 IEEE/ICACT20220314 Slide.17
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.17
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 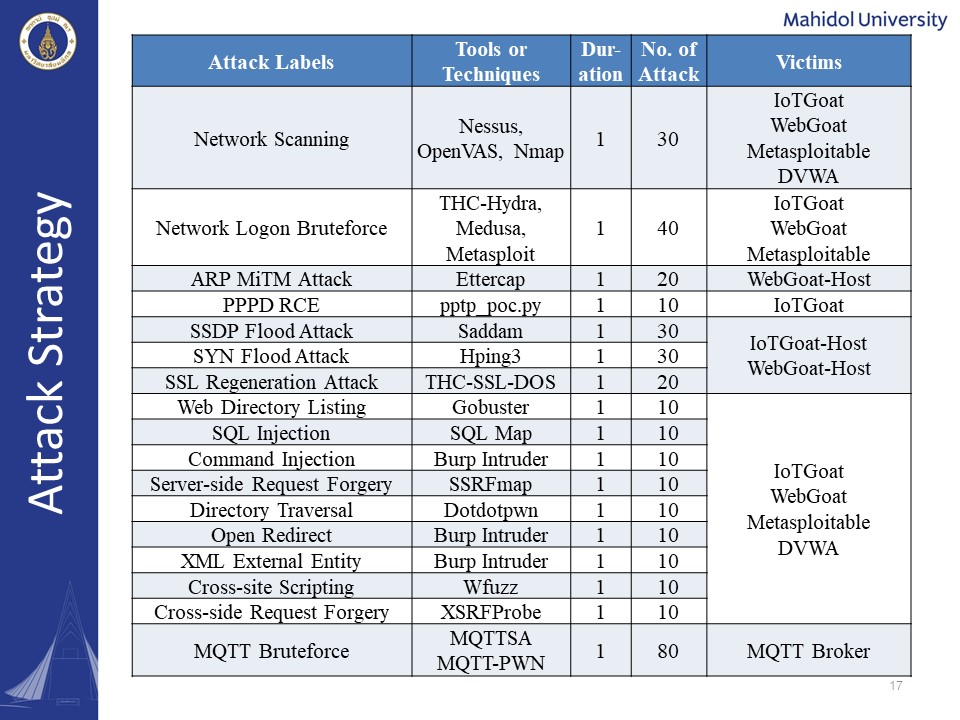
| Virual Oral Presentation Slide by Slide |
 IEEE/ICACT20220314 Slide.17
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.17
[Big Slide]
[YouTube] |
 Oral Presentation Oral Presentation |
|
 |
As for the attack strategy we simulated all of the 17 attack types for one-minute par packet capture each, using the attacking tools and techniques we have listed here. In order to have a realistic target, we have used the IoT devices and the deliberately vulnerable machines, and MQTT brokers as a victim machines. | |
| [Go to Next Slide] |