 |
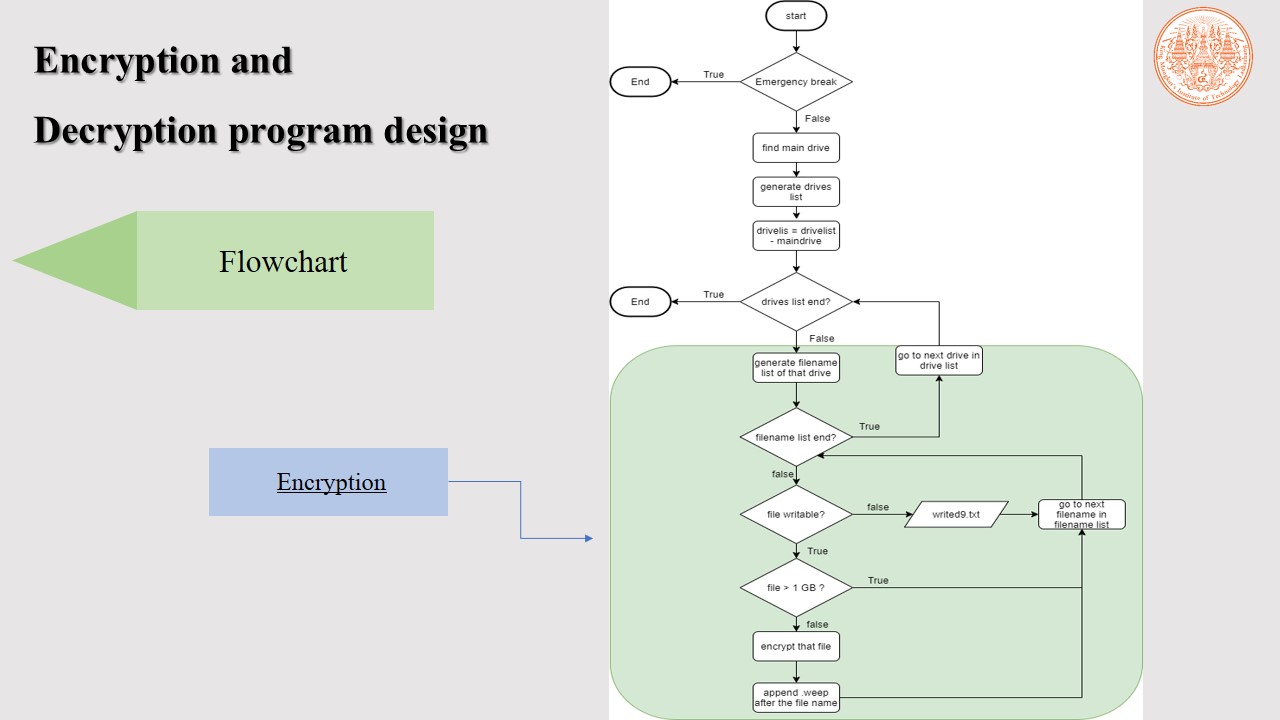
Next researcher will explain encryption and decryption program in flowchart.
Encryption program starts from do Emergency break function. It is run single time make sure the computer running encryption program is not the researcherí»s by compare the hash of researcherí»s computer name with predefined hash value because researchers doní»t want their computers to be encrypted. Next find main drive with echo %Systemroot% command. Next generate drives list the name of windows drives can be only a-z letter only so this program list it out and do encryption for all drives except maindrive. Next the program then recursively encrypt all file in file list generated by os.walk command but only encrypt files that smaller than 1 GB in size for more speed. After the encryption process is finished the program will append .weep as a encrypted file extension this helps decryption know which file was encrypted and need to be decrypted. After encrypt all file in every drives except maindrive the program then encrypt main drive but not /Windows folder and the processes in green rectangle are repeated. |
 IEEE/ICACT20210206 Slide.07
[Big Slide]
IEEE/ICACT20210206 Slide.07
[Big Slide]
 Oral Presentation
Oral Presentation 
 IEEE/ICACT20210206 Slide.07
[Big Slide]
IEEE/ICACT20210206 Slide.07
[Big Slide]
 Oral Presentation
Oral Presentation 