 ICACT20230167 Slide.01
[Big Slide]
[YouTube] ICACT20230167 Slide.01
[Big Slide]
[YouTube] |
Chrome  Click!! Click!! |
 |
Hello everyone. First of all, I would like to thank the organizers for accepting our paper. Let me introduce myself. I am Jian-Fu Qiu from National Taiwan University of Science and Technology. As you can see on the screen, our topic today is an intrusion detection system based on an artificial intelligence box with machine learning developed in collaboration with Taiwan's Industrial Research Institute. |
 ICACT20230167 Slide.02
[Big Slide] ICACT20230167 Slide.02
[Big Slide]
|
Chrome  Click!! Click!! |
 |
So, this is today's outline. In this presentation, We can separate into the following parts: Introduction, methods, results and conclusion.
In the first part, I will first introduce the background of the study and introduce the content of our proposed system. The second part will explain our system architecture diagram, the overall flow of the algorithm, the features we used, and the environment configuration of AI BOX in detail
|
 ICACT20230167 Slide.03
[Big Slide] ICACT20230167 Slide.03
[Big Slide]
|
Chrome  Click!! Click!! |
 |
First is the introduction. |
 ICACT20230167 Slide.04
[Big Slide] ICACT20230167 Slide.04
[Big Slide]
|
Chrome  Click!! Click!! |
 |
With the successful development of AIoT, industrial environments are increasingly vulnerable to cybersecurity attacks.
Taiwan, which is often the target of attacks, has also started to focus on information security protection in the industrial field in recent years. Traditional information security processes are no longer sufficient in today's smart factory environment. Traditional information security event handling is shown in Figure 1.
Our concern is how to implement a system that detects abnormal network traffic. We propose to use machine learning and network traffic feature extraction tool cicflowmeter on the hardware AIBOX provided by Industrial Technology Research Institute to form a complete intrusion detection system.
|
 ICACT20230167 Slide.05
[Big Slide] ICACT20230167 Slide.05
[Big Slide]
|
Chrome  Click!! Click!! |
 |
Now,it's the method part |
 ICACT20230167 Slide.06
[Big Slide] ICACT20230167 Slide.06
[Big Slide]
|
Chrome  Click!! Click!! |
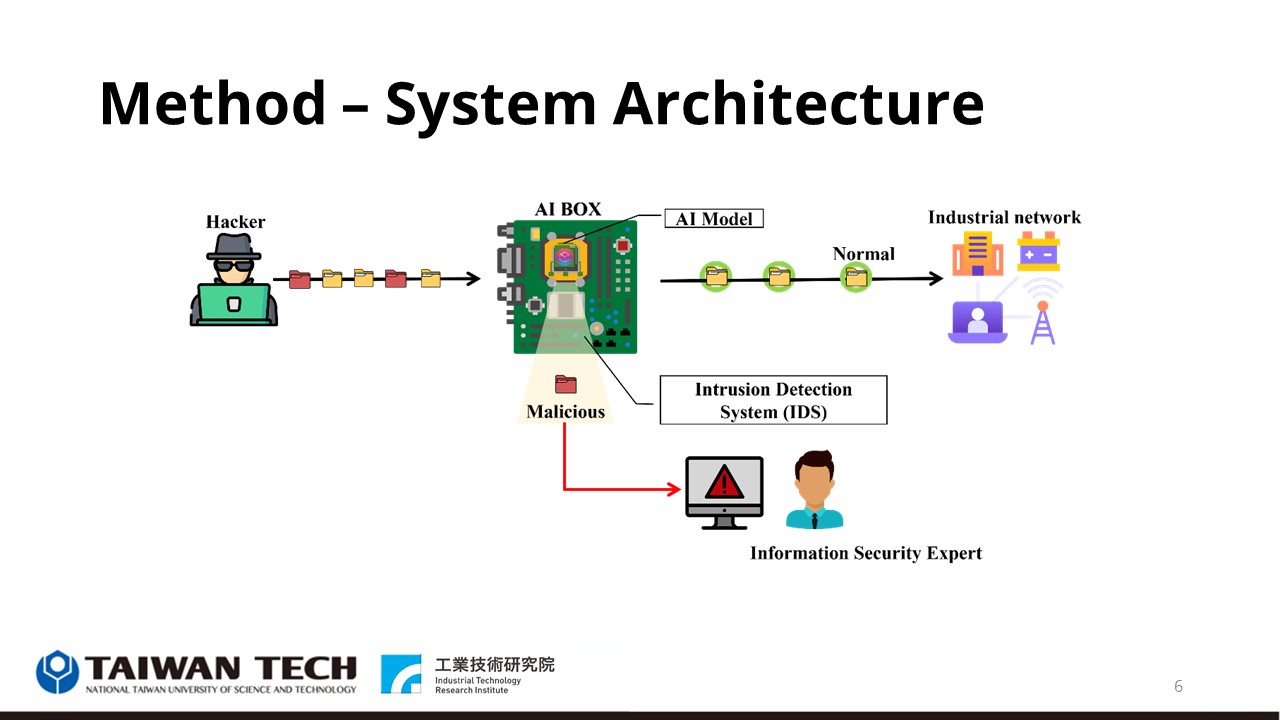 |
So, let me give you a brief overview. This figure is the system architecture. In the smart factory network environment, normal and abnormal network traffic will be encountered. Using our proposed IDS implemented on AIBOX, it can judge whether the network traffic is abnormal in real-time and further decide whether to isolate the network traffic Or raise a system warning. |
 ICACT20230167 Slide.07
[Big Slide] ICACT20230167 Slide.07
[Big Slide]
|
Chrome  Click!! Click!! |
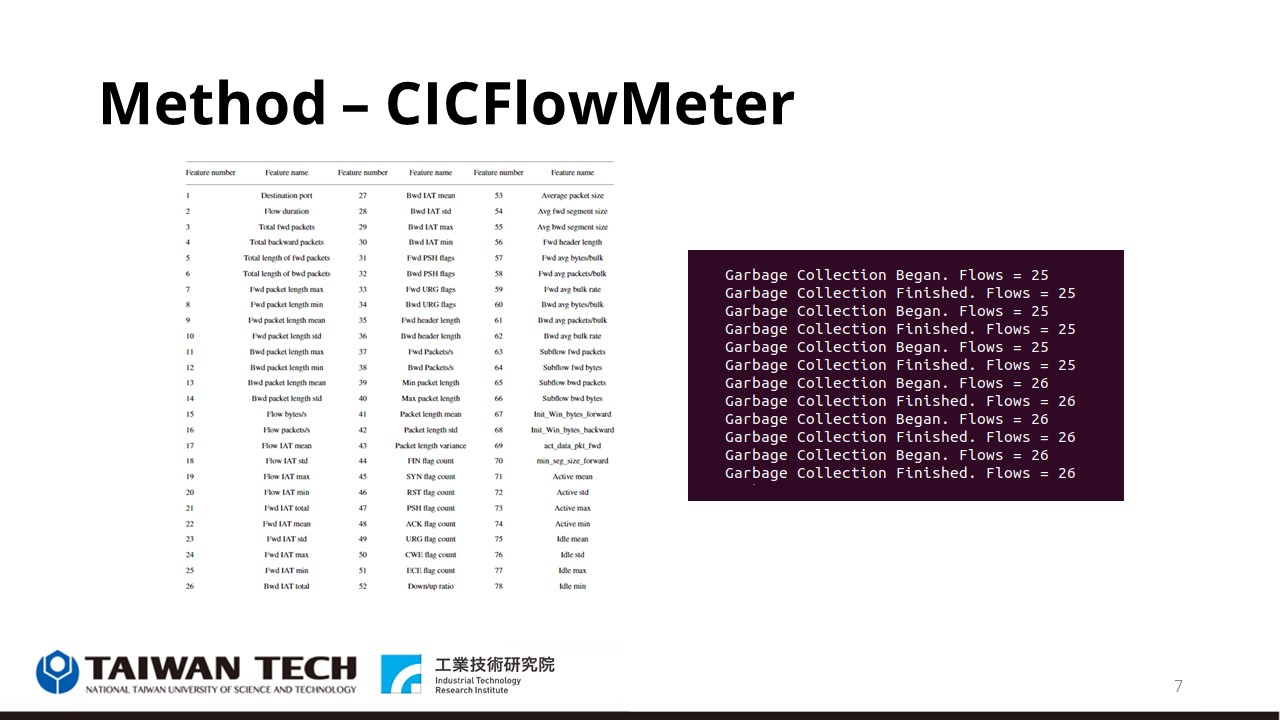 |
On this page, I will introduce CICFLOWMETER, a tool that can automatically extract network traffic features. The number of features is 78 as shown in the left picture, and the right picture is an example of feature extraction. |
 ICACT20230167 Slide.08
[Big Slide] ICACT20230167 Slide.08
[Big Slide]
|
Chrome  Click!! Click!! |
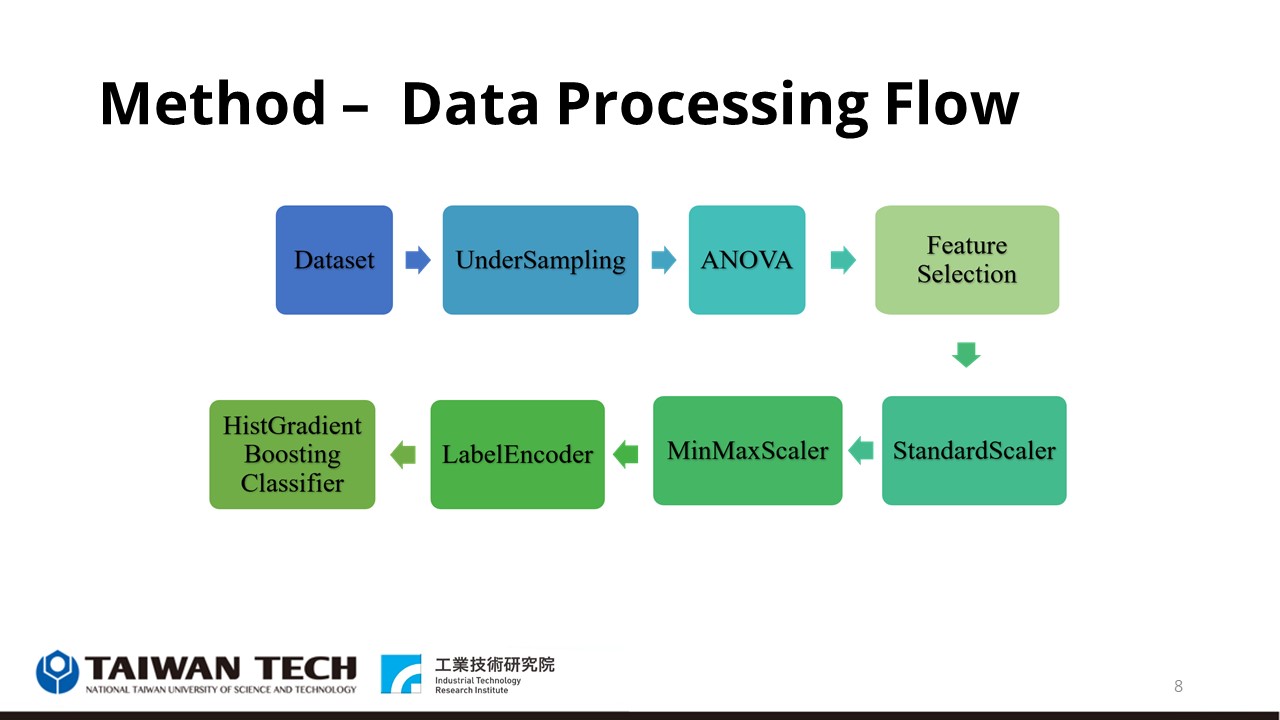 |
In the dataset processing, the three datasets were mixed and split into training and test sets with a ratio of 3:1. Then, the datasets were further analyzed for label uniformity and found to have unbalanced labels. In this study, we use the imblearn tool to perform data under-sampling to equalize the labeling ratio of the whole dataset. We then use the feature importance evaluation tool f_classif and the feature selection tool SelectKBest to perform feature filtering. First, the f_classif tool uses ANOVA (Analysis of Variance) statistics to assign P-values to each feature. Then the SelectKBest tool ranks the P-values of each feature and selects K features in the dataset for model training. Twenty features are finally selected for model training in this study.
After selecting the desired dataset features, data pre-processing is performed. The data pre-processing techniques use in this study are StandardScaler, MinMaxScaler, and LabelEncoder. First, StandardScaler is applied to each feature value to make the Gaussian distribution of each feature value so that the mean value of each group feature is zero and the standard deviation is one. Then MinMaxScaler is performed to reduce the range of each feature in the dataset from zero to one, and finally, the labeled data in the dataset is encoded by LabelEncoder.
|
 ICACT20230167 Slide.09
[Big Slide] ICACT20230167 Slide.09
[Big Slide]
|
Chrome  Click!! Click!! |
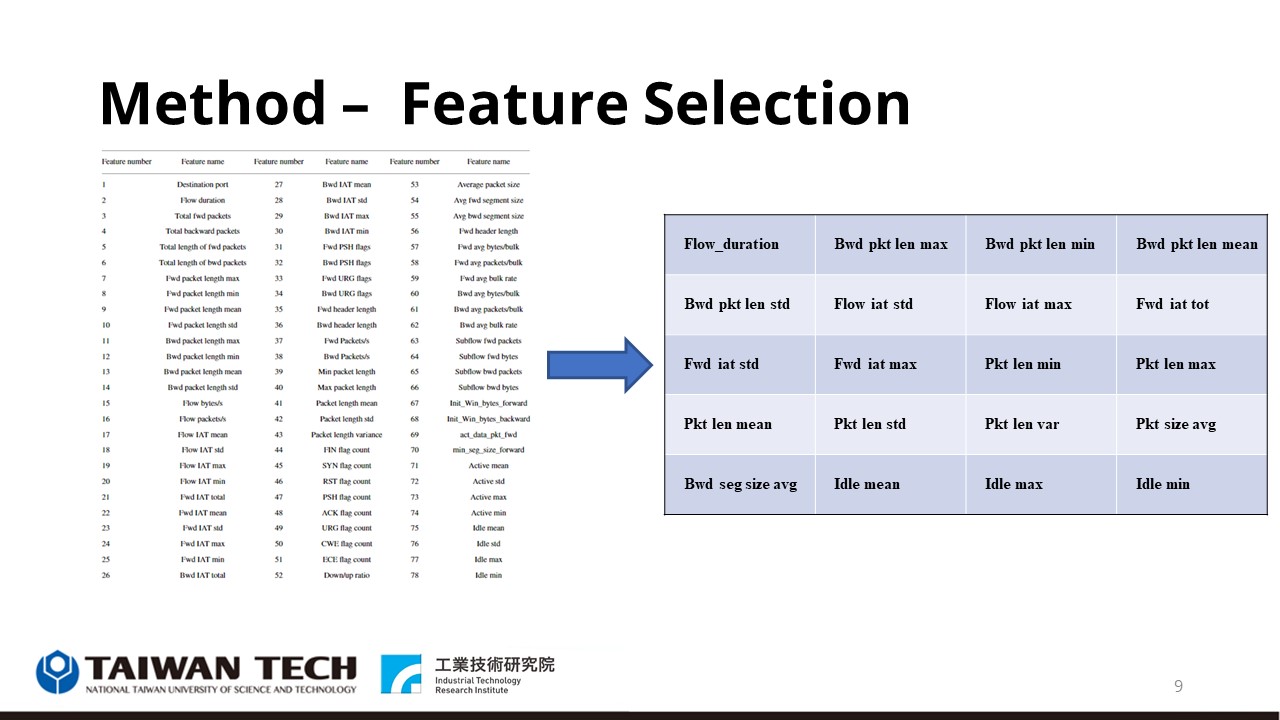 |
So we selected the best 20 features from 78 features for model training, and the graph on the right shows the features we used. |
 ICACT20230167 Slide.10
[Big Slide] ICACT20230167 Slide.10
[Big Slide]
|
Chrome  Click!! Click!! |
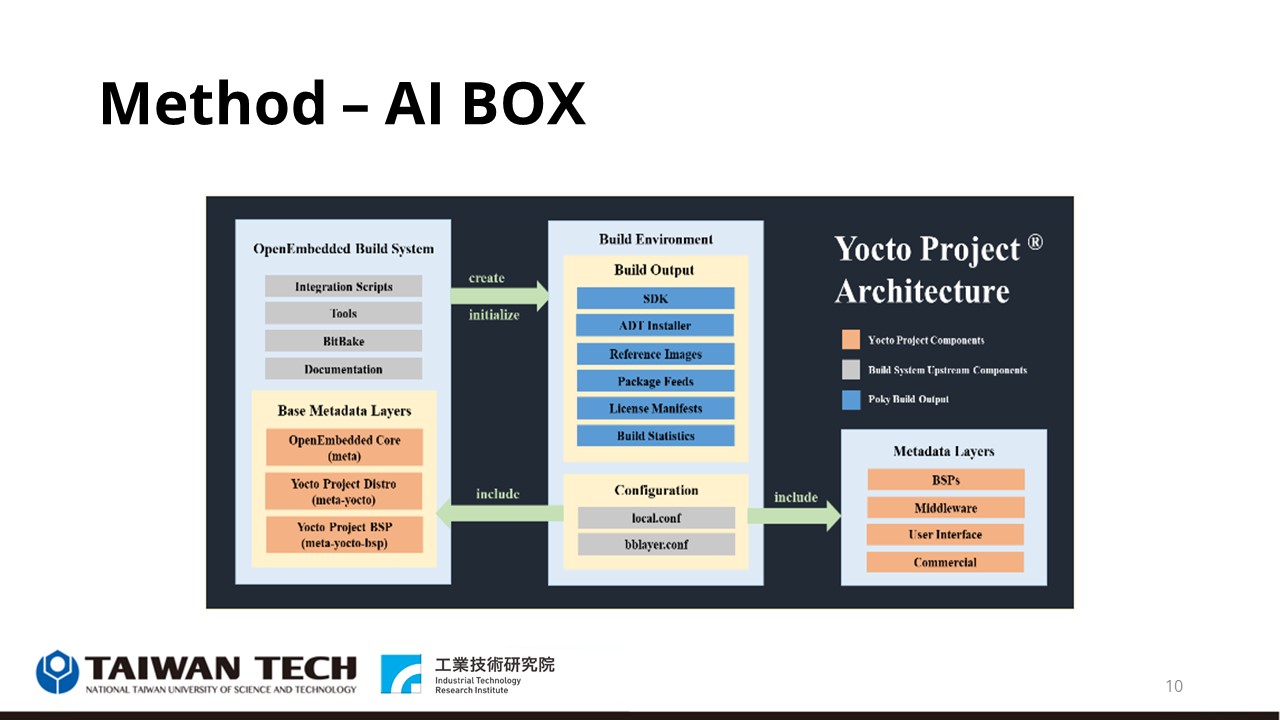 |
Next, this picture is the AI BOX architecture provided by ITRI. This embedded system uses the open software Yocto Project. Its distribution Poky covers the basic components of the OpenEmbedded software architecture. It uses the Bitbake automated program compilation tool to analyze the hardware function information, Kernel configuration information, and other required hardware information driver combination for cross-compilation on the AI BOX. |
 ICACT20230167 Slide.11
[Big Slide] ICACT20230167 Slide.11
[Big Slide]
|
Chrome  Click!! Click!! |
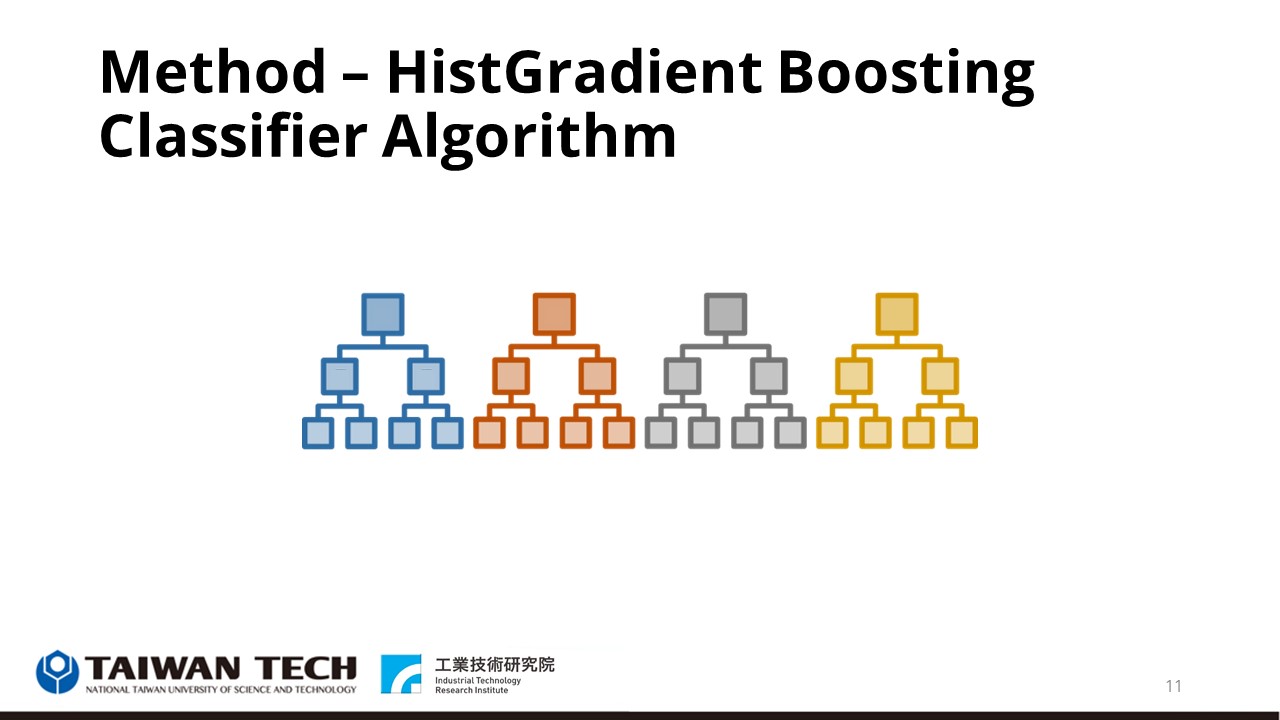 |
Now let's turn to machine learning, we use HisGradient Boosting Classifier to make predictions inspired by the LightGBM algorithm and based on the Gradient Boosting Classifier algorithm.
The HistGradient Boosting Classifier algorithm is a tree structure. Instead of using Gini coefficients as in the Random Forest algorithm [11], the training data is first classified into several numerical segments, i.e., the training data is histogrammed, and the splitting points are determined based on the structure of the data after that.
|
 ICACT20230167 Slide.12
[Big Slide] ICACT20230167 Slide.12
[Big Slide]
|
Chrome  Click!! Click!! |
 |
Next, we need to discuss the data sets used for model training. We used three data sets. CIC-IDS and CIC-DDOS are two public data sets, which contain multiple abnormal data and normal data. The brute force attack data set is We use the Kali Linux environment with brute force attack tools to collect. |
 ICACT20230167 Slide.13
[Big Slide] ICACT20230167 Slide.13
[Big Slide]
|
Chrome  Click!! Click!! |
 |
Now, it's the result part |
 ICACT20230167 Slide.14
[Big Slide] ICACT20230167 Slide.14
[Big Slide]
|
Chrome  Click!! Click!! |
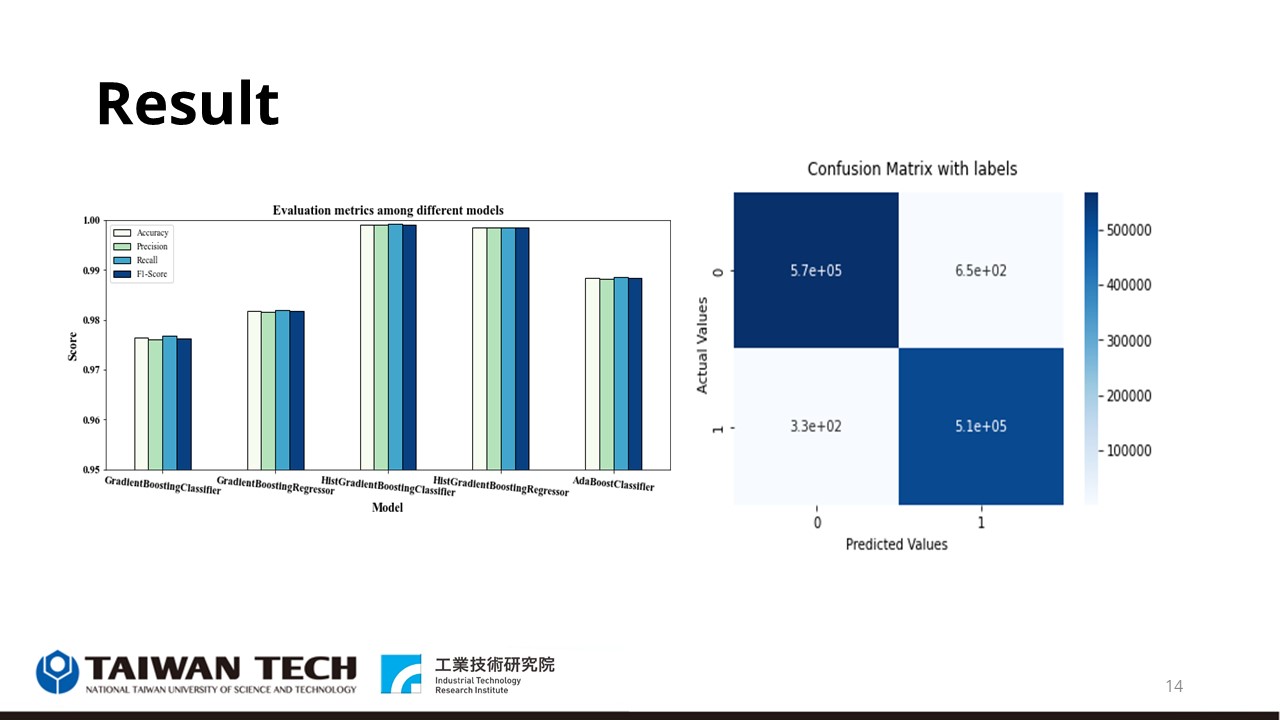 |
In addition to random forest, we also tried other models for prediction, and found that random forest can reach 99% in accuracy, precision, and recall. Our proposed method can well identify normal and abnormal network traffic. |
 ICACT20230167 Slide.15
[Big Slide] ICACT20230167 Slide.15
[Big Slide]
|
Chrome  Click!! Click!! |
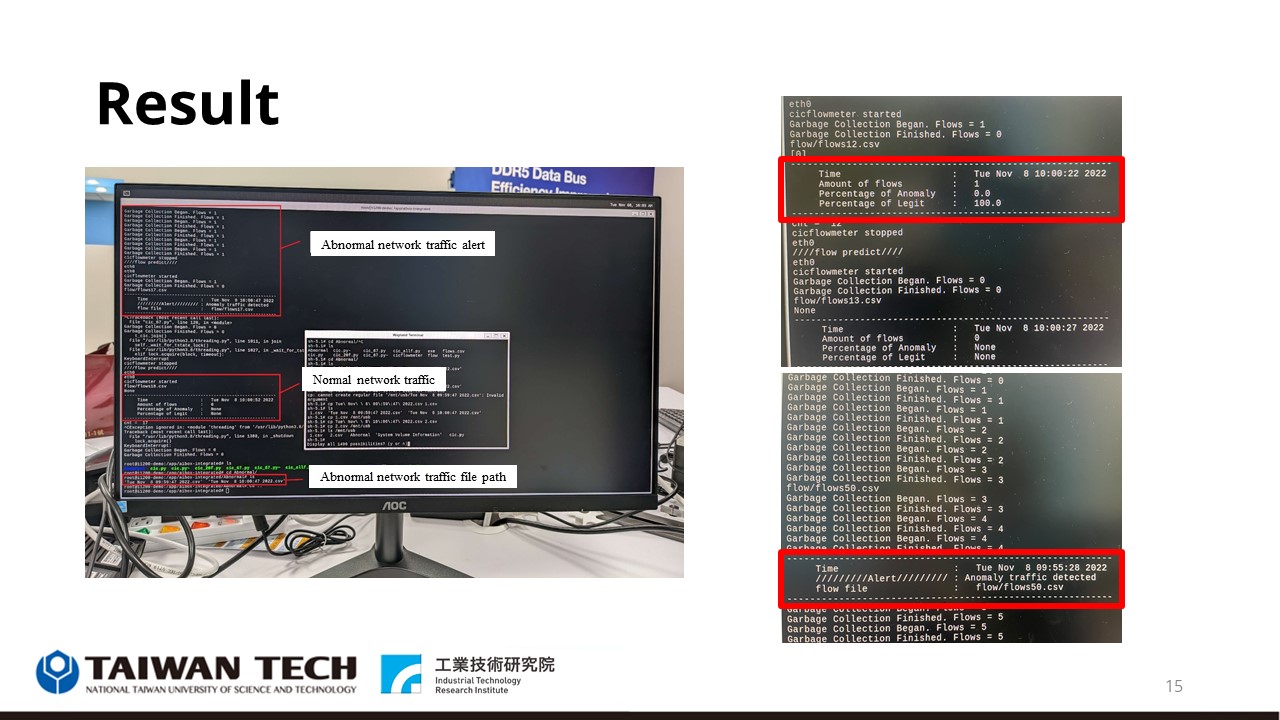 |
Before continuing, I want to recap what I have said so far. We have covered the content of network traffic capture tools, algorithms, datasets, and hardware. So now we can combine the above to complete a set of IDS for network traffic detection.
In our proposed method, IDS will be implemented in AI BOX. Its process is as shown in the figure on the left. The detection process will automatically capture network traffic and extract its features, and then perform feature preprocessing and then pass it into the model for prediction.
|
 ICACT20230167 Slide.16
[Big Slide] ICACT20230167 Slide.16
[Big Slide]
|
Chrome  Click!! Click!! |
 |
Now, it's the conclusion part |
 ICACT20230167 Slide.17
[Big Slide] ICACT20230167 Slide.17
[Big Slide]
|
Chrome  Click!! Click!! |
 |
Finally, I would like to highlight a key issue. As I mentioned before, our concern is how to implement a system that detects abnormal network traffic. To this end, we implemented IDS on AIBOX with 99% accuracy and tested to run in a real environment. |
 ICACT20230167 Slide.18
[Big Slide] ICACT20230167 Slide.18
[Big Slide]
|
Chrome  Click!! Click!! |
 |
Well, this is the end of my presentation. If you have any questions, please feel free to tell me or send me an e-mail. Thank you. |






