 |
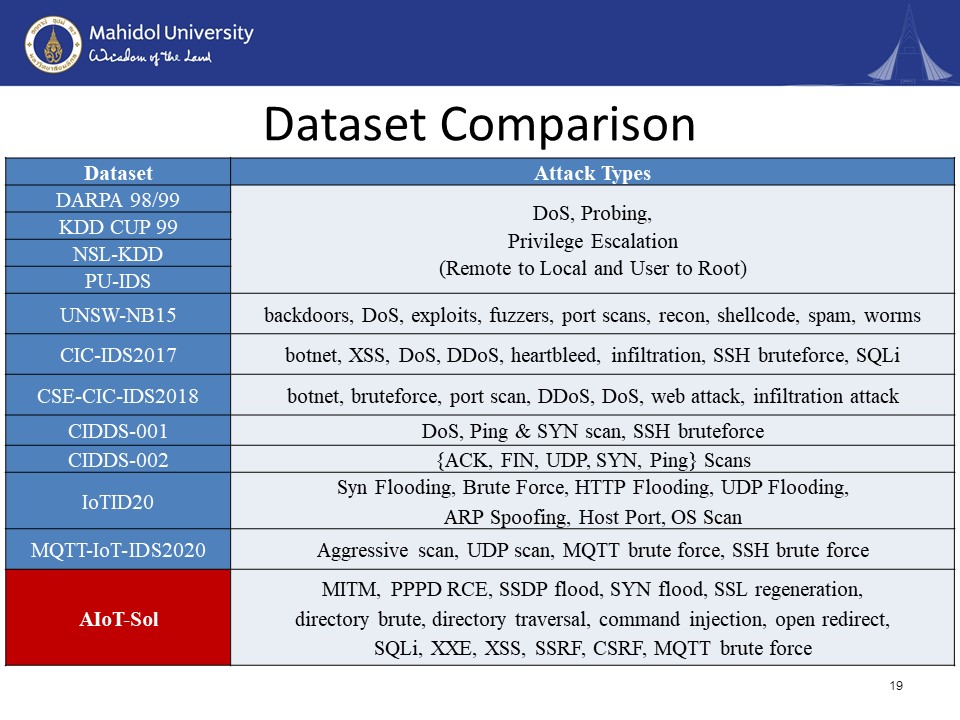
In this page, we will be presenting the comparison of our attack dataset named AIoT-Sol against the previous pre-existing attack sets. First of all, we have to compare with the datasets from the DARPA family. This family contains five attack datasets, which are the DARPA 98, DARPA 99, KDD cup 99, NSL KDD, and PUIDS. All of these DARPA family data sets contain the attack types such as DoS, Probing, Privilege Escalation from (Remote to Local and User to Root. Inside the UNSW-NB15, they contain backdoors, DoS, exploits, fuzzer, port scans, recon, shellcode, spam, worms. CIC-IDS2017 contain the botnet, XSS, DoS, DDoS, Heartbleed, infiltration, SSH bruteforce, SQL injection. The CSE-CIC-IDS2018 which is an improvement from the CIC-IDS2017, contained botnet, brute force, port scan, DDoS, DoS, web attack, infiltration attack. The CIDDS-001 and 002 contain two different types. The first one contains a Denial-of-service, Ping scan, SYN scan, and SSH brute-force. And 002 contains ACK Scan, FIN Scan, UDP Scan, SYN Scan, Ping Scan. IoTID20 includes the SYN Flooding, Brute Force, HTTP Flooding, UDP Flooding, ARP Spoofing, Host Port, OS Scan. Lastly, we have the MQTT-IoT-IDS2020. It contains Aggressive scan, UDP scan, MQTT brute force, SSH brute force. It can be seen from the comparison that our dataset contains more comprehensive attack types that actually reflect the real world. It has the MITM, PPPD RCE, SSDP flood, SYN flood, SSL regeneration, directory brute, directory traversal, command injection, open redirect, SQLi, XXE, XSS, SSRF, CSRF, MQTT brute force. |
 IEEE/ICACT20220314 Slide.19
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.19
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 
 IEEE/ICACT20220314 Slide.19
[Big Slide]
[YouTube]
IEEE/ICACT20220314 Slide.19
[Big Slide]
[YouTube]  Oral Presentation
Oral Presentation 