 ICACT20220335 Slide.15
[Big slide for presentation]
ICACT20220335 Slide.15
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
Thank you for attending this presentation and we are going to make our work open source so that any researcher who is interested in improving our work can get the benefit of our framework and dataset. You may be interested in visiting and interacting with our model at www.iotes.net
|
 ICACT20220335 Slide.14
[Big slide for presentation]
ICACT20220335 Slide.14
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
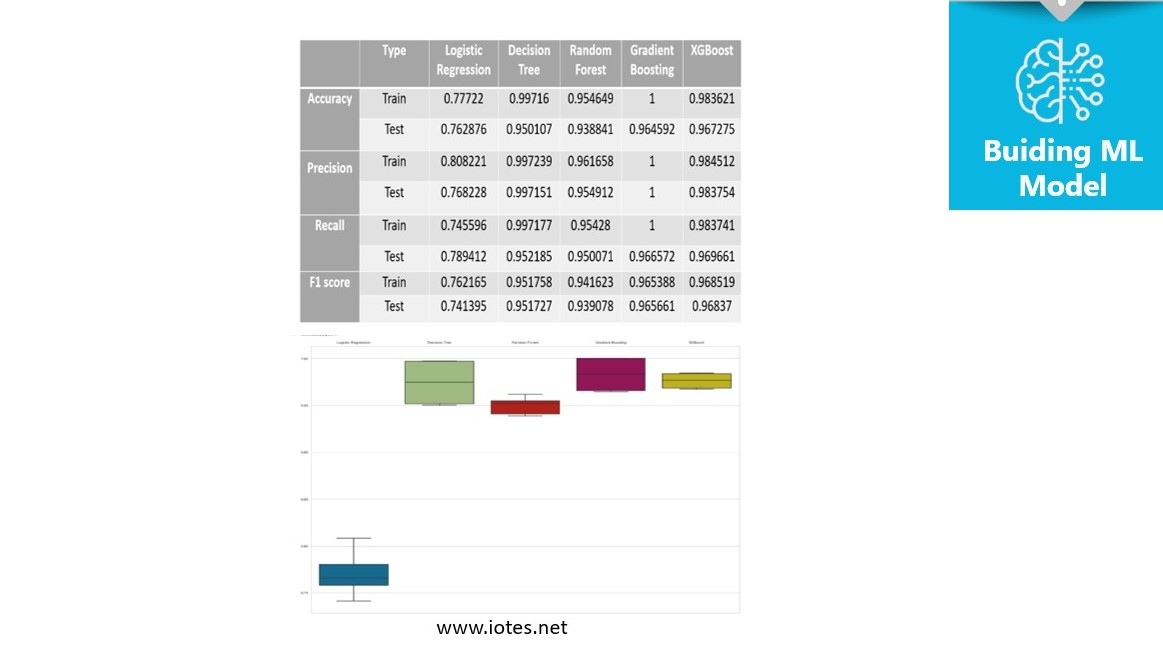 |
We deployed and compared five classification models. All tree-based models outperform the logistic regression model in terms of accuracy, precision, recall and F1 score, as demonstrated in the following table. we chose the gradient boosting model due to its high precision.
|
 ICACT20220335 Slide.13
[Big slide for presentation]
ICACT20220335 Slide.13
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
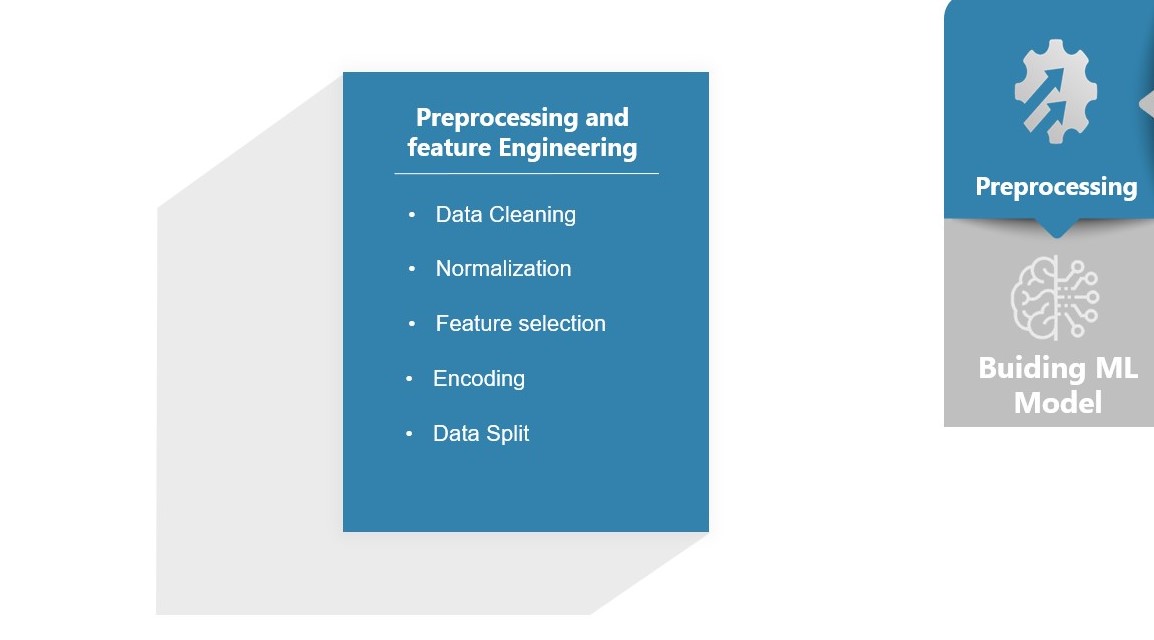 |
After analyzing the dataset we had to preprocess the dataset such as data cleaning, normalization, and encoding to make it ready for model creation.
|
 ICACT20220335 Slide.12
[Big slide for presentation]
ICACT20220335 Slide.12
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
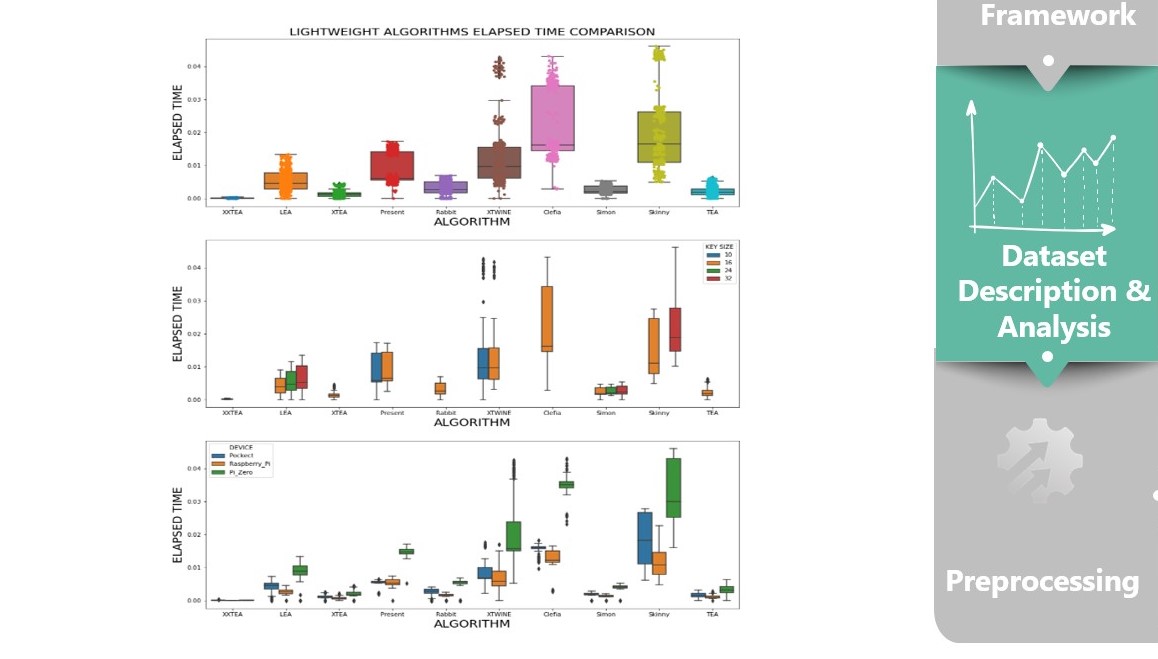 |
We have done a lot of analysis for the algorithms in different 3 classes. the slide figure is showing in example of our analysis where we analyzed the lightweight algorithms to find the slowest and the fastest algorithm.
|
 ICACT20220335 Slide.11
[Big slide for presentation]
ICACT20220335 Slide.11
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
It required more than 60 hours of testing to obtain data from all devices and all algorithms, which included a wide range of key and message sizes. Our dataset contains 37,278 data points. 12,426 data points for encryption only and the rest are for key generation and decryption. We recorded the utilized memory, CPU and elapsed time.
|
 ICACT20220335 Slide.10
[Big slide for presentation]
ICACT20220335 Slide.10
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
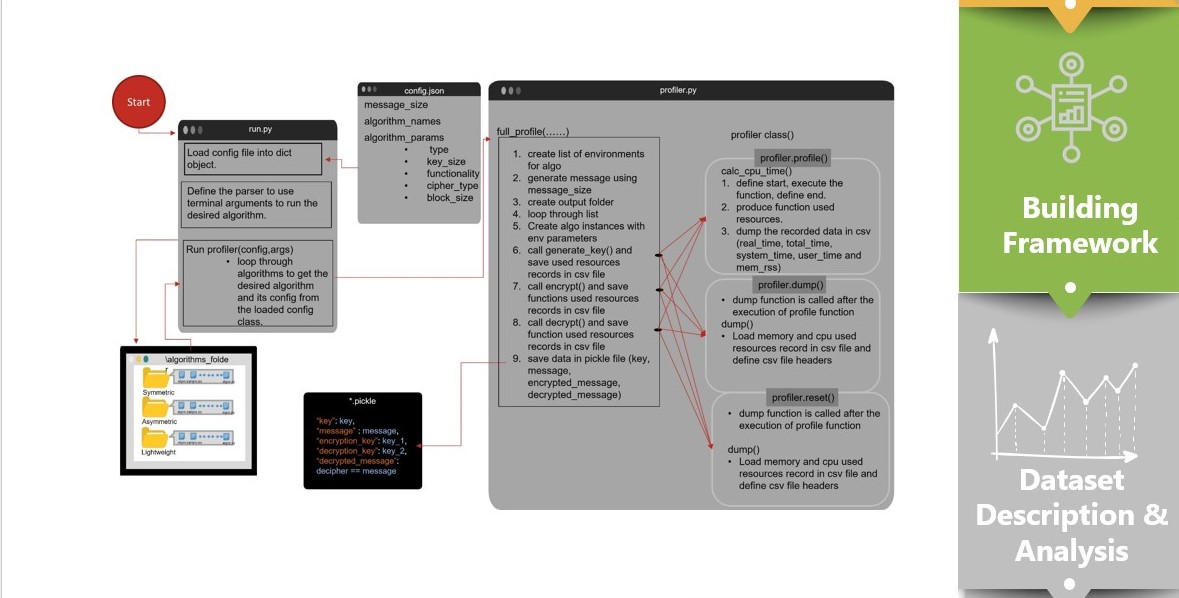 |
We created a framework to automate our experiment and collect as many as data points we can to facilitate our dataset by repeating the encryption several times.
|
 ICACT20220335 Slide.09
[Big slide for presentation]
ICACT20220335 Slide.09
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
Next we had to choose the devices for our experiment. We ultimately chose three devices: a Raspberry Pi 3 model B, a Pocket Beaglebone, and a Raspberry Pi Zero, as shown in the figure 3. All the devices run on Linux, and we chose them in this manner to facilitate data collection, since the goal was to build a single testing framework compatible with all devices.
After that, we had to choose a profiler. Many profilers were tested, including getrusage python package, which retrieves used data, and the Linux utility command ps, which displays information about current processes. Profilers¡¯ data are gathered and will be prepared for further studies throughout the analysis phase.
|
 ICACT20220335 Slide.08
[Big slide for presentation]
ICACT20220335 Slide.08
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
First, we had to decide on an encryption algorithm. The encryption algorithm must be chosen depending on the availability of python encryption repository, as we will be coding the encryption in python.
|
 ICACT20220335 Slide.07
[Big slide for presentation]
ICACT20220335 Slide.07
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
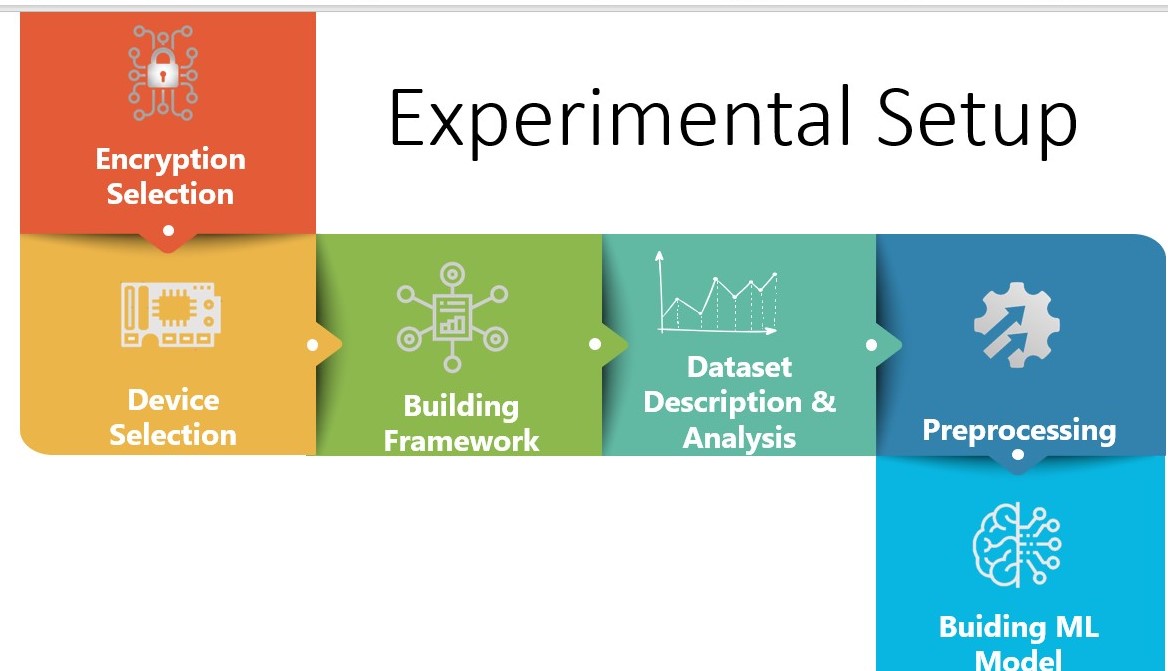 |
We designed our experiment according to the diagram in this slide, and we will go through each step in detail in the next slides.
|
 ICACT20220335 Slide.06
[Big slide for presentation]
ICACT20220335 Slide.06
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
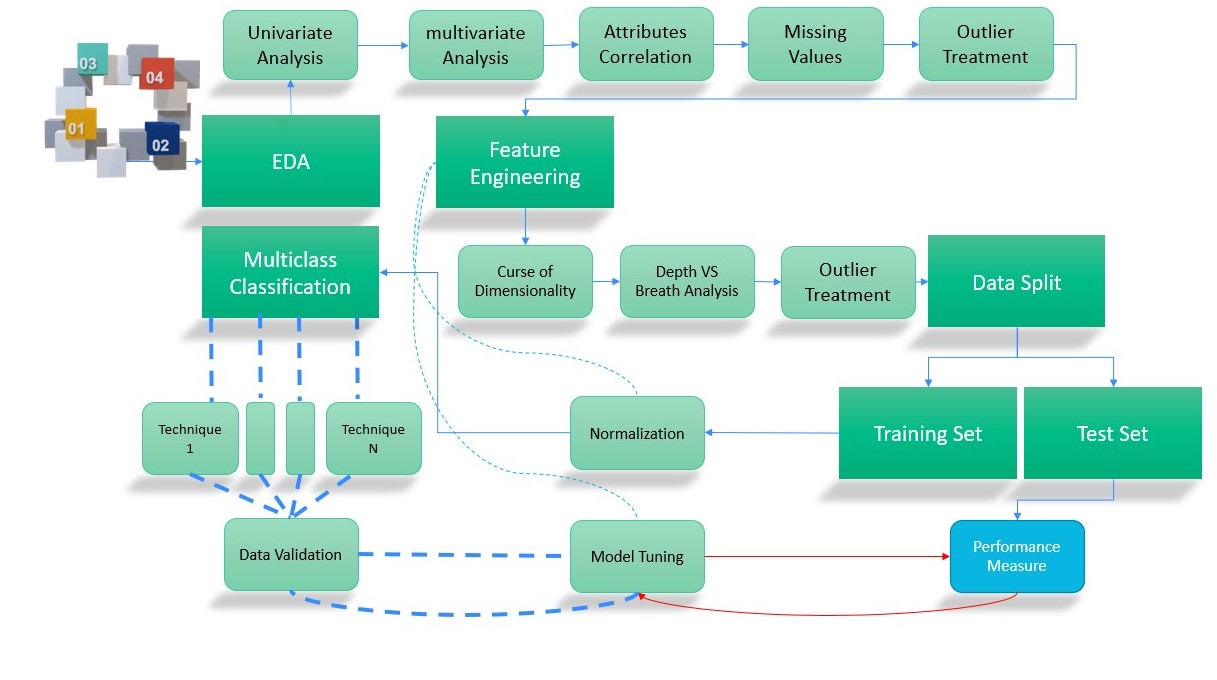 |
As previously stated, the current assistance from researchers and organizations necessitates a time-consuming and burdensome study at the device designer's conclusion. As a result, there is an urgent need for dynamic assistance that may select the most effective encryption approach for their requirements and based on their device design. Therefore, we proposed IOTES machine learning model in previous publication and in this paper we are going to share with you the steps we followed to implement it. Before IOTES model we had to find a suitable dataset in which we build the model on but unfortunately, we couldn¡¯t find therefore we decided to create a primary dataset through conducting some experiments.
|
 ICACT20220335 Slide.05
[Big slide for presentation]
ICACT20220335 Slide.05
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
Several organizations also contributed to the advancement of designer knowledge by publishing yearly guides and organizing conferences, workshops, and seminars.
|
 ICACT20220335 Slide.04
[Big slide for presentation]
ICACT20220335 Slide.04
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
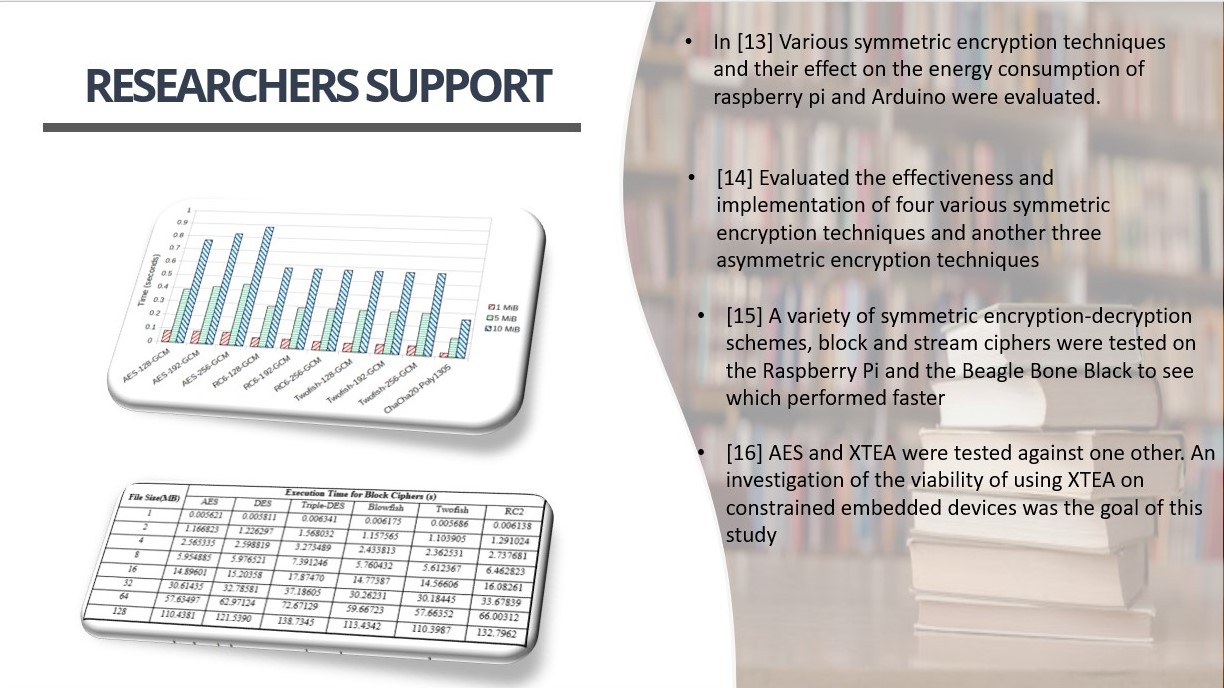 |
Because IoT developers are not spending in research due to the drop in prices, the researchers took on this obligation and continued to examine various encryption schemes on various devices, reporting their findings. All researchers' findings are presented in either tabular or graph form.
|
 ICACT20220335 Slide.03
[Big slide for presentation]
ICACT20220335 Slide.03
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
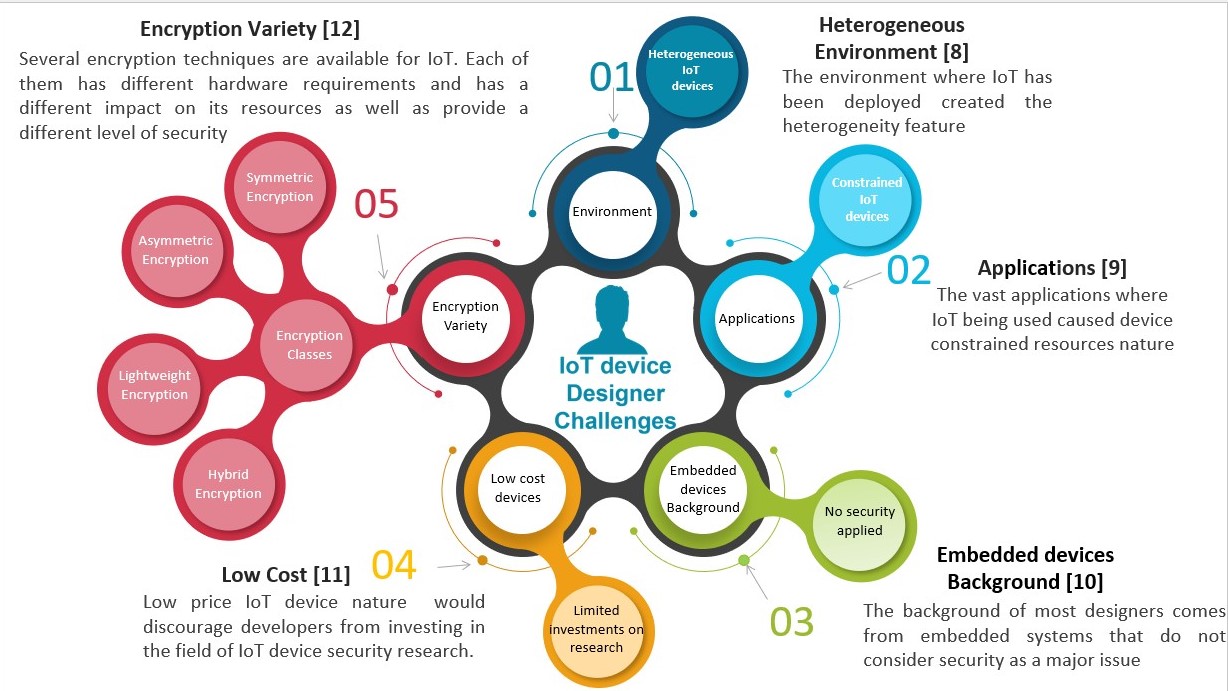 |
When we began investigating why IoT designers are unable to choose an appropriate encryption method for their device, we discovered that there are numerous reasons related to IoT itself, including the fact that IoT devices are heterogeneous and can be deployed in a wide variety of applications, resulting in a lack of standardization. Where the background of the IoT device designer is also one of the factors since they come from an embedded device background where security is not a concern due to their work in isolated systems.
Cost effectiveness is also an issue, as one sensor that cost 100,000 Euros in 1960 cost 0.002 Euros in 2010. Price declines dissuaded Internet of Things developers from investing in security research.
The range of encryption approaches classified into several classes is another reason why IoT device designers struggle to pick the appropriate encryption for their device.
|
 ICACT20220335 Slide.02
[Big slide for presentation]
ICACT20220335 Slide.02
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
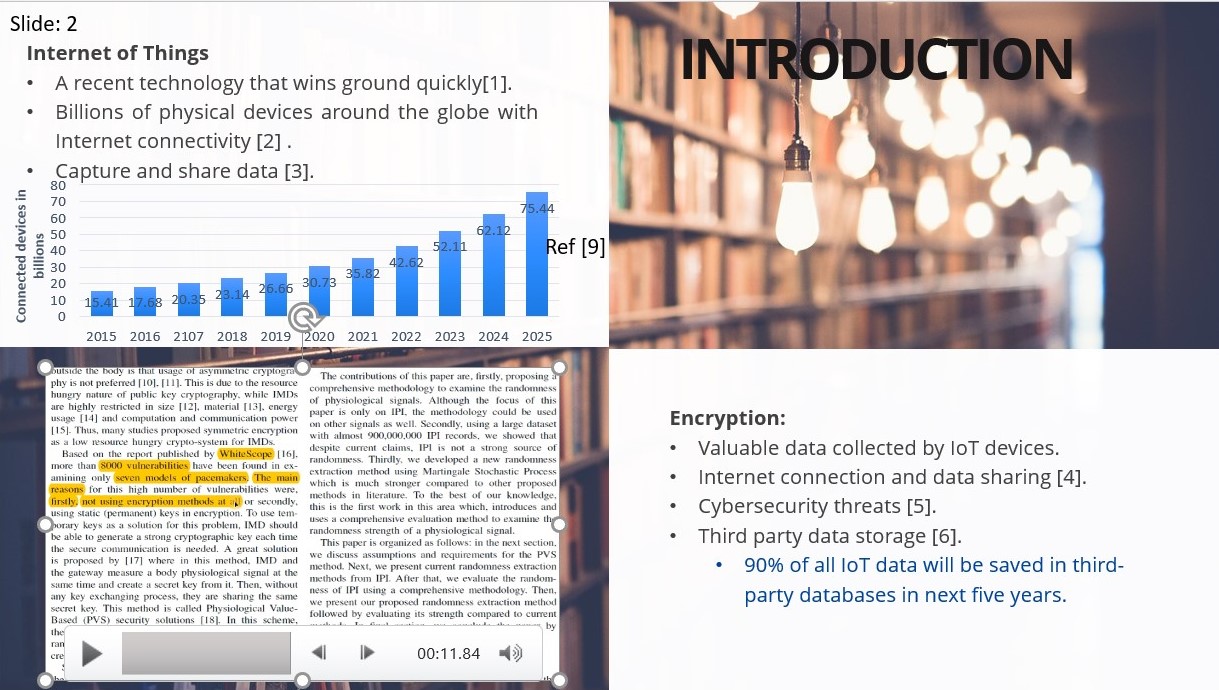 |
The Internet of Things is a rapidly emerging technology that many experts believe could eventually give a solution to many of today's society's issues, such as urbanization. Globally, the number of IoT devices is expanding every day, with studies predicting that more than 75 billion IoT devices will be connected by 2025. The data acquired by IoT devices is shared over the Internet, necessitating the use of some form of protection to safeguard it from cyber security risks. Additionally, a research indicated that over 90% of data acquired by IoT devices will be stored in third-party databases. Data encryption is critical for IoT device gathered data, as a study revealed that 8000 pacemaker devices were vulnerable to cybersecurity attacks, the primary cause being that these devices lacked encryption.
|
 ICACT20220335 Slide.01
[Big slide for presentation]
ICACT20220335 Slide.01
[Big slide for presentation]
|
Chrome Text-to-Speach Click!! Click!! |
 |
1- Hello everyone, I am glad to be present our research
IOTES (A MACHINE LEARNING MODEL) DESIGN DEPENDENT ENCRYPTION SELECTION FOR IOT DEVICES.
|






