 IEEE/ICACT20220314 Slide.12
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.12
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 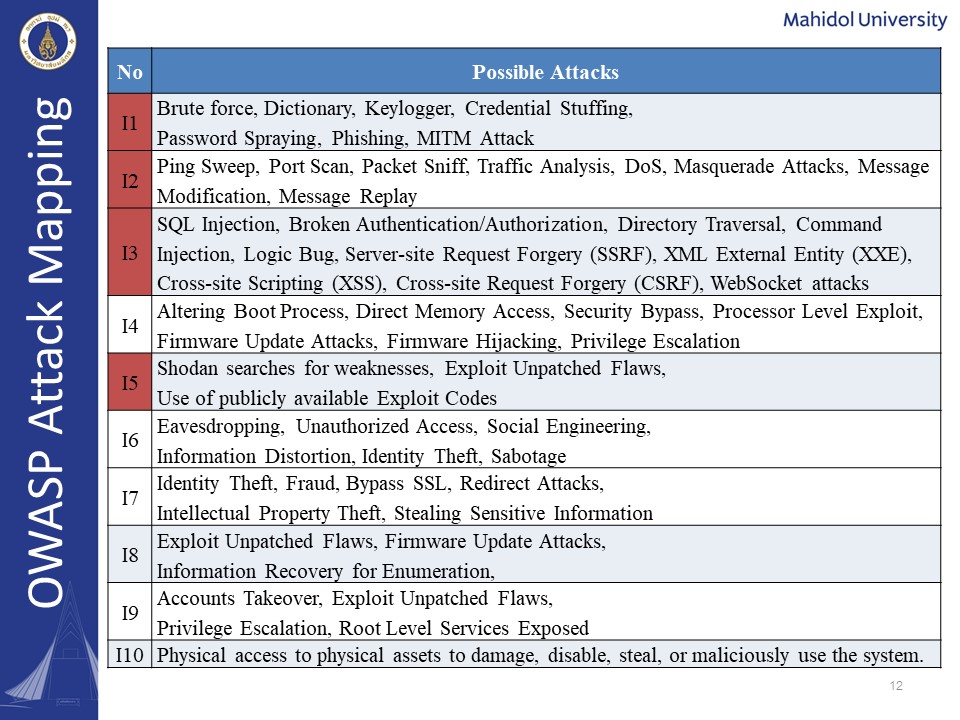
| Virual Oral Presentation Slide by Slide |
 IEEE/ICACT20220314 Slide.12
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.12
[Big Slide]
[YouTube] |
 Oral Presentation Oral Presentation |
|
 |
The OWASP IoT top 10 attack types mapping can be seen as follows: We had come up with several possible attack types for each critical security risk. In our dataset, we selected attacks from the I1, I2, I3, and I5. These attacks are: | |
| [Go to Next Slide] |