 |
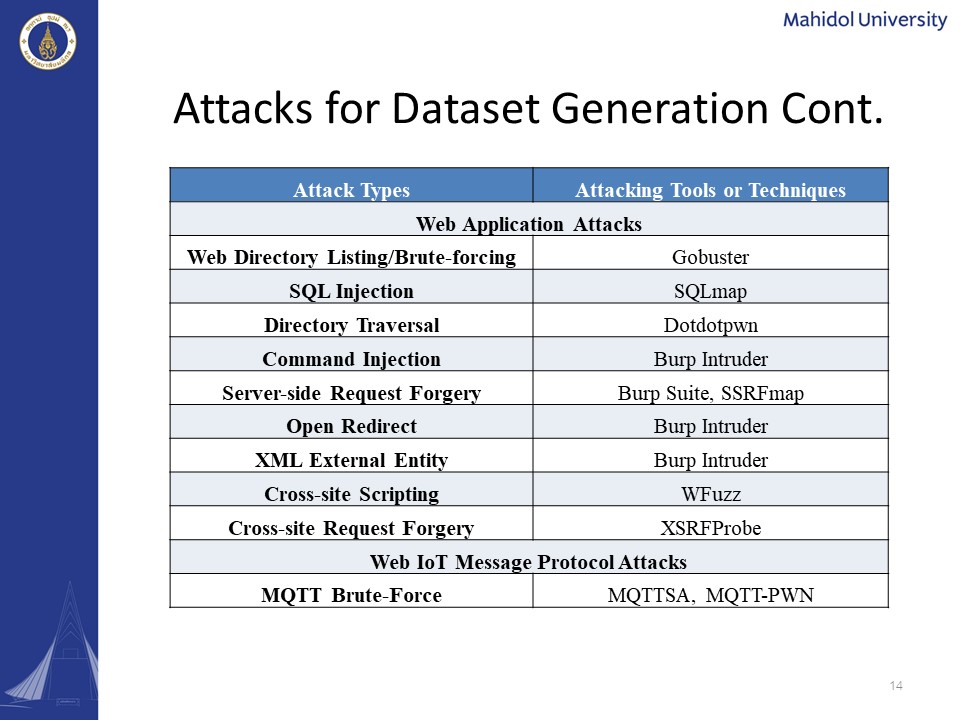
As for the web application attacks, we included the web directory brute-forcing, SQL injection, directory traversal, command injection, server-side request forgery, open redirect, XML external entity, cross-site scripting, and the cross-site request forgery. In order to generate the web application attacks, we had to use several different attacking tools such as Gobuster, sqlmap, dotdotpwn, burp intruder, Burp Suite, SSRFmap, burp intruder again, and the wfuzz and xsrf probing. And for the generation of the mqtt brute force, which is the inside the category of Web IoT message protocol attacks, we had to use mqttsa and mqttpwn attacking tools. |
 IEEE/ICACT20220314 Slide.14
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.14
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20220314 Slide.14
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.14
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 