 |
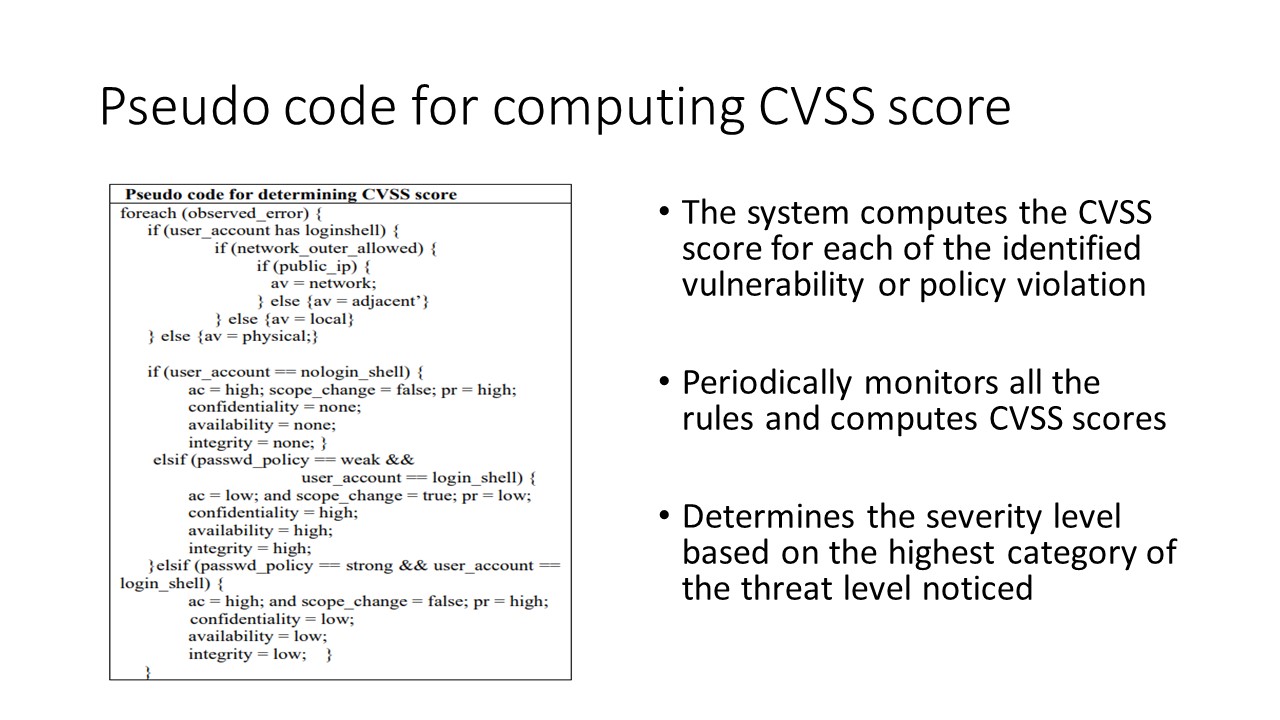
The CVSS score for each policy rule can be obtained based on the pseudo-code shown in this slide. Implementation of each control name may have a dependence on the occurrence of more than one event associated with it. For example, Process monitoring control
compliance would be verified based on various events such as
(a) Whether a process is system-oriented or network-oriented,
(b) if it is network oriented whether access restrictions are
present in the network policy or not (c) whether the log
information corresponding to the process has appropriate
access permissions or not (d) if it is network oriented whether
the process owner has ¡°nologin¡± shell or not. For each event,
the CVSS score would be computed and the highest severity
level among all the events that correspond to a control name
would become that control¡¯s severity level.
This model gives three important dimensions from which
the security assessment of the business entity can be ascertained.
Security Threat Perception of a critical resource being
monitored. (2) Strength/Weakness of the critical resource in a
particular domain in a particular control domain in accordance
with the CCM. (3) Overall compliance with the security
assessment policy framework of the business entity
considering all the critical resources.
|
 IEEE/ICACT20230046 Slide.10
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.10
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20230046 Slide.10
[Big Slide]
[YouTube]
IEEE/ICACT20230046 Slide.10
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 