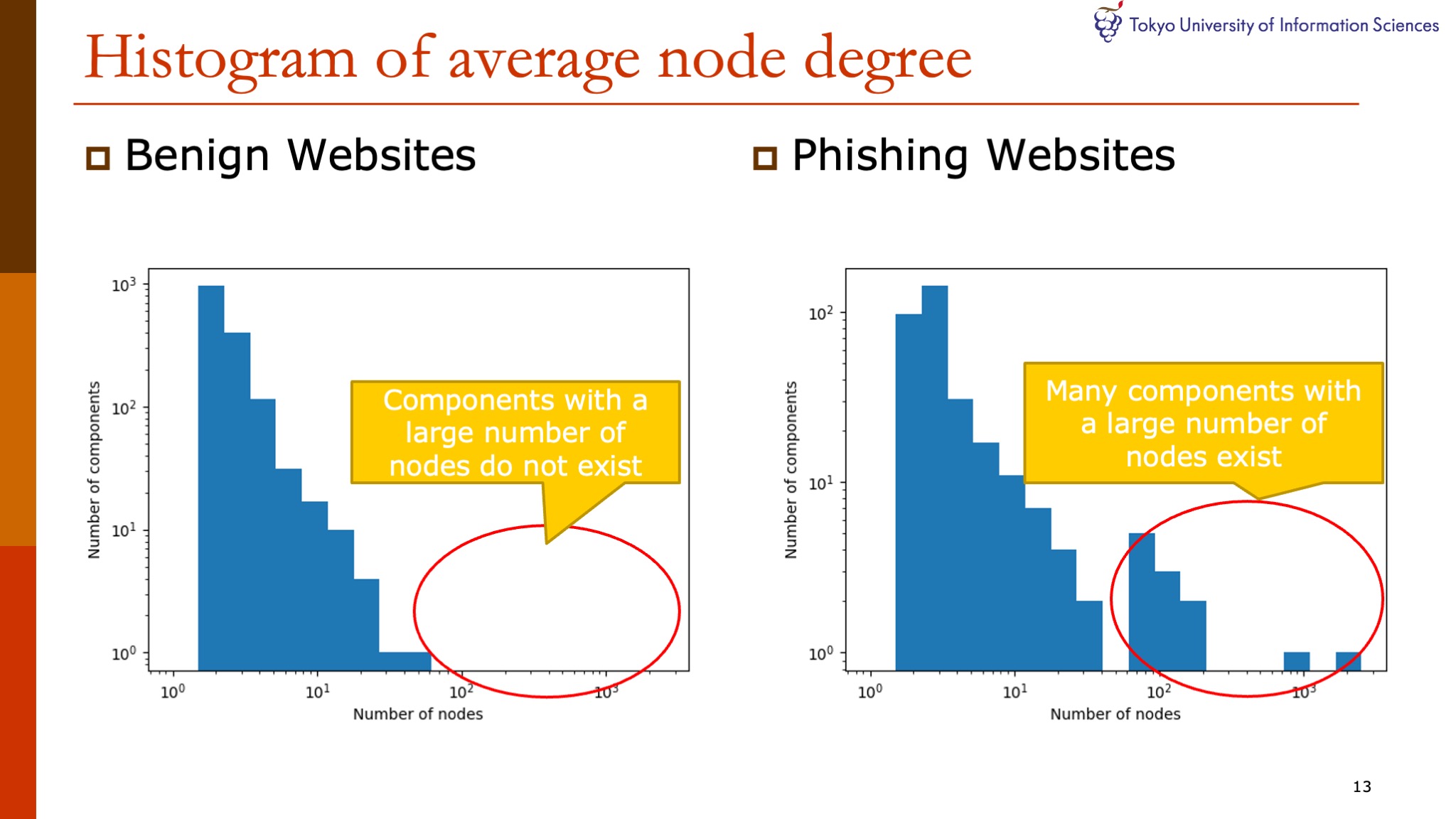 |
Next, we analyze the histograms measuring the number of nodes per component for benign websites and phishing websites.
These result show that there are many components with a large number of nodes in the phishing websites.
|
 ICACT20230129 Slide.14
[Big Slide]
[YouTube] ICACT20230129 Slide.14
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
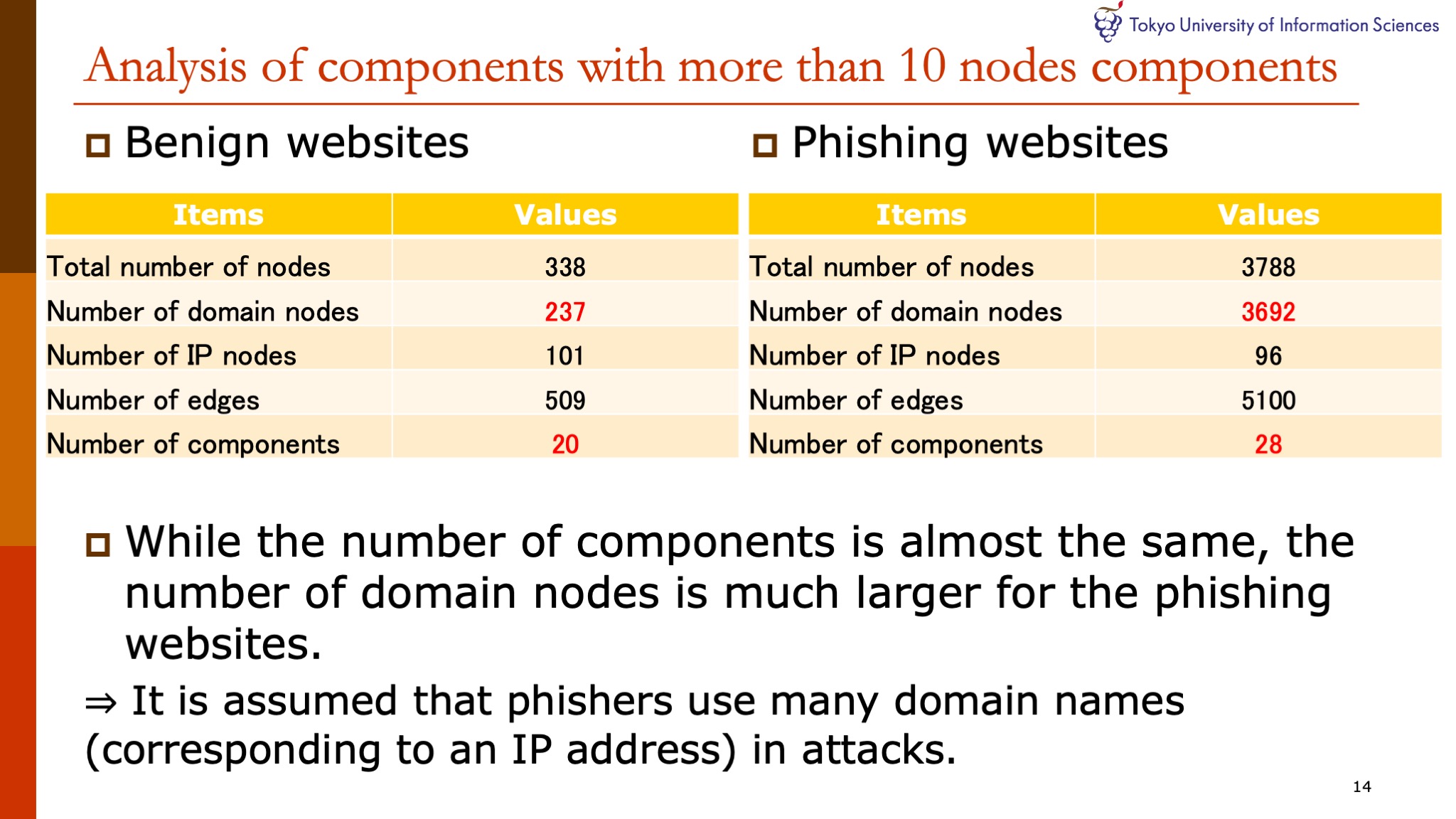 |
Next, we focus on components with 10 or more nodes of the DNS graphs of the benign and phishing websites and analyze them.
These two tables are the results of extracting components with more than 10 nodes from DNS graphs of the benign and phishing websites.
While the number of components is almost the same, the number of domain nodes is much larger for the phishing websites.
These results, it is assumed phishers use many domain names that correspond to an IP address in attacks.
|
 ICACT20230129 Slide.15
[Big Slide]
[YouTube] ICACT20230129 Slide.15
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
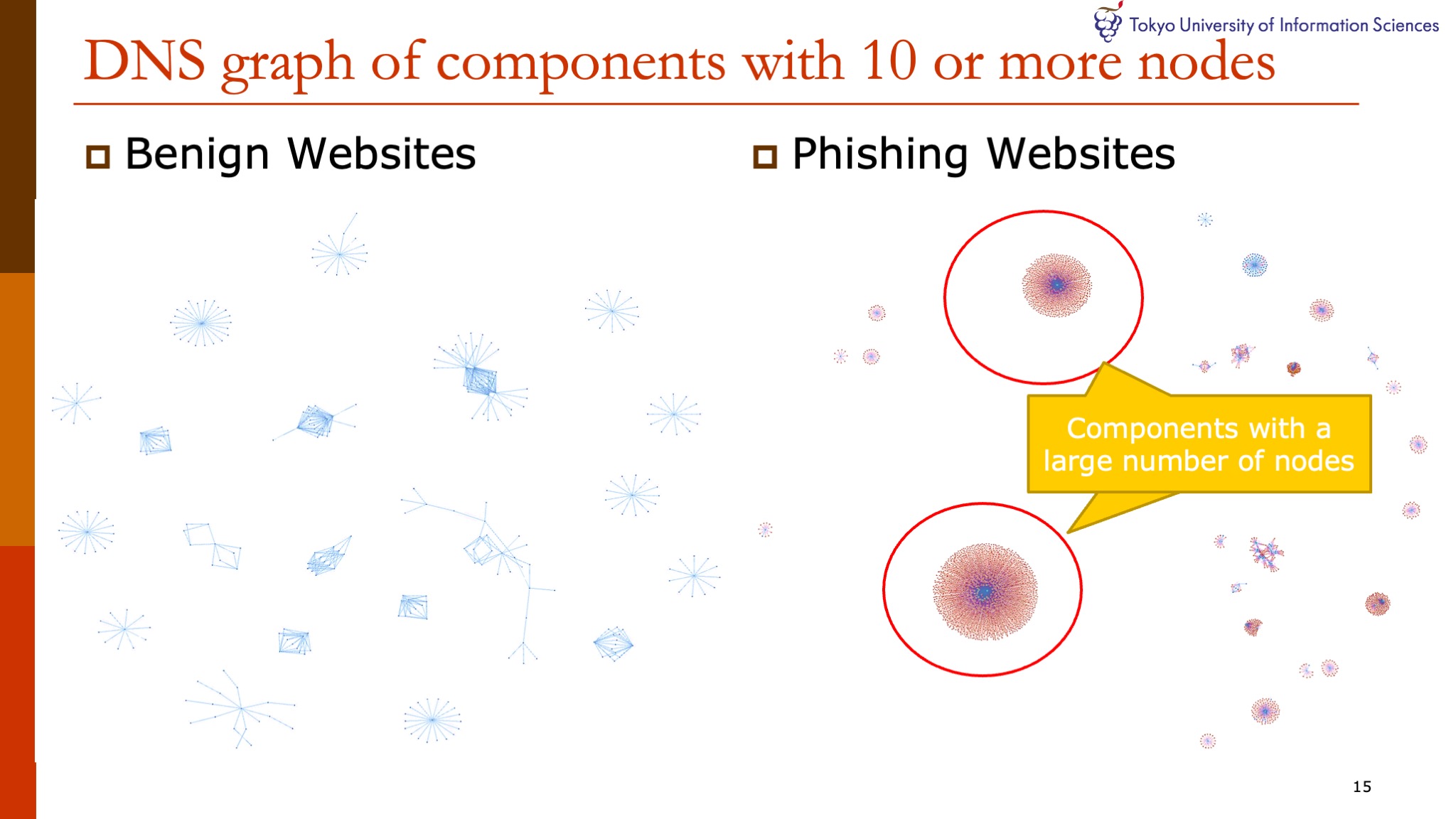 |
We again notice the DNS graphs of phishing.
Phishing websites clearly have two components with a large number of nodes.
We believe that this is evidence that phishing websites are created mechanically and that this is one of major characteristics of phishing sites.
|
 ICACT20230129 Slide.16
[Big Slide]
[YouTube] ICACT20230129 Slide.16
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
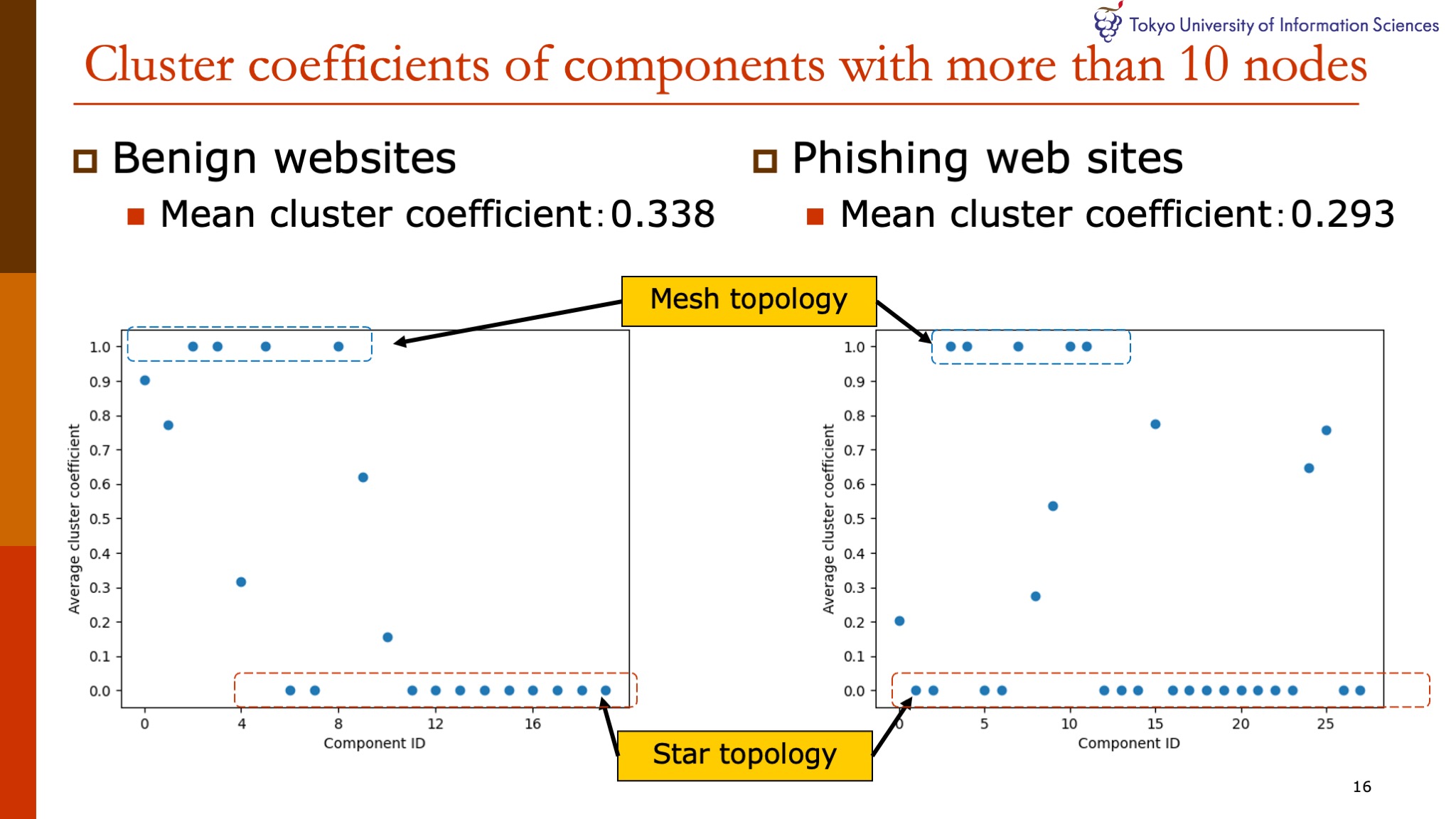 |
To explore features for each component, we analyzed the cluster coefficient of each component.
Here, the x-axis is the numbered component.
Both figures show the square-based clustering coefficients of each component.
When the cluster coefficient is zero, it indicates star topology.
On the other hand, when the cluster coefficient is one, it indicates mesh topology.
With regard to the clustering coefficient, few differences were observed between the benign and phishing websites.
|
 ICACT20230129 Slide.17
[Big Slide]
[YouTube] ICACT20230129 Slide.17
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Let me summarize my presentation.
We focused on phishing websites using HTTPS and constructed and analyzed DNS graphs of domain names and IP addresses of phishing websites using CT logs.
We showed that the main differences between the DNS graphs of benign and phishing websites are the average number of nodes per component and the average node degree per component.
In terms of the clustering coefficient, few differences were observed between the benign and phishing websites corresponding to components with 10 or more nodes.
In future work, we plan to analyze the results of this study in more detail using other complex network metrics.
We also intend to analyze the growth and change of DNS graphs for benign and phishing websites using time series analysis, and to develop a detection method for phishing websites.
|
 ICACT20230129 Slide.18
[Big Slide]
[YouTube] ICACT20230129 Slide.18
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Thank you so much for your kind attention. Welcome any comment or question.
|






